The Cable GuyTroubleshooting NAP Enforcement
Joseph Davies
The new Network Access Protection (NAP) platform built into Windows Vista, Windows Server 2008, and Windows XP SP3 helps protect your private intranet by enforcing compliance with computer health requirements. Key components of NAP are NAP clients, NAP enforcement points, and NAP health policy servers.
A NAP client is a computer that can provide health status information for system health evaluation. A NAP enforcement point is a computer or network access device that uses NAP or can be used with NAP to require the evaluation of a NAP client's health state and provide restricted network access or communication. A NAP health policy server is a computer that is running Windows Server® 2008 and the Network Policy Server (NPS) service that stores health requirement policies and performs health evaluations of NAP clients. The NAP health policy server and NAP enforcement points exchange system health information and restricted access instructions with the Remote Authentication Dial-In User service (RADIUS) server and proxy messages.
In this column, I describe the components of a health requirement policy, how the NPS service processes incoming requests for NAP evaluation, and how to troubleshoot the most common issues with NAP enforcement.
Health Requirement Policies
How NAP Health Evaluation Works
The NPS service on the NAP health policy server uses the following process to perform a health evaluation:
- The NPS service compares the incoming request message to its configured set of connection request policies. For NAP, the request message should match a connection request policy that specifies that the NPS service perform the authentication and authorization locally.
- The connection request policy can also impose connection requirements. For example, for 802.1X and VPN enforcement, the connection request policy requires the use of a Protected Extensible Authentication Protocol (PEAP)-based authentication method. If the connecting client does not use PEAP, the connection request is rejected.
- The NPS service evaluates the health information in the request message, which consists of a system statement of health (SSoH) containing health status information. The NPS service passes the health status information to its installed SHVs, which return health evaluation information to the NPS service.
- The NPS service compares the request message and the health evaluation information from the SHVs to the appropriate set of network policies. The health evaluation information is compared to the Health Policy condition of NAP-based network policies. The Health Policy condition specifies the conditions for health compliance or noncompliance. The NPS service applies the first matching network policy to the request message.
- Based on the matching NAP-based network policy and its associated NAP settings, the NPS service creates a system statement of health response (SSoHR). This response includes the health evaluation information from the SHVs and indicates whether the NAP client has unlimited or restricted access and whether the NAP client should automatically attempt to remediate its health state.
- The NPS service sends a RADIUS response message with the SSoHR to the NAP enforcement point. If the client has been granted restricted access, the response message can also contain instructions that specify how the NAP client's access is restricted.
- The NAP enforcement point sends the SSoHR to the NAP client.
A health requirement policy is a combination of a connection request policy, one or more network policies, one or more health policies, and NAP settings for a NAP enforcement method. To create a health requirement policy, use the Configure NAP Wizard in the Network Policy Server snap-in. (For more information on the evaluation process, see the "How NAP Health Evaluation Works" sidebar.)
Connection Request Policies These are ordered sets of rules that allow the NPS service to determine whether an incoming connection request should be processed locally or forwarded to another RADIUS server. A NAP health policy server processes connection requests locally.
Incoming RADIUS requests from Windows®-based NAP enforcement points can contain a source tag that specifies the type of NAP enforcement point such as a Dynamic Host Configuration Protocol (DHCP) server or a virtual private network (VPN) server.
If the incoming request message contains a source tag, the NPS service on the NAP health policy server attempts to match the request against only those connection request policies with a matching source (all other connection request policies are ignored). If the incoming request message does not contain a source tag, the NPS service attempts to match the request against the connection request policies with an unspecified source (all other connection request policies that specify sources are ignored).
For example, incoming requests from a NAP-enabled DHCP server specify a source tag of DHCP. The NPS service attempts to match the requests from the DHCP server against connection request policies with the source of DHCP. Incoming requests from 802.1X-enabled switches and wireless access points do not specify a source tag. The NPS service attempts to match these requests against connection request policies without a specified source.
The connection request policy used for local or remote processing evaluation is the first matching connection request policy in the ordered list for the subset of the policies that apply to the incoming request. If the request does not match any connection request policies, the request is rejected.
Network Policies These are ordered sets of rules that specify the circumstances under which connection attempts corresponding to incoming request messages are either authorized or rejected. For each rule, there is an access permission that either grants or denies access, a set of conditions, a set of constraints, and network policy settings. If a connection is authorized, the network policy constraints and settings can specify a set of connection restrictions. For NAP, network policies can specify a health policy condition to check for health requirements and enforcement behavior settings.
Just like connection request policies, network policies use a source tag to determine which network policies to attempt to match to the incoming request. If the incoming request message contains a source tag, the NPS service attempts to match the request against only the network policies with a matching source (all other network policies are ignored). If the incoming request message does not contain a source tag, the NPS service attempts to match the request against the network policies with an unspecified source (all other network policies that specify sources are ignored).
The network policy used for authorization or health evaluation is the first matching network policy in the ordered list of subset for policies that apply to the connection attempt. If the attempt does not match any network policies, the request is rejected.
Health Policies These allow you to specify health requirements in terms of the installed system health validators (SHVs), which are used in health evaluation, and whether NAP clients must pass or fail any or all of the selected SHVs. For example, a health policy for compliant NAP clients can specify that the client must pass all health checks. A health policy for noncompliant NAP clients can specify that the client must fail at least one health check or all health checks.
Network Access Protection Settings These consist of the configuration of the SHVs installed on the NAP health policy server for health requirements and error conditions, and remediation server groups, which specify the sets of servers that are accessible to noncompliant NAP clients with restricted network access for the DHCP and VPN enforcement methods.
Scoping NAP Enforcement Problems
A logical approach is helpful when troubleshooting any problem. Some common questions to ask during troubleshooting include the following: What works? What does not work? How are the things that do and do not work related? Have the things that do not work ever worked? If so, what has changed since they last worked?
Obviously, these questions become more focused when dealing with NAP enforcement problems. Was the connection or connectivity working before the NAP enforcement method was deployed? For example, was the Internet Protocol security (IPsec) server or domain isolation working before deploying IPsec enforcement? Was 802.1X authentication working before deploying 802.1X enforcement? Was VPN remote access working before deploying VPN enforcement? Was DHCP working before deploying DHCP enforcement?
Furthermore, was a specific NAP enforcement method working before? If so, what has changed on the NAP client, NAP enforcement point, or NAP health policy server? The answers to these questions can indicate where to begin troubleshooting, possibly allowing you to isolate the component, layer, or configuration issue that is causing the problem.
For general troubleshooting of NAP enforcement problems, you need to determine the scope of the problem. The first step is to figure out whether the issue is, in fact, NAP enforcement. For IPsec enforcement, determine whether the NAP client has the correct set of IPsec policies for IPsec peer negotiation and data protection. For DHCP enforcement, find out whether the NAP client can exchange DHCP messages with a DHCP server. For 802.1X and VPN enforcement, determine if the NAP client can successfully authenticate. For example, if your VPN clients cannot perform authentication for the VPN connection, verify the authentication settings and credentials of the VPN clients.
If you have identified the problem as NAP enforcement, next determine its extent. Are all NAP clients for all NAP enforcement methods affected? Are all NAP clients for a specific enforcement method affected? Are all NAP clients for a specific enforcement method and NAP enforcement point affected? Are all NAP clients that are members of a specific group affected? Does the problem affect only a specific NAP client?
For example, if all of your NAP clients are experiencing problems for all types of NAP enforcement methods, there may be configuration issues on your NAP health policy servers. If all of your NAP clients are experiencing problems with a specific NAP enforcement method, configuration issues might exist for the Group Policy settings for NAP clients or with the health requirement policies for the specific NAP enforcement method on your NAP health policy servers. If only specific NAP clients are experiencing NAP enforcement problems, configuration issues for NAP enforcement might exist for those NAP clients.
Common NAP Enforcement Problems
NAP Resources
- Introduction to Network Access Protection
- Network Access Protection Platform Architecture
- Network Access Protection Policies in Windows Server 2008
- NPS Network Access Protection
Unlimited Access When a NAP client has unlimited access (it is not restricted), it may be because the NAP client has been evaluated as compliant by the NAP health policy server. This is exactly what you want. However, the unlimited access could also have been granted because the NAP client did not receive an SSoHR, which is what typically occurs when a health evaluation is not being performed for the NAP client. If there is no NAP health evaluation, there is no SSoHR sent back to the NAP client and the NAP client gets unlimited access.
For example, a NAP client configured for DHCP enforcement will send its SSoHR to its DHCP server. If the DHCP server running Windows Server 2008 is not configured for NAP, it won't send health evaluation request messages to a NAP health policy server. Moreover, a DHCP server running Windows Server 2008 configured for NAP that cannot reach a NAP health policy server assigns, by default, an address configuration for unlimited access.
Unlimited access may also result when the NAP health policy server does not perform a health evaluation because the incoming request matched a network policy that does not require NAP health evaluation. For information about determining the network policy that matched a NAP client's request, see the "Troubleshooting NAP Enforcement Step-by-Step" section in this column.
Restricted Access A NAP client that has restricted access has been evaluated as noncompliant by the NAP health policy server. If the NAP client has restricted access but should have unlimited access, verify the health state of the NAP client against the health policy settings corresponding to the network policy that matched the NAP client's request.
No Auto-remediation When properly configured, NAP clients can automatically remediate their health state. If NAP clients cannot auto-remediate, verify that the Enable Auto-Remediation of Client Computers checkbox is selected for the NAP Enforcement settings of the network policy that matched the NAP client's request.
Another problem that can affect auto-remediation is when the restricted NAP client cannot reach the remediation servers to download updates. For IPsec enforcement, verify that the remediation servers have the correct IPsec policy applied. For 802.1X enforcement, check the settings in the matching network policy that assign the access control list (ACL) or virtual local area network identifier (VLAN ID) and verify the configuration of the ACL or VLAN for your switches or wireless access points (APs). For VPN or DHCP enforcement, check the settings in the matching network policy for the remediation server group and ensure that all remediation servers are configured as members of the group. For DHCP enforcement, ensure that the DHCP scope options for NAP clients are configured correctly, such as the Default Gateway option value for the NAP user class.
Non-NAP-Capable Evaluation For any NAP enforcement method, verify that the corresponding enforcement client is enabled on the NAP client. For 802.1X and VPN enforcement, verify that the NAP client has system health checking for the PEAP authentication method enabled on both the connection request policy and on the NAP client (the Enable Quarantine Checks checkbox in the Protected EAP Properties dialog box is selected).
NAP Client Not Restricted but Can't Reach Intranet For IPsec enforcement, verify that the IPsec policy for compliant NAP clients and the IPsec policy of the intranet computers have a common set of negotiation and protection settings. For 802.1X enforcement, confirm that the network policy for compliant NAP clients is specifying the ACL or VLAN ID for the intranet, rather than the restricted network. Verify the configuration of the ACL or VLAN ID for the intranet on your switches or wireless APs. For VPN enforcement, make sure that there are no IP packet filters configured on the network policy for compliant NAP clients that restrict the traffic of VPN clients.
Troubleshooting NAP Enforcement Step-by-Step
One way to step your way through troubleshooting a problem with NAP enforcement for a specific NAP client is to start with the configuration of the NAP client, check the NAP client event log, and then go to the NAP health policy server to determine how the NPS service processed the request of the NAP client.
Step 1: Check the NAP Client Configuration NAP client configuration consists of Windows services, enforcement clients, and NAP enforcement-specific settings. To display NAP client status and configuration information, use the netsh nap client show state and netsh nap client show configuration commands.
Note that if NAP client settings are being provided by Group Policy, then all of your NAP client settings are specified by Group Policy and all of your local NAP client settings are ignored. In that case, use the netsh nap client show grouppolicy command to display the Group Policy-based NAP client configuration and make changes through Group Policy.
For IPsec enforcement on a computer running Windows Vista®, use the net start command to verify that the Network Access Protection Agent, IKE and AuthIP IPsec Keying Module, and IPsec Policy Agent services are started. Use the netsh nap client show configuration command to verify that the IPsec Relying Party enforcement client is enabled. If needed, use the NAP Client Configuration snap-in to enable the IPsec Relying Party enforcement client or use the netsh nap client set enforcement 79619 enabled command. Netsh nap client set enforcement commands should be run from a command prompt with elevated privileges.
For 802.1X enforcement on a computer running Windows Vista, use the net start command to verify that the Extensible Authentication Protocol, Network Access Protection Agent, Wired AutoConfig (for 802.1X enforcement on wired connections), and WLAN AutoConfig (for 802.1X enforcement on wireless connections) services are started.
Use the netsh nap client show configuration command again to verify that the EAP Quarantine enforcement client is enabled. If needed, use the NAP Client Configuration snap-in to enable the EAP Quarantine enforcement client or use the netsh nap client set enforcement 79623 enabled command. Verify that the Enable Quarantine Checks checkbox is selected for the properties of the Protected EAP authentication method for the wired or wireless connection.
For VPN enforcement on a computer running Windows Vista, use the net start command to verify that the Extensible Authentication Protocol, Network Access Protection Agent, and Remote Access Connection Manager services are started.
Use the display of the netsh nap client show configuration command to verify that the Remote Access Quarantine enforcement client is enabled. If needed, use the NAP Client Configuration snap-in to enable the Remote Access Quarantine enforcement client or use the netsh nap client set enforcement 79618 enabled command. Verify that the Enable Quarantine Checks checkbox is selected for the properties of the Protected EAP authentication method for the VPN connection.
For DHCP enforcement on a computer running Windows Vista, use the net start command to verify that the Network Access Protection Agent and DHCP Client services are started. If needed, use the Services snap-in or the Sc.exe tool to start these services and configure them for automatic startup.
Use the display of the netsh nap client show configuration command to verify that the DHCP Quarantine enforcement client is enabled. If needed, use the NAP Client Configuration snap-in to enable the DHCP Quarantine enforcement client or use the netsh nap client set enforcement 79617 enabled command.
Step 2: Check the NAP Client Event Log Use the Event Viewer snap-in to check the events in the event log created by the Network Access Protection Agent service. On computers running Windows Vista, use the Event Viewer snap-in to view events in Applications and Services Logs\Microsoft\Windows\Network Access Protection\Operational. On computers running Windows XP with SP3, use the Event Viewer snap-in to view NAP events in the System event log.
From the NAP client events, obtain the correlation ID for the NAP client health evaluation. You can use the correlation ID or the computer name of the NAP client to find the corresponding health evaluation event on the NAP health policy server. Figure 1 shows an example of an event for a non-compliant NAP client with the correlation ID.
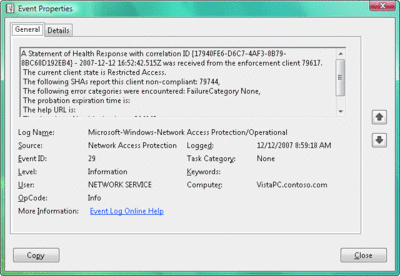
Figure 1** Example of a Windows Vista NAP client event **(Click the image for a larger view)
Step 3: Check the NPS Event Log On the NAP health policy server, use the Event Viewer snap-in to view the events in the Windows Logs\Security log that are created by the NPS service. To view NPS events, in Event viewer, open Custom Views, then Server Roles, and then click Network Policy and Access Services. To view an online help topic associated with the event, click on the "Event Log Online Help" link on the General tab of the event.
Typical NAP health evaluation events have the event ID 6278 (for unlimited access) or 6276 (for restricted access). Find the corresponding NAP health policy server event based on the computer name of the NAP client (the Account Name field in the Client Machine section of the event description) or the correlation ID (the Session Identifier field in the Quarantine Information section of the event description).
NPS event log events 6278 and 6276 contain information about the NAP health evaluation, such as the name of the matching connection request policy (the Proxy Policy Name field in the Authentication Details section of the description of the event) and the matching network policy (the Network Policy Name field in the Authentication Details section of the description of the event). Figure 2 is an example of the Details tab of an event ID 6276, with the Prefix Policy Name, the Network Policy Name, and the correlation ID (named QuarantineSessionID). This is the NAP health policy event corresponding to the Windows Vista NAP client event in Figure 1.
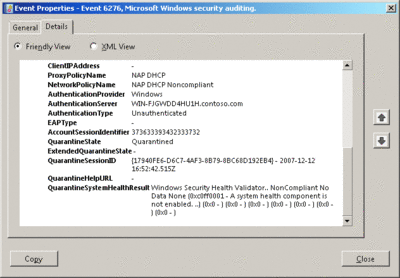
Figure 2** Example of a NAP health policy server event **(Click the image for a larger view)
If there is no event corresponding to the NAP client event, verify that the Network Policy Server service is started and that the NAP enforcement point is properly configured for NAP and to use the NAP health policy server as a RADIUS server. Verify that RADIUS messages can be sent between the NAP enforcement point and the NAP health policy server.
By following these three steps, you should be well on your way to figuring out why your NAP enforcement is not working as expected. For more information about NAP, see the "NAP Resources" sidebar.
Joseph Davies is a technical writer with Microsoft and has been teaching and writing about Windows networking topics since 1992. He has written eight books for Microsoft Press and is the author of the monthly online TechNet Cable Guy column.
© 2008 Microsoft Corporation and CMP Media, LLC. All rights reserved; reproduction in part or in whole without permission is prohibited.