Introduction to Microsoft Online Services security incident management
In cloud environments, customers and cloud service providers share the responsibility for achieving a compliant and secure computing environment. Microsoft uses a shared responsibility model to define security and operational accountability in Microsoft 365 services. While Microsoft 365 secures the underlying cloud infrastructure and services, customers need to be aware of their responsibilities for ensuring a secure tenant environment for their users and data.
Note
Microsoft Secure Score provides customers with clear analysis of their tenant configuration and makes actionable suggestions for improving security. We encourage every customer to use self-assessment tools like Microsoft Secure Score to ensure that our shared responsibilities for security and privacy are met.
At Microsoft, we use a Defense-in-Depth approach to secure our services by applying security protections at multiple layers. Defense-in-Depth provides overlapping safeguards to protect against security threats. While we build our services with security in mind, we also prepare our services for the possibility of compromise using an Assume Breach strategy. Assume Breach limits the trust placed in applications, services, identities, and networks by approaching them all—internal and external—as insecure and already compromised. The principles of Assume Breach help to limit the impact of security incidents by reducing the damage an adversary can cause and enabling rapid detection and response to security threats.
In this module, we will focus on how Microsoft Online Services investigate, manage, and respond to security threats to protect customers in the Microsoft cloud environment.
What is a security incident?
Microsoft defines a security incident in its online services as an issue that has the potential to result in a customer data breach, including violations of security policies, acceptable use policies, or standard security practices. This includes not only situations such as confirmed breaches of Microsoft systems, but also lack of compliance with Microsoft’s security policies and practices.
Whenever there is a security incident, Microsoft strives to respond quickly and effectively to protect Microsoft Online Services and customer data. Microsoft's customer notification commitments are detailed in the Microsoft Products and Services Data Protection Addendum:
If Microsoft becomes aware of a breach of security leading to the accidental or unlawful destruction, loss, alteration, unauthorized disclosure of, or access to Customer Data or Personal Data while processed by Microsoft (each a "Security Incident"), Microsoft will promptly and without undue delay (1) notify Customer of the Security Incident; (2) investigate the Security Incident and provide Customer with detailed information about the Security Incident; (3) take reasonable steps to mitigate the effects and to minimize any damage resulting from the Security Incident.
Federated incident response at Microsoft
To effectively respond to security incidents, Microsoft employs a federated security incident response model. Each major Online Service, such as Azure and Microsoft 365, has their own dedicated security teams with specialized engineering skills. At the same time, each team adheres to a shared incident management process, shared definitions, and shared training to provide consistency across all Online Services.
Each Online Service security response team provides service teams with centralized security expertise and incident response guidance as part of our federated security response model. Depending on the nature of the incident, security response and service teams may engage security partners and subject matter experts from other organizations within Microsoft for investigative assistance, such as:
- Microsoft Threat Intelligence Center – for investigative support and threat intelligence support
- Microsoft Core Engineering Digital Security & Risk Engineering – for investigative assistance with incidents involving Microsoft corporate assets and networks
- Microsoft Security Response Center – for support on externally reported vulnerabilities and Software and Services Incident Response
- Microsoft Corporate, External, Legal Affairs – for legal insight and guidance regarding security incident investigations
- Privacy teams – for guidance on regulatory requirements, compliance, and privacy. Separate teams are dedicated to each major Online Service
- Customer experience communication teams – for internal and external communications related to incidents. Separate teams are dedicated to each major Online Service
Incident response in Microsoft Online Services
Within Microsoft Online Services, responsibilities for security incident response are shared between the security response teams and each Microsoft service team. The security response teams coordinate with service teams to implement the enterprise-wide incident response strategy while leveraging service team expertise.
Our incident response strategy, which is based on the NIST 800-61 response management phases, proceeds through four phases of interconnected activity: preparation; detection and analysis; containment, eradication, and recovery; and post-incident activity.
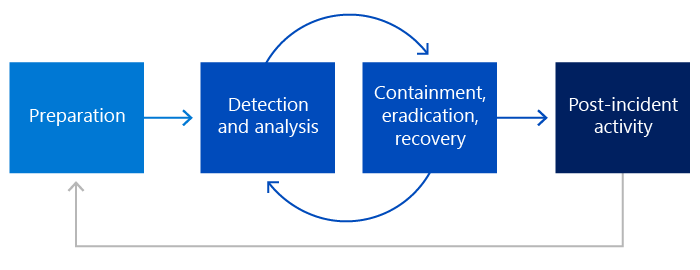
The diagram indicates that the detection and analysis and containment, eradication, and recovery phases iterate loop until the incident is resolved.
Each phase of the response management process is important for effective incident response.