Register mobile apps that call web APIs
This article contains instructions to help you register a mobile application that you're creating.
Supported account types
The account types that your mobile applications support depend on the experience that you want to enable and the flows that you want to use.
Audience for interactive token acquisition
Most mobile applications use interactive authentication. If your app uses this form of authentication, you can sign in users from any account type.
Audience for integrated Windows authentication, username-password, and B2C
If you have a Universal Windows Platform (UWP) app, you can use integrated Windows authentication (IWA) to sign in users. To use IWA or username-password authentication, your application needs to sign in users in your own line-of-business (LOB) developer tenant. In an independent software vendor (ISV) scenario, your application can sign in users in Microsoft Entra organizations. These authentication flows aren't supported for Microsoft personal accounts.
You can also sign in users by using social identities that pass a B2C authority and policy. To use this method, you can use only interactive authentication and username-password authentication. Username-password authentication is currently supported only on Xamarin.iOS, Xamarin.Android, and UWP.
For more information, see Scenarios and supported authentication flows and Scenarios and supported platforms and languages.
Platform configuration and redirect URIs
Interactive authentication
When you build a mobile app that uses interactive authentication, the most critical registration step is the redirect URI. This experience enables your app to get single sign-on (SSO) through Microsoft Authenticator (and Intune Company Portal on Android). It also supports device management policies.
Sign in to the Microsoft Entra admin center as at least an Application Developer.
Browse to Identity > Applications > App registrations.
Select New registration.
Enter a Name for the application.
For Supported account types, select Accounts in this organizational directory only.
Select Register.
Select Authentication and then select Add a platform.
When the list of platforms is supported, select iOS / macOS.
Enter your bundle ID, and then select Configure.
When you complete the steps, the redirect URI is computed for you, as in the following image.
If you prefer to manually configure the redirect URI, you can do so through the application manifest. Here's the recommended format for the manifest:
- iOS:
msauth.<BUNDLE_ID>://auth- For example, enter
msauth.com.yourcompany.appName://auth
- For example, enter
- Android:
msauth://<PACKAGE_NAME>/<SIGNATURE_HASH>- You can generate the Android signature hash by using the release key or debug key through the KeyTool command.
Username-password authentication
Tip
Steps in this article might vary slightly based on the portal you start from.
If your app uses only username-password authentication, you don't need to register a redirect URI for your application. This flow does a round trip to the Microsoft identity platform. Your application won't be called back on any specific URI.
However, identify your application as a public client application. To do so:
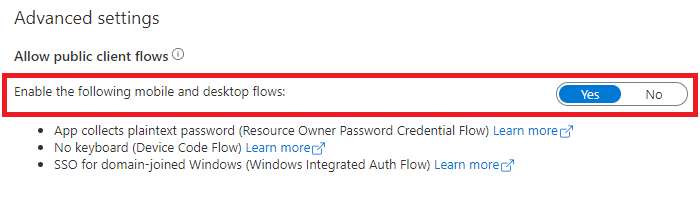
Still in the Microsoft Entra admin center, select your app in App registrations, and then select Authentication.
In Advanced settings > Allow public client flows > Enable the following mobile and desktop flows:, select Yes.
API permissions
Mobile applications call APIs for the signed-in user. Your app needs to request delegated permissions. These permissions are also called scopes. Depending on the experience that you want, you can request delegated permissions statically through the Azure portal. Or you can request them dynamically at runtime.
By statically registering permissions, you allow administrators to easily approve your app. Static registration is recommended.
Next steps
Move on to the next article in this scenario, App code configuration.
Tagasiside
Varsti tulekul: 2024. aasta jooksul tühistame GitHubi probleemide funktsiooni sisutagasiside mehhanismina ja asendame selle uue tagasisidesüsteemiga. Lisateabe saamiseks vt https://aka.ms/ContentUserFeedback.
Esita ja vaata tagasisidet



