Password Hash Sync is automatically enabled during Microsoft Entra Connect Pass-through Authentication
This article can help you fix a problem in which Password Hash Synchronization is automatically enabled in Microsoft Entra connector.
Original product version: Microsoft Entra ID
Original KB number: 4051623
The following versions of Microsoft Entra Connect have issues that affect the Change user sign-in task:
- 1.1.557.0
- 1.1.558.0
- 1.1.561.0
- 1.1.614.0
These issues affect the Pass-through Authentication users who don't want to use Password Hash Synchronization.
The issues are fixed in Microsoft Entra Connect version 1.1.644.0.
Problem 1: Password Synchronization is enabled when User sign-in method is set to Pass-through Authentication
Scenario 1
- You have an existing Microsoft Entra Connect deployment that has both Password Synchronization and Pass-through Authentication disabled.
- After you enable Pass-through Authentication by using the Change user sign-in task, Password Hash Synchronization is automatically enabled.
Scenario 2
- You have an existing Microsoft Entra Connect deployment that has Password Synchronization disabled and Pass-through Authentication enabled.
- After you enable or disable the Seamless Single Sign-on option by using the Change user sign-in task, Password Hash Synchronization is automatically enabled.
Background information about this issue
- Prior to Microsoft Entra Connect version 1.1.557.0, Password Synchronization was a prerequisite for enabling Pass-through Authentication. Therefore, Password Synchronization was enabled when Pass-through Authentication was enabled.
- Because Password Synchronization is no longer required for Pass-through Authentication, we changed this process in Microsoft Entra Connect version 1.1.557.0 so that it does not enable Password Synchronization when Pass-through Authentication is enabled during a Microsoft Entra Connect installation.
- However, the same change was not applied to the Change user sign-in task. If you use the task to enable Pass-through Authentication to an existing Microsoft Entra Connect deployment, Password Synchronization is automatically enabled. This issue is fixed in Microsoft Entra Connect version 1.1.644.0 to make sure that Password Hash Synchronization remains disabled when Pass-through Authentication is enabled by using the Change user sign-in task.
Problem 2: Incorrect prompt about disabled Password Synchronization if User sign-in method is set to Pass-through Authentication
- You have an existing Microsoft Entra Connect deployment that has Password Synchronization enabled and Pass-through Authentication disabled.
- After you enable Pass-through Authentication by using the Change user sign-in task, Password Hash Synchronization remains enabled.
Background information about this issue
By design, if Password Hash Synchronization is enabled, changing the user sign-in task to any other option does not disable Password Hash Synchronization. This issue is fixed in Microsoft Entra Connect version 1.1.644.0 to prevent the display of the prompt window that states that Password Hash Synchronization is disabled.
Resolution
To resolve this issue, follow these steps:
Run Microsoft Entra Connect, and then select View current configuration. In the details pane, check whether Password synchronization is enabled on your tenant.
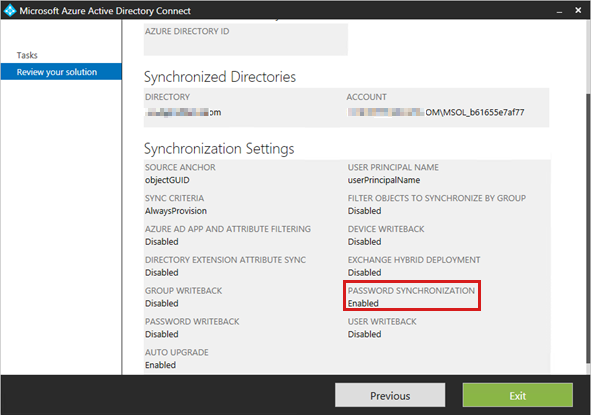
Disable the Password synchronization feature. To do this, follow these steps:
- Run Microsoft Entra Connect, and then select Configure.
- Select the Customize synchronization options task.
- On the Optional features page, clear the Password synchronization feature check box.
- Complete the wizard.
Optionally, if you want to clear password hashes that are already synchronized to Microsoft Entra ID, follow these steps:
Make sure that the Password writeback feature is disabled on your tenant. To do that, follow these steps:
- Run Microsoft Entra Connect, and then select Configure.
- Select the Customize synchronization options task.
- On the Optional features page, clear the Password writeback feature check box.
- Complete the wizard.
Use the Set-MsolUserPassword cmdlet to set random passwords on all affected users. You have to run this cmdlet five times for each user because Microsoft Entra ID stores the last four password hashes in the password hash history.
Note
Azure AD and MSOnline PowerShell modules are deprecated as of March 30, 2024. To learn more, read the deprecation update. After this date, support for these modules are limited to migration assistance to Microsoft Graph PowerShell SDK and security fixes. The deprecated modules will continue to function through March, 30 2025.
We recommend migrating to Microsoft Graph PowerShell to interact with Microsoft Entra ID (formerly Azure AD). For common migration questions, refer to the Migration FAQ. Note: Versions 1.0.x of MSOnline may experience disruption after June 30, 2024.
Note
The Set-MsolUserPassword cmdlet does not work if the user is using a federated domain. To clear password hashes for the user in the federated domain, you must change the UPN of the user to a non-federated domain, and then run the cmdlet to set the random password. After that, revert the UPN of the user to the original state.
Contact us for help
If you have questions or need help, create a support request, or ask Azure community support. You can also submit product feedback to Azure feedback community.
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for