How cutover works in Storage Migration Service
Cutover is the phase of migration that moves the network identity of the source computer to the destination computer. After cutover, the source computer will still contain the same files as before, but it won't be available to users and apps.
Summary
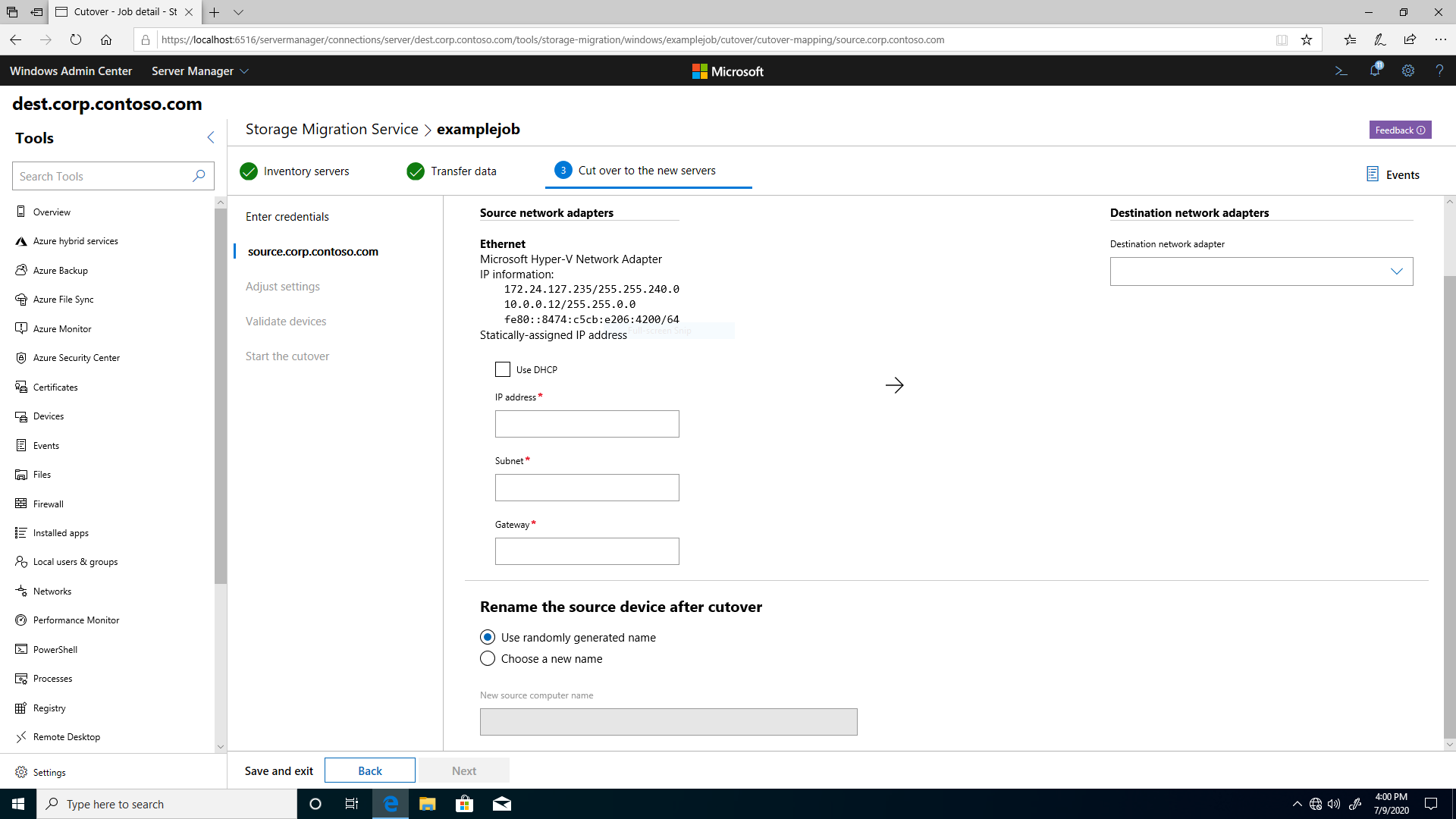 Figure 1: Storage Migration Service cutover configuration
Figure 1: Storage Migration Service cutover configuration
Before cutover starts, you provide the network configuration information needed to cut over from the source computer to the destination computer. You can also choose a new unique name for the source computer or let Storage Migration Service create a random one.
Then, Storage Migration Service takes the following steps to cut over the source computer to the destination computer:
We connect to the source and destination computers. They should both already have the following firewall rules enabled inbound:
- File and Printer Sharing (SMB-In), TCP Port 445
- Netlogon Service (NP-In), TCP Port 445
- Windows Management Instrumentation (DCOM-In), TCP Port 135
- Windows Management Instrumentation (WMI-In), TCP, Any Port
We set security permissions on the destination computer in Active Directory Domain Services to match the source computer's permissions.
We create a temporary local user account on the source computer. If the computer is domain-joined, the account username is "MsftSmsStorMigratSvc". We disable the local account token filter policy on the source computer to allow the account through, and then connect to the source computer. We make this temporary account so that when we restart and remove the source computer from the domain later, we can still access the source computer.
We repeat the previous step on the destination computer.
We remove the source computer from the domain to free up its Active Directory account, which the destination computer will later take over.
We map network interfaces on the source computer and rename the source computer.
We add the source computer back to the domain. The source computer now has a new identity and is available to admins, but not to users and apps.
On the source computer, we remove any lingering alternate computer names, remove the temporary local account we created, and re-enable the local account token filter policy.
We remove the destination computer from the domain.
We replace the IP addresses on the destination computer with the IP information provided by the source, and then rename the destination computer to the source computer's original name.
We join the destination computer back to the domain. When joined, it uses the source computer's original Active Directory computer account. This preserves group memberships and security ACLs. The destination computer now has the identity of the source computer.
On the destination computer, we remove any lingering alternate computer names, remove the temporary local account we created, and re-enable the local account token filter policy, completing cutover.
After cutover finishes, the destination computer has taken on the identity of the source computer, and you can then decommission the source computer.
Manual cutover
If cutover is failing due to an environmental condition, you can manually complete the cutover. For example, problems such as networking, custom security settings, or a third party product interaction, could all cause cutover to fail. Manually complete the cutover following these steps:
Note the step where the cutover has failed or hung. The table in Detailed stages states where specifically the cutover is in its operations.
In SMS orchestrator, run the following PowerShell command in an elevated console, where
<name>is the name of the migration job:Stop-SmsTransfer -Name <string>Manually follow the remaining steps in the previous Summary section.
a. For the Removing alternate computer names on the source step, performed when the progress is 57%, the operation is using
NETDOM COMPUTERNAME /REMOVEto remove any alternate names assigned to the source computer. Then the operation usesNETDOM COMPUTERNAME /ADDto add those old alternate names to your new destination server.b. For the following steps, there's no need to change the filter policy state unless the policy was disabled during the failed automatic cutover. To revert the policy to be enabled, delete the settings at How to disable UAC remote restrictions.
- Setting the local account token filter policy on the source computer is shown when the progress is at 13%.
- Setting the local account token filter policy on the destination computer is shown when the progress is at 25%.
- Resetting the local account token filter policy on the source computer is shown when the progress is at 61%.
- Resetting the local account token filter policy on the destination computer is shown when the progress is at 97%.
Detailed stages
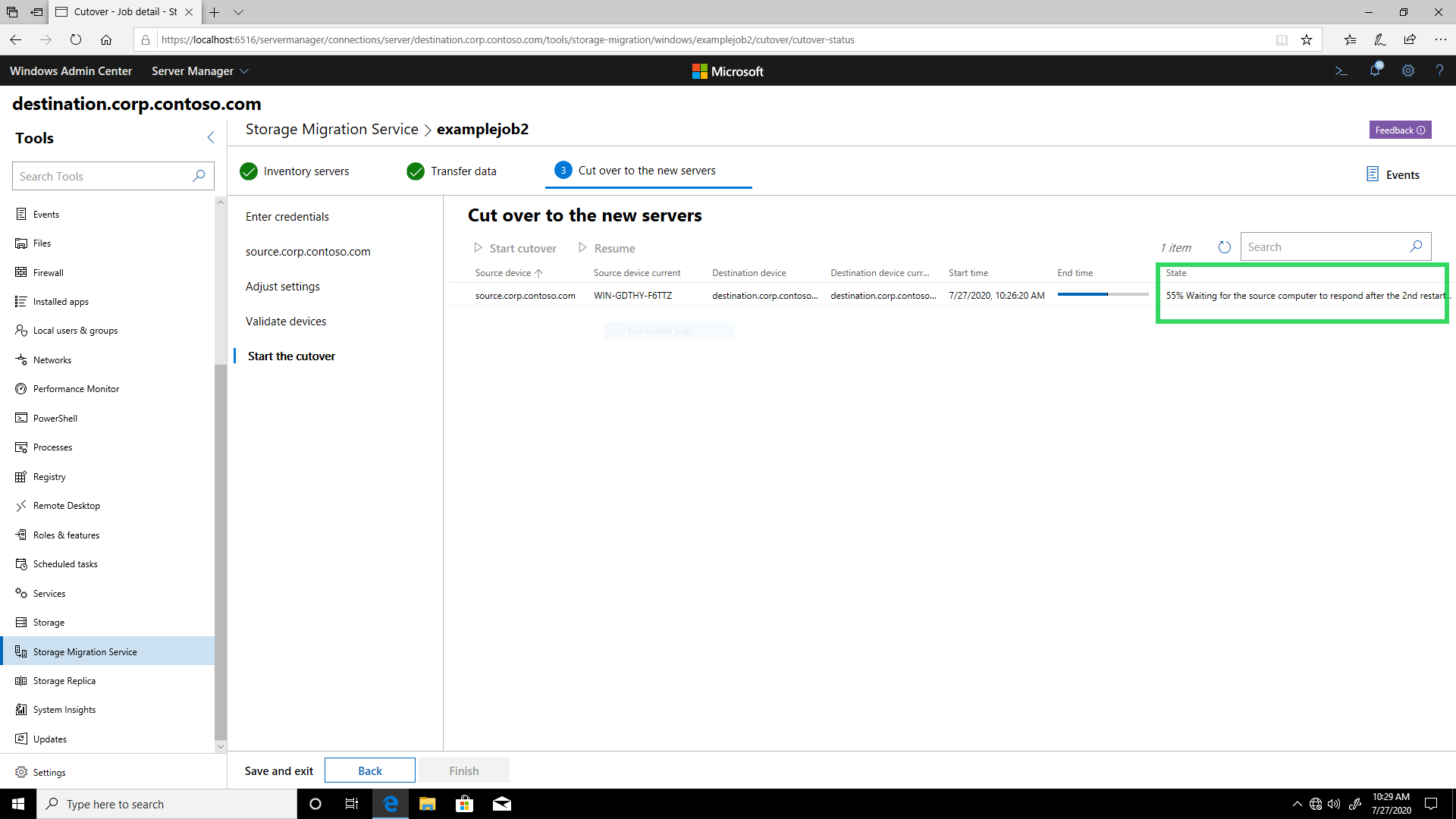 Figure 2: Storage Migration Service showing a cutover stage description
Figure 2: Storage Migration Service showing a cutover stage description
You can keep track of cutover progress through descriptions of each stage that appear as shown in figure 2. The following table shows each possible stage along with its progress, description, and any clarifying notes.
| Progress | Description | Notes |
|---|---|---|
| 0% | The cutover is idle. | |
| 2% | Connecting to the source computer... | Please ensure that the requirements for both source and destination computers are fulfilled. |
| 5% | Connecting to the destination computer... | |
| 6% | Setting security permissions on the computer object in Active Directory... | Replicates the source computer's Active Directory object security permissions on the destination computer. |
| 8% | Making sure that the temporary account that we created was successfully deleted on the source computer... | Makes sure that we can create a temporary account with the same name. |
| 11% | Creating a temporary local user account on the source computer... | If the source computer is domain-joined, the temporary account username is "MsftSmsStorMigratSvc". The password consists of 127 random unicode wide characters with letters, numbers, symbols, and case changes. If the source computer is in a workgroup, we use the original source credentials. |
| 13% | Setting the local account token filter policy on the source computer... | Disables the policy so that we can connect to the source when it's not joined to the domain. Learn more about the local account token filter policy here. |
| 16% | Connecting to the source computer using the temporary local user account... | |
| 19% | Making sure that the temporary account that we created was successfully deleted on the destination computer... | |
| 22% | Creating a temporary local user account on the destination computer... | If the destination computer is domain-joined, the temporary account username is "MsftSmsStorMigratSvc". The password consists of 127 random unicode wide characters with letters, numbers, symbols, and case changes. If the destination computer is in a workgroup, we use the original destination credentials. |
| 25% | Setting the local account token filter policy on the destination computer... | Disables the policy so that we can connect to the destination when it's not joined to the domain. Learn more about the local account token filter policy here. |
| 27% | Connecting to the destination computer using the temporary local user account... | |
| 30% | Removing the source computer from the domain... | |
| 31% | Collecting the source computer IP addresses. | Applies only to Linux source computers. |
| 33% | Restarting the source computer... (1st restart) | |
| 36% | Waiting for the source computer to respond after the 1st restart... | Likely to become unresponsive if the source computer isn't covered by a DHCP subnet, but you selected DHCP during network configuration. |
| 38% | Mapping network interfaces on the source computer... | |
| 41% | Renaming the source computer... | |
| 42% | Restarting the source computer... (1st restart) | Applies only to Linux source computers. |
| 43% | Restarting the source computer... (2nd restart) | Applies only to domain-joined Windows Server 2003 source computers. |
| 43% | Waiting for the source computer to respond after the 1st restart... | |
| 43% | Waiting for the source computer to respond after the 2nd restart... | |
| 44% | Adding the source computer to the domain... | |
| 47% | Restarting the source computer... (1st restart) | |
| 50% | Restarting the source computer... (2nd restart) | |
| 51% | Restarting the source computer... (3rd restart) | Applies only to Windows Server 2003 source computers. |
| 52% | Waiting for the source computer to respond... | |
| 52% | Waiting for the source computer to respond after the 1st restart... | |
| 55% | Waiting for the source computer to respond after the 2nd restart... | |
| 56% | Waiting for the source computer to respond after the 3rd restart... | |
| 57% | Removing alternate computer names on the source... | Ensures that the source is unreachable to other users and apps. For more info, see Netdom computername. |
| 58% | Removing a temporary local account we created on the source computer... | |
| 61% | Resetting the local account token filter policy on the source computer... | Enables the policy. |
| 63% | Removing the destination computer from the domain... | |
| 66% | Restarting the destination computer... (1st restart) | |
| 69% | Waiting for the destination computer to respond after the 1st restart... | |
| 72% | Mapping network interfaces on destination computer... | Maps each network adapter and IP address from the source computer onto the destination computer, replacing the destination's network information. |
| 75% | Renaming the destination computer... | |
| 77% | Adding the destination computer to the domain... | The destination computer takes over the old source computer's Active Directory object. This can fail if the destination user isn't a member of Domain Admins or doesn't have admin rights to the source computer Active Directory object. You can specify alternate destination credentials in the "Enter credentials" step before cutover starts. |
| 80% | Restarting the destination computer... (1st restart) | |
| 83% | Restarting the destination computer... (2nd restart) | |
| 84% | Waiting for the destination computer to respond... | |
| 86% | Waiting for the destination computer to respond after the 1st restart... | |
| 88% | Waiting for the destination computer to respond after the 2nd restart... | |
| 91% | Waiting for the destination computer to respond with the new name... | May take a long time due to Active Directory and DNS replication. |
| 93% | Removing alternate computer names on the destination... | Ensures that the destination name has been replaced. |
| 94% | Removing a temporary local account we created on the destination computer... | |
| 97% | Resetting the local account token filter policy on the destination computer... | Enables the policy. |
| (100%) | Succeeded |
FAQ
Is domain controller migration supported?
Not currently, but see the FAQ page for a workaround.
Known issues
Ensure that you have fulfilled the requirements from the Storage Migration Service overview and installed the latest Windows update on the computer running Storage Migration Service.
See the known issues page for more information on the following issues.
Cutover hangs on "38% Mapping network interfaces on the source computer..." when using static IPs
Cutover hangs on "38% Mapping network interfaces on the source computer..."
Additional References
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for