אירוע
9 באפר׳, 15 - 10 באפר׳, 12
קוד העתיד עם בינה מלאכותית והתחברות לעמיתים ומומחים של Java ב- JDConf 2025.
הירשם כעתהדפדפן הזה אינו נתמך עוד.
שדרג ל- Microsoft Edge כדי לנצל את התכונות, עדכוני האבטחה והתמיכה הטכנית העדכניים ביותר.
In this article, you'll learn how to integrate Veracode with Microsoft Entra ID. When you integrate Veracode with Microsoft Entra ID, you can:
To get started, you need the following items:
In this article, you configure and test Microsoft Entra SSO in a test environment. Veracode supports identity provider initiated SSO and just-in-time user provisioning.
To configure the integration of Veracode into Microsoft Entra ID, add Veracode from the gallery to your list of managed SaaS apps.
Alternatively, you can also use the Enterprise App Configuration Wizard. In this wizard, you can add an application to your tenant, add users/groups to the app, assign roles, as well as walk through the SSO configuration as well. Learn more about Microsoft 365 wizards.
Configure and test Microsoft Entra SSO with Veracode by using a test user called B.Simon. For SSO to work, you must establish a link between a Microsoft Entra user and the related user in Veracode.
To configure and test Microsoft Entra SSO with Veracode, perform the following steps:
Follow these steps to enable Microsoft Entra SSO.
In the Microsoft Entra ID navigate to the Veracode application page under Enterprise Applications, scroll down to the Manage section, and click on single sign-on.
Again under the Manage tab, click on Single sign-on, then select SAML.
On the Set up single sign-on with SAML page, select the pencil icon for Basic SAML Configuration to edit the settings.
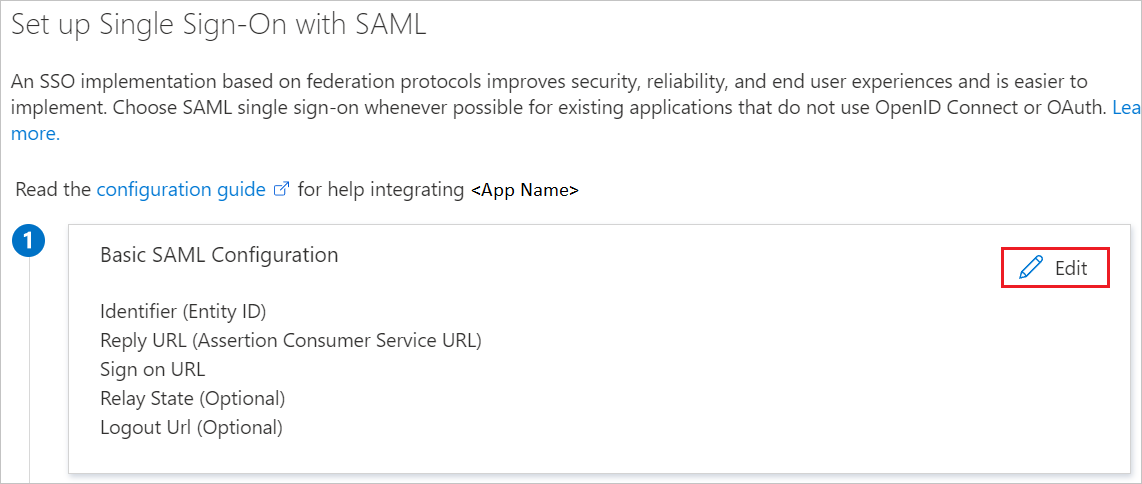
The Relay state field should be autopopulated with https://web.analysiscenter.veracode.com/login/#/saml. The rest of these fields will populate after setting up SAML within the Veracode Platform.
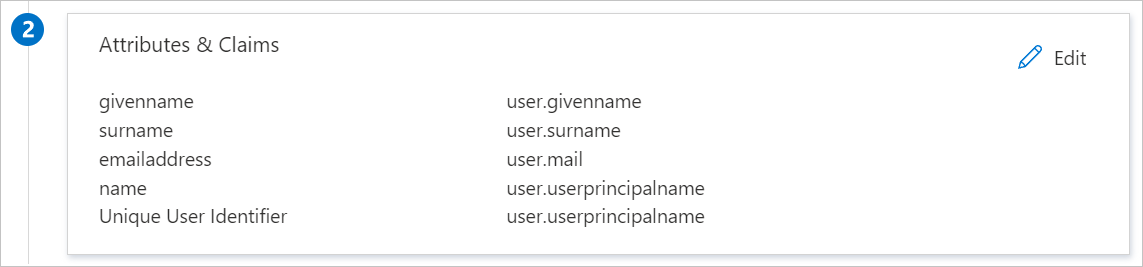
On the Set up single sign-on with SAML page, in the SAML Signing Certificate section, find Certificate (Base64). Select Download to download the certificate and save it on your computer.
Veracode expects the SAML assertions in a specific format, which requires you to add custom attribute mappings to your SAML token attributes configuration. The following screenshot shows the list of default attributes.
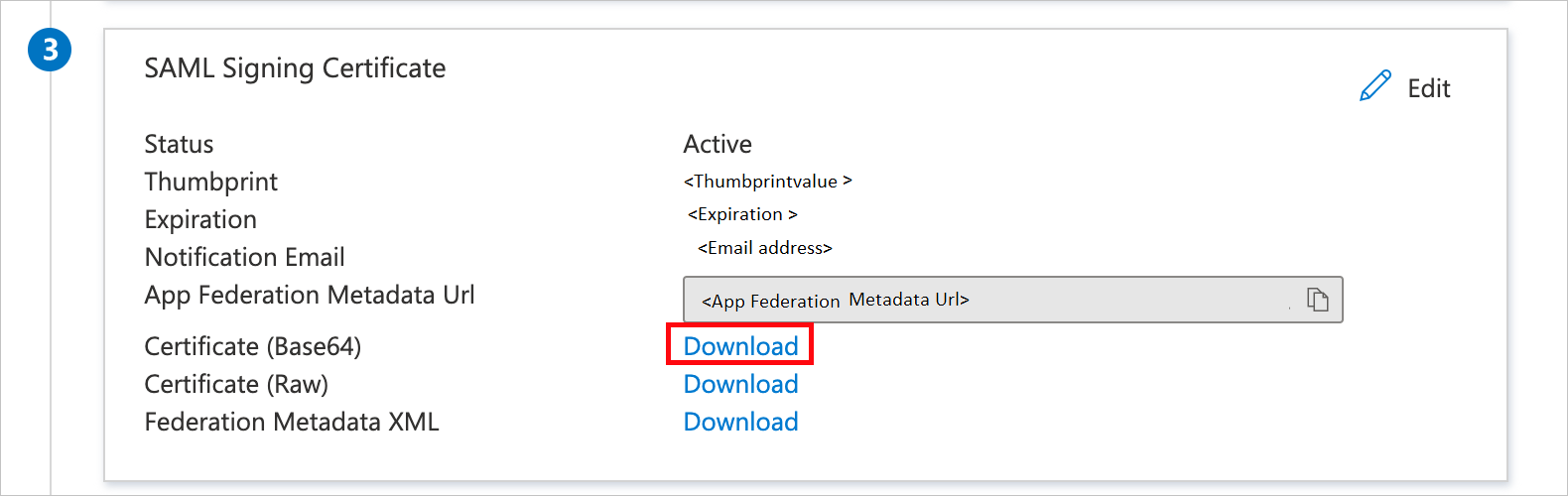
Veracode also expects a few more attributes to be passed back in the SAML response. These attributes are also pre-populated, but you can review them per your requirements.
| Name | Source attribute |
|---|---|
| firstname | User.givenname |
| lastname | User.surname |
| User.mail |
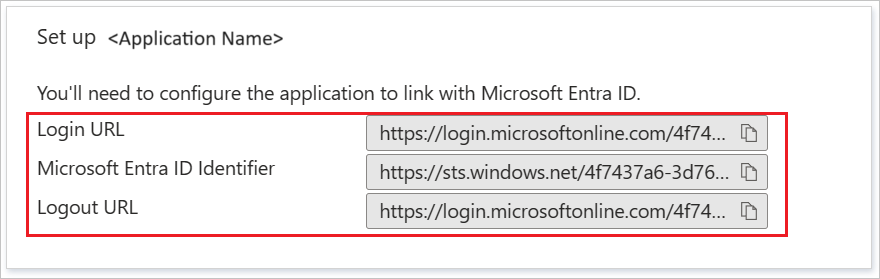
On the Set up Veracode section, copy and save the provided URLs to use later in your Veracode Platform SAML setup.
In this section, you'll create a test user called B.Simon.
B.Simon.B.Simon@contoso.com.In this section, you'll enable B.Simon to use single sign-on by granting access to Veracode.
Notes:
In a different web browser window, sign in to your Veracode company site as an administrator.
From the menu on the top, select Settings > Admin.

Select the SAML Certificate tab.
In the SAML Certificate section, perform the following steps:

a. For Issuer, paste the value of the Microsoft Entra Identifier that you've copied.
b. For Assertion Signing Certificate, select Choose File to upload your downloaded certificate.
c. Note the values of the three URLs (SAML Assertion URL, SAML Audience URL, Relay state URL).
d. Click Save.
Take the values of the SAML Assertion URL, SAML Audience URL and Relay state URL and update them in the Microsoft Entra settings for the Veracode integration (follow the table below for proper conversions) NOTE: Relay State is NOT optional.
| Veracode URL | Microsoft Entra ID Field |
|---|---|
| SAML Audience URL | Identifier (Entity ID) |
| SAML Assertion URL | Reply URL (Assertion Consumer Service URL) |
| Relay State URL | Relay State |
Select the JIT Provisioning tab.

In the Organization Settings section, toggle the Configure Default Settings for Just-in-Time user provisioning setting to On.
In the Basic Settings section, for User Data Updates, select Prefer Veracode User Data. This will cause conflicts between data passed in the SAML assertion from Microsoft Entra ID and user data in the Veracode platform to be resolved using the Veracode user data.
In the Access Settings section, under User Roles, select from the following For more information about Veracode user roles, see the Veracode Documentation:

In this section, a user called B.Simon is created in Veracode. Veracode supports just-in-time user provisioning, which is enabled by default. There's no action item for you in this section. If a user doesn't already exist in Veracode, a new one is created after authentication.
הערה
You can use any other Veracode user account creation tools or APIs provided by Veracode to provision Microsoft Entra user accounts.
In this section, you test your Microsoft Entra single sign-on configuration with following options.
Click on Test this application, and you should be automatically signed in to the Veracode for which you set up the SSO.
You can use Microsoft My Apps. When you click the Veracode tile in the My Apps, you should be automatically signed in to the Veracode for which you set up the SSO. For more information about the My Apps, see Introduction to the My Apps.
Once you configure Veracode you can enforce session control, which protects exfiltration and infiltration of your organization’s sensitive data in real time. Session control extends from Conditional Access. Learn how to enforce session control with Microsoft Defender for Cloud Apps.
אירוע
9 באפר׳, 15 - 10 באפר׳, 12
קוד העתיד עם בינה מלאכותית והתחברות לעמיתים ומומחים של Java ב- JDConf 2025.
הירשם כעתהדרכה
מודול
Implement and monitor the integration of enterprise apps for SSO - Training
Deploying and monitoring enterprise applications to Azure solutions can ensure security. Explore how to deploy on-premises and cloud based apps to users.
אישור
Microsoft Certified: Identity and Access Administrator Associate - Certifications
להדגים את התכונות של Microsoft Entra ID כדי לבצע מודרניזציה של פתרונות זהות, ליישם פתרונות היברידיים וליישם פיקוח על זהות.