Atvik
Mar 31, 11 PM - Apr 2, 11 PM
Stærsti Fabric, Power BI og SQL námsviðburðurinn. 31. mars – 2. apríl. Notaðu kóðann FABINSIDER til að spara $400.
Skráðu þig í dagÞessi vafri er ekki lengur studdur.
Uppfærðu í Microsoft Edge til að nýta þér nýjustu eiginleika, öryggisuppfærslur og tæknilega aðstoð.
Microsoft recommends locking all of your storage accounts with an Azure Resource Manager lock to prevent accidental or malicious deletion of the storage account. There are two types of Azure Resource Manager resource locks:
For more information about Azure Resource Manager locks, see Lock resources to prevent changes.
Varúð
Locking a storage account does not protect containers or blobs within that account from being deleted or overwritten. For more information about how to protect blob data, see Data protection overview.
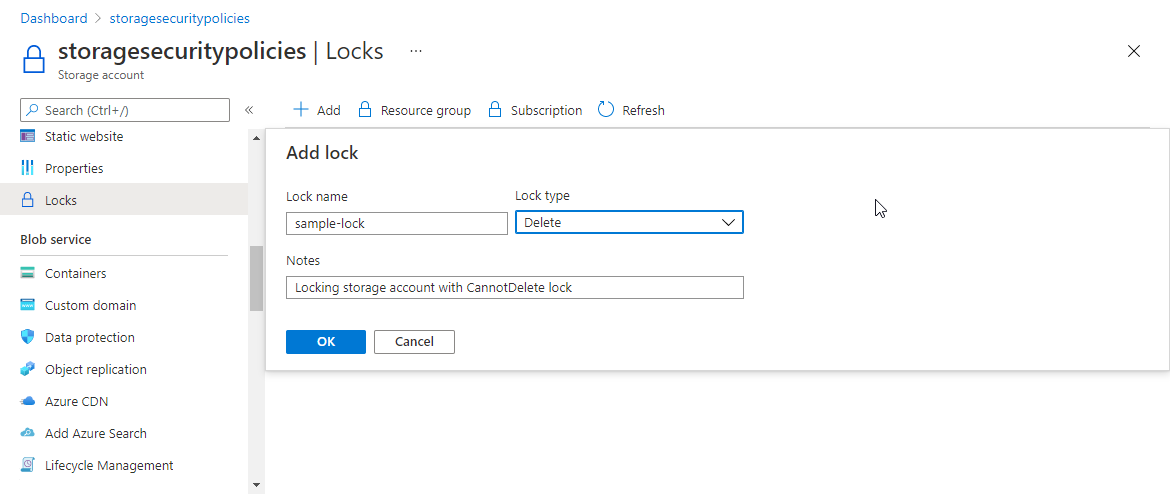
To configure a lock on a storage account with the Azure portal, follow these steps:
Navigate to your storage account in the Azure portal.
Under the Settings section, select Locks.
Select Add.
Provide a name for the resource lock, and specify the type of lock. Add a note about the lock if desired.
When a ReadOnly lock is applied to a storage account, the List Keys operation is blocked for that storage account. The List Keys operation is an HTTPS POST operation, and all POST operations are prevented when a ReadOnly lock is configured for the account. The List Keys operation returns the account access keys, which can then be used to read and write to any data in the storage account.
If a client is in possession of the account access keys at the time that the lock is applied to the storage account, then that client can continue to use the keys to access data. However, clients who do not have access to the keys will need to use Microsoft Entra credentials to access blob or queue data in the storage account.
Users of the Azure portal may be affected when a ReadOnly lock is applied, if they have previously accessed blob or queue data in the portal with the account access keys. After the lock is applied, portal users will need to use Microsoft Entra credentials to access blob or queue data in the portal. To do so, a user must have at least two RBAC roles assigned to them: the Azure Resource Manager Reader role at a minimum, and one of the Azure Storage data access roles. For more information, see one of the following articles:
Data in Azure Files or the Table service may become unaccessible to clients who have previously been accessing it with the account keys. As a best practice, if you must apply a ReadOnly lock to a storage account, then move your Azure Files and Table service workloads to a storage account that is not locked with a ReadOnly lock.
Atvik
Mar 31, 11 PM - Apr 2, 11 PM
Stærsti Fabric, Power BI og SQL námsviðburðurinn. 31. mars – 2. apríl. Notaðu kóðann FABINSIDER til að spara $400.
Skráðu þig í dagÞjálfun
Eining
Secure your Azure Storage account - Training
Learn how Azure Storage provides multilayered security to protect your data with access keys, secure networks, and Advanced Threat Protection monitoring.
Vottorð
Microsoft Certified: Azure Administrator Associate - Certifications
Demonstrate key skills to configure, manage, secure, and administer key professional functions in Microsoft Azure.
Skjöl
Recover a deleted storage account - Azure Storage
Learn how to recover a deleted storage account within the Azure portal.
Lock your Azure resources to protect your infrastructure - Azure Resource Manager
Learn how to lock all users and roles to protect your Azure resources from updates or deletions.
Storage account overview - Azure Storage
Learn about the different types of storage accounts in Azure Storage. Review account naming, performance tiers, access tiers, redundancy, encryption, endpoints, and more.