Understand Firewalls
Firewalls block or allow network traffic, based on the traffic’s properties. You can utilize hardware-based firewalls or software firewalls that run on a device.
Depending on your firewall’s sophistication, you can configure it to block or allow traffic based on the:
- Traffic source address
- Traffic destination address
- Traffic source port
- Traffic destination port
- Traffic protocol
- Packet contents
For example, a sophisticated firewall analyzes network traffic and filters out harmful traffic, such as attempts to cause a denial-of-service attack or an SQL injection attack.
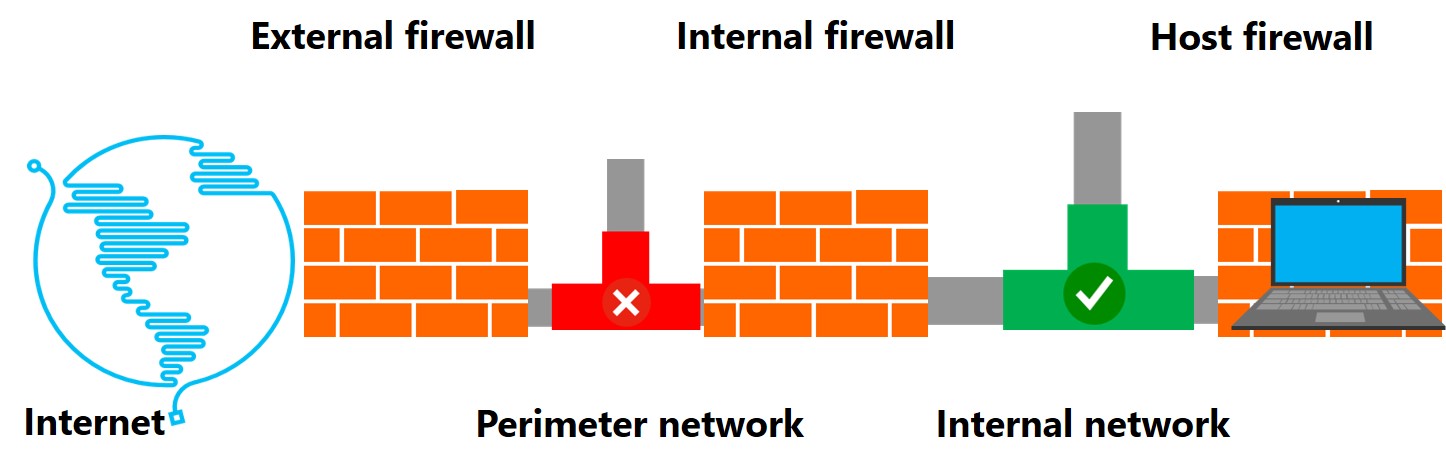
Administrators often place firewalls at a network perimeter, between an organization’s screened subnet and the Internet, and between the screened subnet and the internal network. Today, it also is common for each host to have its own additional firewall.