Data security dashboard
Microsoft Defender for Cloud's data security dashboard provides an interactive view of significant risks to sensitive data. It prioritizes alerts and potential attack paths across multicloud data resources, making data protection management more effective.
With the data security dashboard you can:
- Easily locate and summarize sensitive data resources in your cloud data estate.
- Identify and prioritize data resources at risk to prevent and respond to sensitive data breaches.
- Investigate active high severity threats that lead to sensitive data.
- Explore potential threats data by highlighting attack paths that lead to sensitive data.
- Explore useful data insights by highlighting useful data queries in the security explorer.
To access the data security dashboard in Defender for Cloud, select Data Security.
Prerequisites
To view the dashboard:
- You must enable Defender CSPM.
- Enable sensitive data discovery within the Defender CSPM plan.
To receive the alerts for data sensitivity:
- You must enable Defender for Storage.
Required permissions and roles
Permissions:
- Microsoft.Security/assessments/read
- Microsoft.Security/assessments/subassessments/read
- Microsoft.Security/alerts/read
Role - the minimum required privileged role-based access control role of Security explorer.
- Register each relevant Azure subscription to the Microsoft.Security resource provider.
Note
The data security dashboard feature is turned on at the subscription level.
Data security overview section
The data security overview section provides a general overview of your cloud data estate, per cloud, including all data resources, divided into storage assets, managed databases, and hosted databases (IaaS).
Coverage status - displays the limited data coverage for resources without Defender CSPM workload protection:
- Covered – resources that have the necessary Defender CSPM, or Defender for Storage, or Defender for Databases enabled.
- Partially covered – missing either the Defender CSPM, Defender for Storage, or Defender for Storage plan. Select the tooltip to present a detailed view of what is missing.
- Not covered - resources that aren't covered by Defender CSPM, or Defender for Storage, or Defender for Databases.
Sensitive resources – displays how many resources are sensitive.
- Sensitive resources requiring attention - displays the number of sensitive resources that have either high severity security alerts or attack paths.
Top issues
The Top issues section provides a highlighted view of top active and potential risks to sensitive data.
Sensitive data resources with high severity alerts - summarizes the active threats to sensitive data resources and which data types are at risk.
Sensitive data resources in attack paths - summarizes the potential threats to sensitive data resources by presenting attack paths leading to sensitive data resources and which data types are at potential risk.
Data queries in security explorer - presents the top data-related queries in security explorer that helps focus on multicloud risks to sensitive data.
Closer look
The Closer look section provides a more detailed view into the sensitive data within the organization.
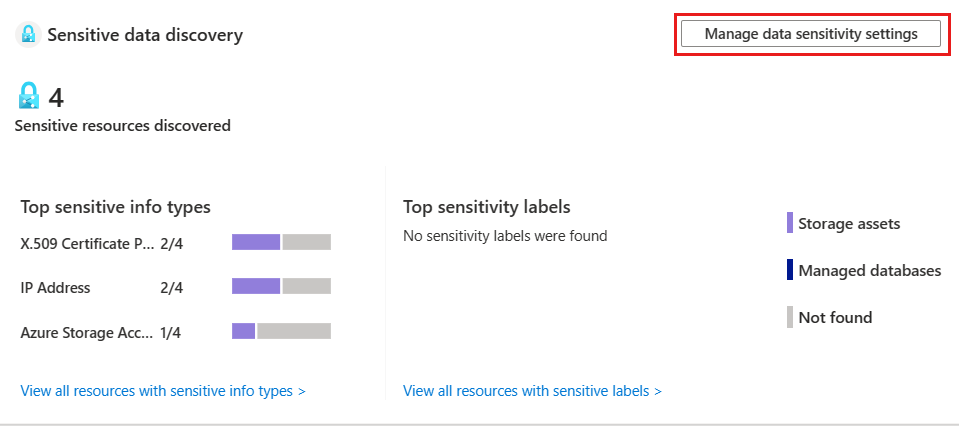
Sensitive data discovery - summarizes the results of the sensitive resources discovered, allowing customers to explore a specific sensitive information type and label.
Internet-exposed data resources - summarizes the discovery of sensitive data resources that are internet-exposed for storage and managed databases.
You can select the Manage data sensitivity settings to get to the Data sensitivity page. The Data sensitivity page allows you to manage the data sensitivity settings of cloud resources at the tenant level, based on selective info types and labels originating from the Purview compliance portal, and customize sensitivity settings such as creating your own customized info types and labels, and setting sensitivity label thresholds.
Next steps
- Learn more about data security posture management.
- Learn how to enable Defender CSPM.