ToolboxNew Products for IT Pros
Greg Steen
Server Administration
Windows Server 2003 Resource Kit Tools
go.microsoft.com/fwlink/?LinkId=77796
The Microsoft Windows Server 2003 Resource Kit Tools is an invaluable set of over 100 utilities that can help you streamline and automate your administrative tasks. It includes everything from Active Directory® tools to network troubleshooting utilities to CD/DVD image burners.
The Custom Reason Editor (custreasonedit.exe) is a great tool for getting your Shutdown Event Tracker organized. A component of Windows Server® 2003, the Shutdown Event Tracker logs reasons for system shutdowns to the event log. Meanwhile, the Custom Reason Editor tool lets you create a custom list with configurable parameters that will override the built-in reasons that are enabled by default. This tool can make it easy to aggregate and identify troubling processes, applications, or system states that lead to a shutdown by keeping event items logical and organized.
The DNS Resolver Tool, a command-line utility that simulates the SMTP service's execution of DNS resolution, displays messages regarding the status of the DNS query you specify as a command parameter. This utility will run on any Windows Server 2003 host with the SMTP service installed and will return error codes you can use in batch files. CDBurn.exe and DVDburn.exe are command-line utilities that let you create CDs and DVDs from ISO images and provide limited support for RW media with the /Erase switch that will clean the media before applying the new disk image. They can be used, for instance, to automate archival processes in your infrastructure.
Windows Server 2003 Resource Kit(Click the image for a larger view)
If you need to verify whether an account has been successfully locked out, the Account Lockout Status tool makes it quick and easy with both a command-line and GUI option. The tool queries every reachable domain controller and checks the status of the target user's account. Perhaps one of the best tools for automation, the Robust File Copy Utility, Robocopy.exe, gives you a variety of options for moving or copying files. This tool lets you use wildcard characters and even file attributes to specify candidates for copying, and copying can be selectively set to be recursive. You can use the tool for synchronization, and set it to delete destination files or directories that have been removed from the source directory.
Another one of my favorite utilities is the simple tool Tail (tail.exe) which, like the Linux/UNIX utility, lets you display the last N number of lines from a file, refreshing the display when new lines are added. This is great way to debug or monitor any task that writes to a log file.
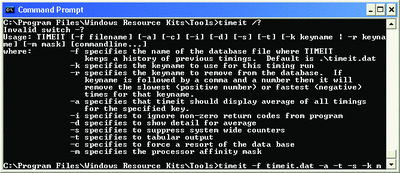
Time It (timeit.exe) lets you time commands and stores the data into its own database file letting you test how long your administrative tasks are really taking.
You should note that the tools have not been localized, having been written and tested in English only, and may "produce unpredictable results" upon execution. Be sure to test on your non-English-based systems before you use one of these utilities in a production environment.
Price: Free download.
Track Problems
ASP.NET Issue Tracker
www.ASP.NET/StarterKits/WhitePapers/Issue%20Tracker%20Whitepaper.htm
There are two things that, in my mind, always make an application better: when it's free and when it's customizable. The ASP.NET Issue Tracker, which is provided through the ASP.NET online developer community, is both of these things. Designed as a Starter Kit for learning to program Web applications under the ASP.NET 1.1 framework, Issue Tracker is a simple, but useful tool for tracking issues related to projects.
The interface is straight forward and lets you create projects, users, and issues with ease. The application supports multiple users with role-based permissions, protecting issues from unwanted eyes. You can also create custom issue categories for each project and custom data fields of various types. Tasks can be assigned a status, a priority, and a milestone, which helps organize your projects.
Another cool feature is that upon project creation, you can specify your own status codes, priorities and milestones for each project and assign an image to represent it. All the code is available in the download, so, if you have a .NET developer on hand, or can work your way through existing code, you can use the starter kit as a basis for any custom functionality you may need.
Price: Free.
Systems Monitoring
NetHealth Sentinel Professional
Network and systems monitoring are essential, and I'm always on the lookout for apps that give me insight into machine health from a distance. NetHealth Sentinel Professional, from NetHealth Systems, does just that.
An agent-based solution, Sentinel Professional gives you deep insight into monitored host machines. The application is split into four components: the Admin Server, the Admin Console, the Connection Manager, and the Remote Agent. The Admin Server executes scheduled tasks, stores configuration information, and collects alerts via the Connection Manager.
The Admin Console is the graphical interface to the Admin Server that allows you to view and configure your monitored systems as well as set up any scheduled tasks or events. The Connection Manager gathers all the data from the Remote Agents—host agents that reside on your monitored system. The Remove Agent runs as a Windows service and securely communicates to the Connection Manager via a secure connection. Each Remote Agent can be configured to send alerts to one or more Connection Managers.
NetHealth Sentinel Professional(Click the image for a larger view)
One nice feature is the aggregation of Events from all the machines on a specified monitoring group. The smooth GUI also lets you drag and drop data columns from the Event view to group by item.
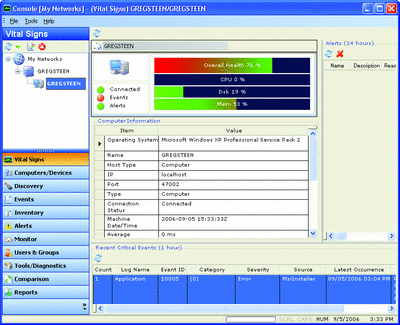
The application also offers the Vital Signs panel which gives you a quick overview of whatever statistics you would like to monitor. By default, you can see CPU, disk, and memory utilization, but you can add, via the Monitor tab, counters of your choosing.
NetHealth Sentinel Professional also includes a baselining feature that allows you to set levels for a machine's "normal" operation and then triggers alerts if operation exceeds one of those established baseline values.
Price: $495 for a 10 Client Access License pack.
Data Encryption
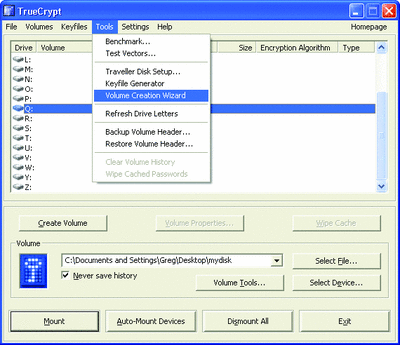
TrueCrypt
TrueCrypt, from TrueCrypt Foundation, is a free, open-source "on the fly" encryption tool that, with the correct password or encryption key, will decrypt information you are trying to read or encrypt data you are trying to write in memory, from and to your encrypted volumes. But don't worry—at no point does your volume exist in a decrypted state. Only if you have a memory dump while the application is decrypting data in memory could an aggressor find what information you are trying to protect. That can easily be avoided by turning off memory dumps on your system, not to mention that only a small portion of your data exists in memory decrypted at any one time.
The application supports both virtual volumes and physical partitions or devices. Virtual volumes, dubbed "file containers" by the authors, can be created with any file extension or have no file extension at all, so to peering eyes your sensitive data will appear to be made up of random data; there is no TrueCrypt "file signature."
TrueCrypt(Click the image for a larger view)
In addition, you can run TrueCrypt in "traveler mode" which essentially means you can create a file container on a USB key along with the application files and take your encrypted data with you wherever you go without requiring installation of the TrueCrypt application on the host system. But, by the nature of the read/write via memory, you will need administrative privileges on the system you want to use your traveler disk on.
TrueCrypt has a simple wizard to set up your traveler disk as well. This would be a great way to carry around your sys-admin information and not have to worry (as much) about eyes peering into sensitive corporate data.
For another extra level of security, TrueCrypt also lets you create a hidden volume within a file-container, so even if an intruder mounts the outer volume, he won't be able to discover that there is an inner hidden volume on the disk. Every volume is initialized with random data, making the hidden volume that resides in the outer volume "free space" very difficult to detect.
TrueCrypt can use AES, Blowfish, CAST5, Serpent, Triple DES, Twofish, and a few combinations of those algorithms to encrypt your data. The application uses the LRW mode of operation for encryption, which is to become an IEEE standard for sector-based storage encryption. For the header hashing algorithm, you can choose to use Whirlpool, SHA-1, or RIPEME-160, and the application will not store any hash on your system as an added layer of protection. The applica-tion supports FAT12, FAT16, FAT32, and NTFS file systems, but as with other Windows-based sector encryption utilities out there, it doesn't let you encrypt a Windows boot partition.
Price: Free.
Book Review
Hacking Web Services
Shreeraj Shah's Hacking Web Services (Charles River Media, 2006) is a valuable resource for those involved in development, deployment, or support of Web services. The book is a well-organized general security reference for Web services and their component technologies. And it does a good job of detailing what is involved in defending them in your infrastructure and through your development practices.
The book begins with a relatively in-depth introduction to Web services A case study titled "The Consequences of Procrastination" teaches you about the power of preemptive security procedures and the penalties of reactive systems. The chapter titled "Web Services Scanning and Enumeration" discusses how to use the wsChess, a .NET-based Web service security toolkit from Net-Square (net-square.com/wschess/index.shtml), to profile and footprint Web services.
The book includes a utility CD, which contains a sample .NET-based application called SOAPWall. This shows you how to block injection characters and buffer overflows in your .NET Web services. In addition, the CD provides demos of different types of Web service attacks.
Price: $49.95.
Shreeraj Shah's Hacking Web Services (Charles River Media, 2006) is a valuable resource for those involved in development, deployment, or support of Web services. The book is a well-organized general security reference for Web services and their component technologies. And it does a good job of detailing what is involved in defending them in your infrastructure and through your development practices.
The book begins with a relatively in-depth introduction to Web services A case study titled "The Consequences of Procrastination" teaches you about the power of preemptive security procedures and the penalties of reactive systems. The chapter titled "Web Services Scanning and Enumeration" discusses how to use the wsChess, a .NET-based Web service security toolkit from Net-Square (net-square.com/wschess/index.shtml), to profile and footprint Web services.
The book includes a utility CD, which contains a sample .NET-based application called SOAPWall. This shows you how to block injection characters and buffer overflows in your .NET Web services. In addition, the CD provides demos of different types of Web service attacks.
Price: $49.95.
Write to Toolbox
If you have a favorite tool or utility you would like to see featured here, please write to the author at tntools@microsoft.com.
The opinions expressed in this column are solely those of the author and do not necessarily reflect the opinions of Microsoft. All prices were confirmed at press time and are subject to change.
Greg Steen is a technology professional, entrepreneur, and enthusiast. He is always on the hunt for new tools and methods to help make operations and development easier for IT professionals.
© 2008 Microsoft Corporation and CMP Media, LLC. All rights reserved; reproduction in part or in whole without permission is prohibited.