What is sensitive information?
Ideally, your employees would understand the importance of information protection and working within your policies. However, your employees are probably busy and not fully aware of how to help protect data. Some might handle sensitive information, such as accounting files. An employee might inadvertently upload a sensitive document that has incorrect permissions to a cloud repository. A week later, you realize that your enterprise's confidential information was leaked to competitors.
What is sensitive data?
Before learning how to help protect data, you must identify the data that requires protection. Not all data actually needs it. Nor does all data that needs it, require the same level of protection. You might want to:
- Implement strong protection methods for financial data.
- Not protect marketing materials.
- Help protect personal data so only you can access it.
- Help protect important financial data so only authorized people can access it.
The specific definition of sensitive data differs for different scenarios. However, sensitive data is essentially information that needs protection from unauthorized access. You can achieve this protection by implementing appropriate data security and information protection technologies. However, in some cases, you might also need to include physical security. An example is sensitive data in paper form. There are several useful technologies and methods to help protect sensitive data from unauthorized access or leakage.
Reasons to protect sensitive data include:
- Personal privacy
- Regulatory requirements
- Intellectual-property privacy
- Ethical or legal requirements
Consider the General Data Protection Regulation (GDPR). It primarily helps protect personal data and considers the following personal data sensitive:
- Personal information that reveals racial or ethnic origin, political opinions, and religious or philosophical beliefs.
- Trade-union memberships.
- Genetic data and biometric data that's processed solely to identify a human being.
- Health-related data.
- Data about a person’s sex life or sexual orientation.
Discover and protect sensitive data
If your organization is incorporating sensitive data protection, there are several steps you must take. It's not enough to just choose a technology to help protect data. You must properly identify sensitive data so the technology you select can actually help. Also, a consistent process for classifying data (both sensitive and nonsensitive) is imperative. Otherwise, you can't efficiently implement protection technology. Data monitoring is another important consideration. You must monitor sensitive data through its lifecycle. Otherwise, protection might not be efficient, because you don't know if it's working properly.
Data location is also important. Today, data is everywhere—on mobile devices, cloud-storage services, and local file servers. You must consider all possible locations of sensitive data. And don't forget the network paths along which it potentially travels.
The Microsoft approach to sensitive data protection consists of four phases. This approach allows you to help protect data through its entire lifecycle and across multiple locations and devices. The four phases are:
- Discover your data.
- Classify sensitive information.
- Help protect your data.
- Monitor and report on your data.
The following image depicts the Microsoft approach to information protection:
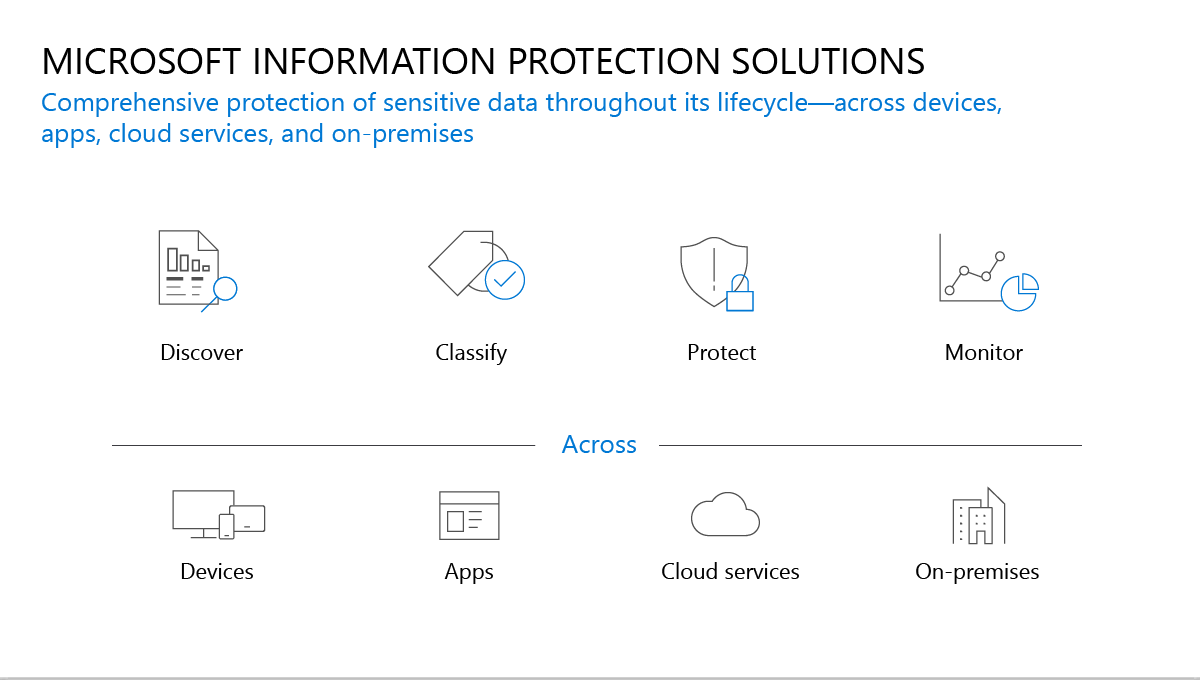
Use this approach to help ensure your sensitive data is discovered, classified, protected, and monitored. A subsequent section in this module provides more details about specific technologies that you can use to:
- Define and discover sensitive data for your specific scenario.
- Help protect data.
- Monitor data usage.