Događaj
Izgradite AI aplikacije i agente
17. mar 21 - 21. mar 10
Pridružite se seriji sastanaka kako biste izgradili skalabilna AI rešenja zasnovana na stvarnim slučajevima korišćenja sa kolegama programerima i stručnjacima.
Registrujte se odmahOvaj pregledač više nije podržan.
Nadogradite na Microsoft Edge biste iskoristili najnovije funkcije, bezbednosne ispravke i tehničku podršku.
This article shows you how to create or edit an activity log, service health, or resource health alert rule in Azure Monitor. To learn more about alerts, see the alerts overview.
You create an alert rule by combining the resources to be monitored, the monitoring data from the resource, and the conditions that you want to trigger the alert. You can then define action groups and alert processing rules to determine what happens when an alert is triggered.
Alerts triggered by these alert rules contain a payload that uses the common alert schema.
To create or edit an alert rule, you must have the following permissions:
There are multiple ways to create or edit an alert rule.
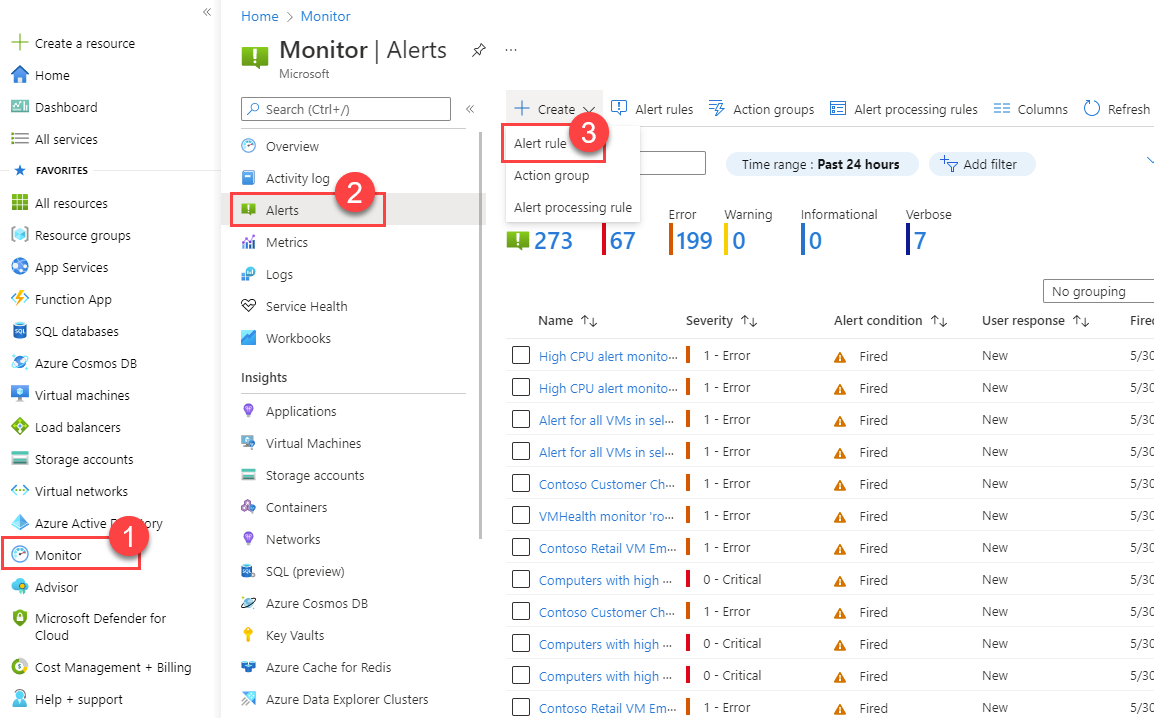
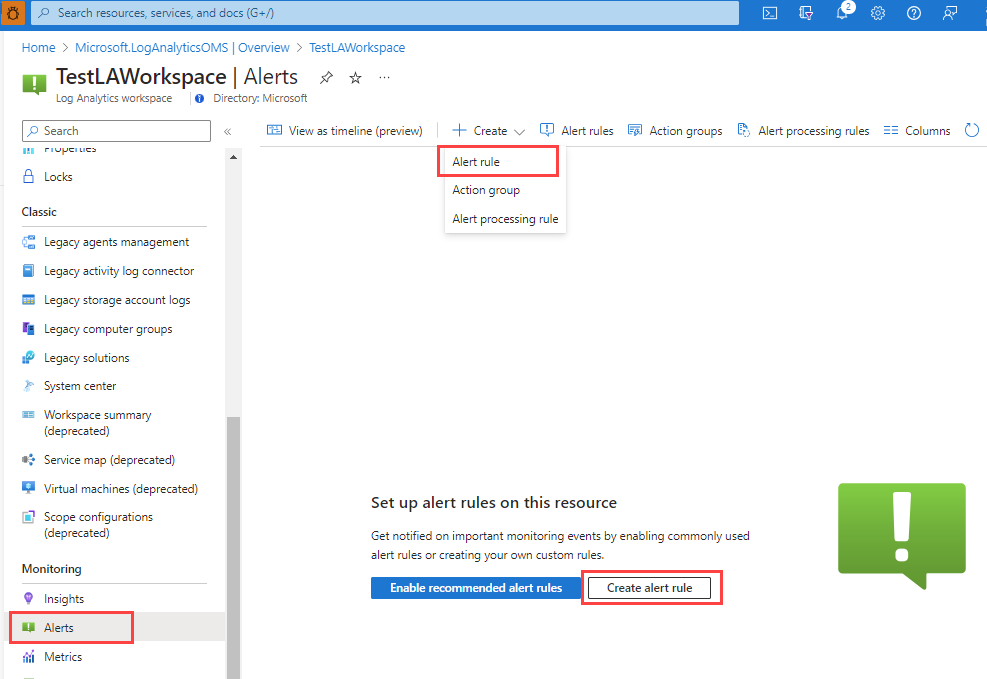
In the Azure portal, either from the home page or from a specific resource, select Alerts on the left pane.
Select Alert rules.
Select the alert rule you want to edit, and then select Edit.
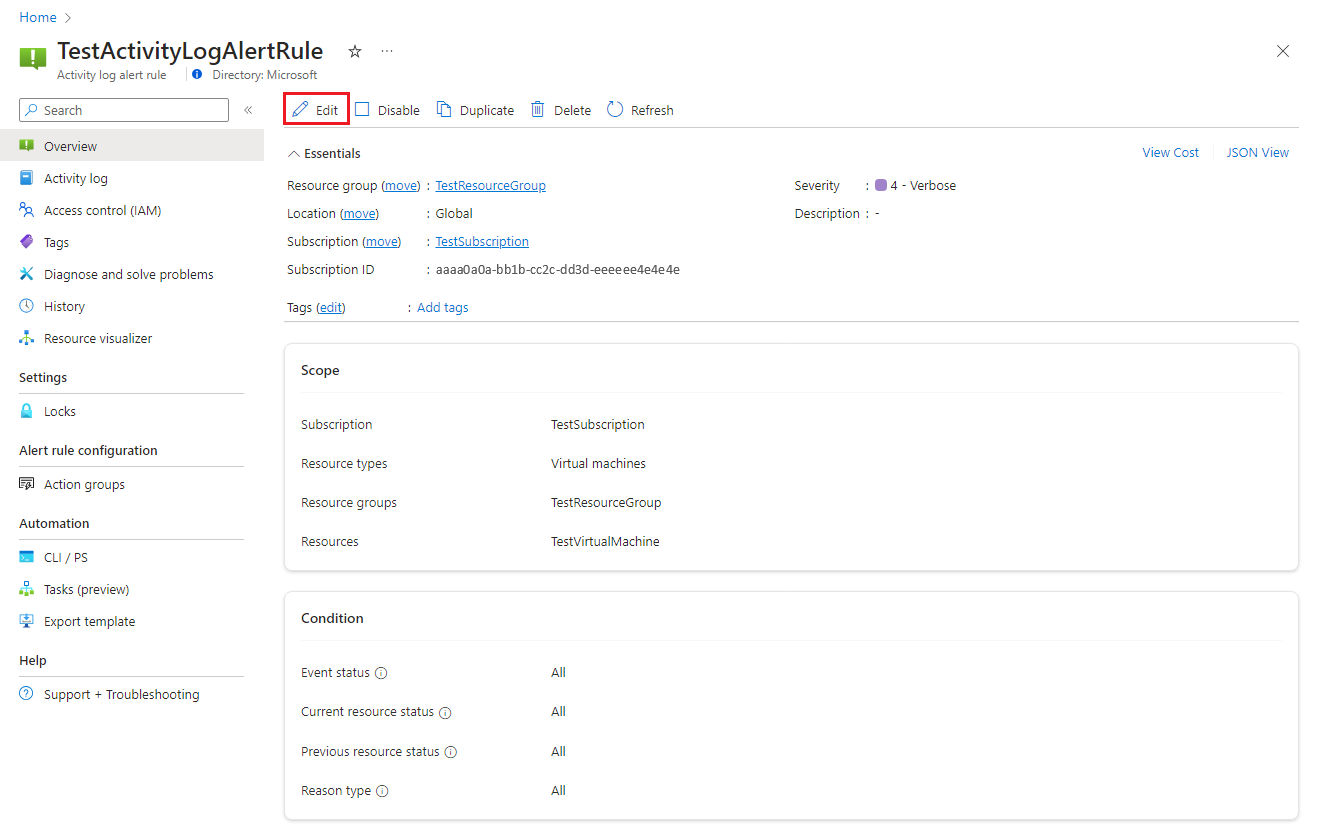
Select any of the tabs for the alert rule to edit the settings.
On the Select a resource pane, set the scope for your alert rule. You can filter by subscription, resource type, or resource location.
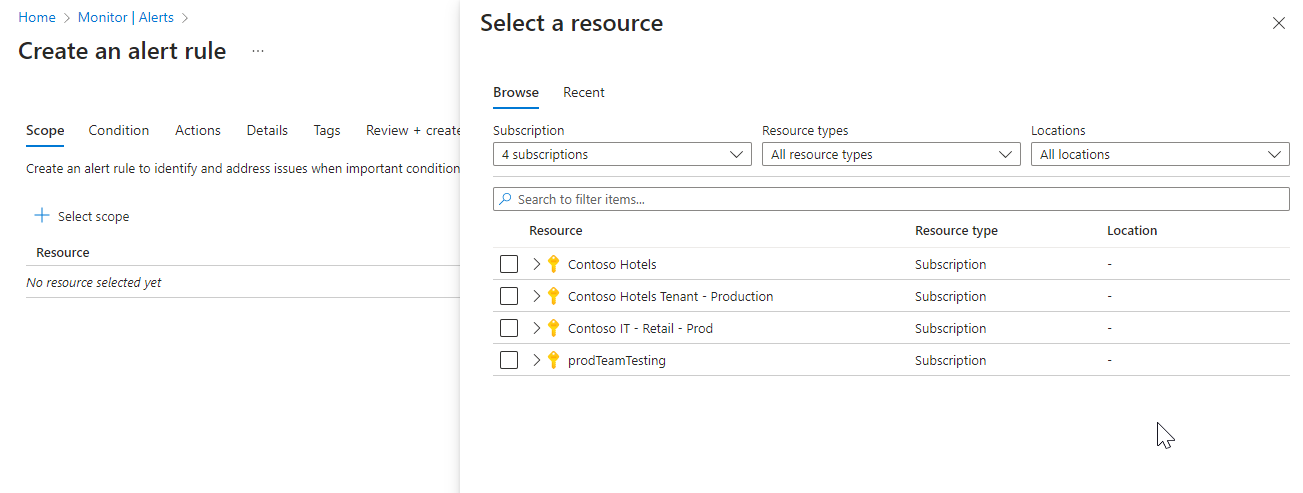
Select Apply.
On the Condition tab, select Activity log, Resource health, or Service health. Or select See all signals if you want to choose a different signal for the condition.
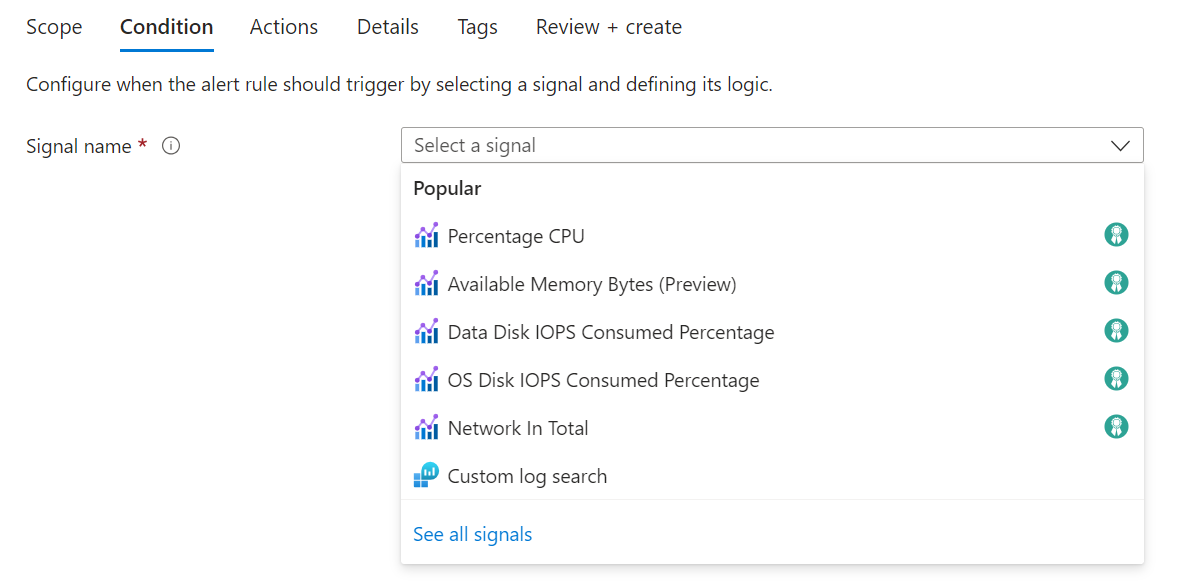
(Optional) If you selected See all signals in the previous step, use the Select a signal pane to search for the signal name or filter the list of signals. Filter by:
This table describes the available services for activity log alert rules:
| Signal source | Description |
|---|---|
| Activity log – Policy | The service that provides the policy-related activity log events. |
| Activity log – Autoscale | The service that provides the autoscale-related activity log events. |
| Activity log – Security | The service that provides the security-related activity log events. |
| Resource health | The service that provides the resource-level health status. |
| Service health | The service that provides the subscription-level health status. |
Select the signal name, and then select Apply.
On the Conditions pane, select the Chart period value.
The Preview chart shows the results of your selection.
In the Alert logic section, select values for each of these fields:
| Field | Description |
|---|---|
| Event level | Select the level of the events for this alert rule. Values are Critical, Error, Warning, Informational, Verbose, and All. |
| Status | Select the status levels for the alert. |
| Event initiated by | Select the user principal or service principal that initiated the event. |
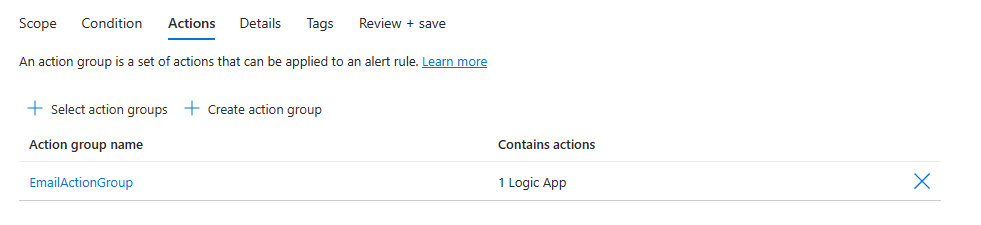
On the Actions tab, you can optionally select or create action groups for your alert rule.
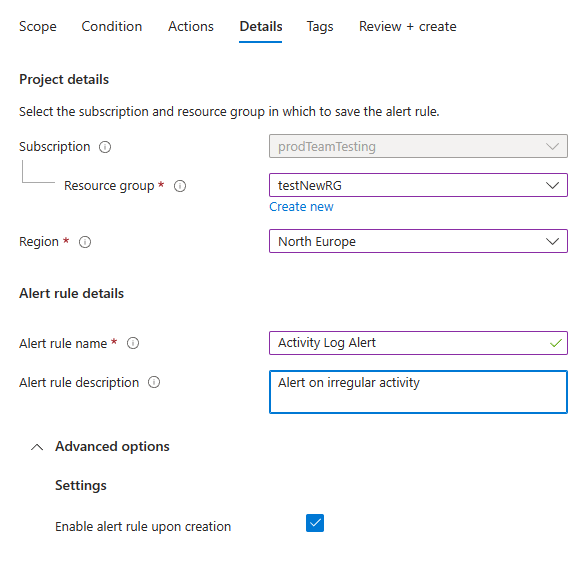
On the Details tab, enter values for Alert rule name and Alert rule description.
Select Enable alert rule upon creation for the alert rule to start running as soon as you finish creating it.
(Optional) For Region, select a region in which your alert rule will be processed. If you need to make sure the rule is processed within the EU Data Boundary, select the North Europe or West Europe region. In all other cases, you can select the Global region (which is the default).
Napomena
Service Health alert rules can only be located in the Global region.
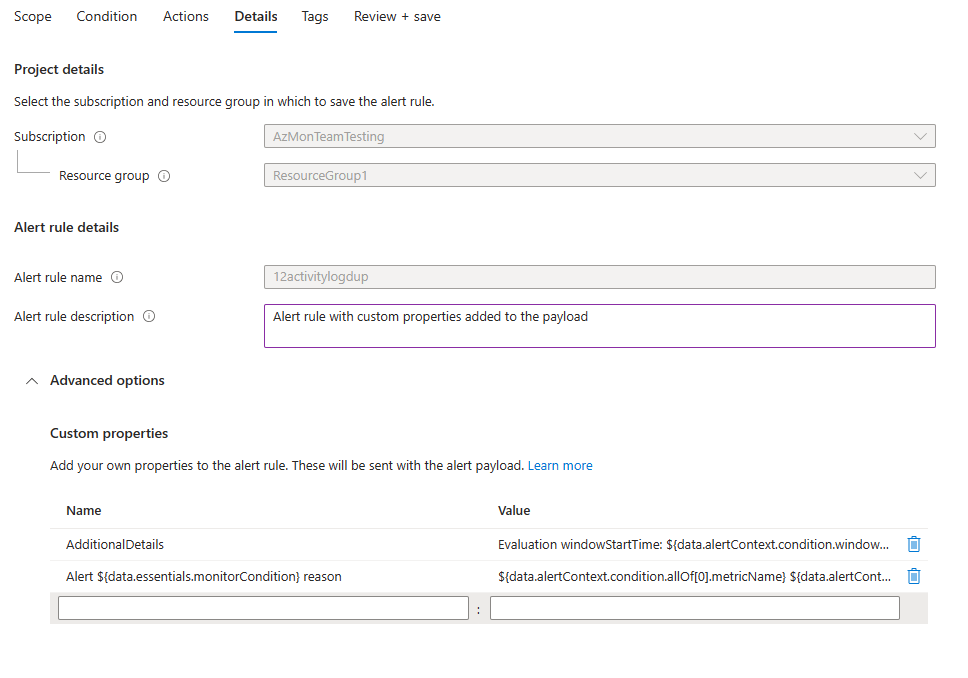
(Optional) In the Custom properties section, if this alert rule contains action groups, you can add your own properties to include in the alert notification payload. You can use these properties in the actions that the action group calls, such as by a webhook, Azure function, or logic app action.
The custom properties are specified as key/value pairs by using static text, a dynamic value extracted from the alert payload, or a combination of both.
The format for extracting a dynamic value from the alert payload is: ${<path to schema field>}. For example: ${data.essentials.monitorCondition}.
Use the format of the common alert schema to specify the field in the payload, whether or not the action groups configured for the alert rule use the common schema.
Napomena
The following examples use values in Custom properties to utilize data from a payload that uses the common alert schema.
This example creates an Additional Details tag with data regarding the window start time and window end time:
Additional DetailsEvaluation windowStartTime: ${data.alertContext.condition.windowStartTime}. windowEndTime: ${data.alertContext.condition.windowEndTime}AdditionalDetails:Evaluation windowStartTime: 2023-04-04T14:39:24.492Z. windowEndTime: 2023-04-04T14:44:24.492ZThis example adds data regarding the reason for resolving or firing the alert:
Alert ${data.essentials.monitorCondition} reason${data.alertContext.condition.allOf[0].metricName} ${data.alertContext.condition.allOf[0].operator} ${data.alertContext.condition.allOf[0].threshold} ${data.essentials.monitorCondition}. The value is ${data.alertContext.condition.allOf[0].metricValue}Alert Resolved reason: Percentage CPU GreaterThan5 Resolved. The value is 3.585Alert Fired reason": "Percentage CPU GreaterThan5 Fired. The value is 10.585On the Tags tab, you can optionally set any required tags on the alert rule resource.
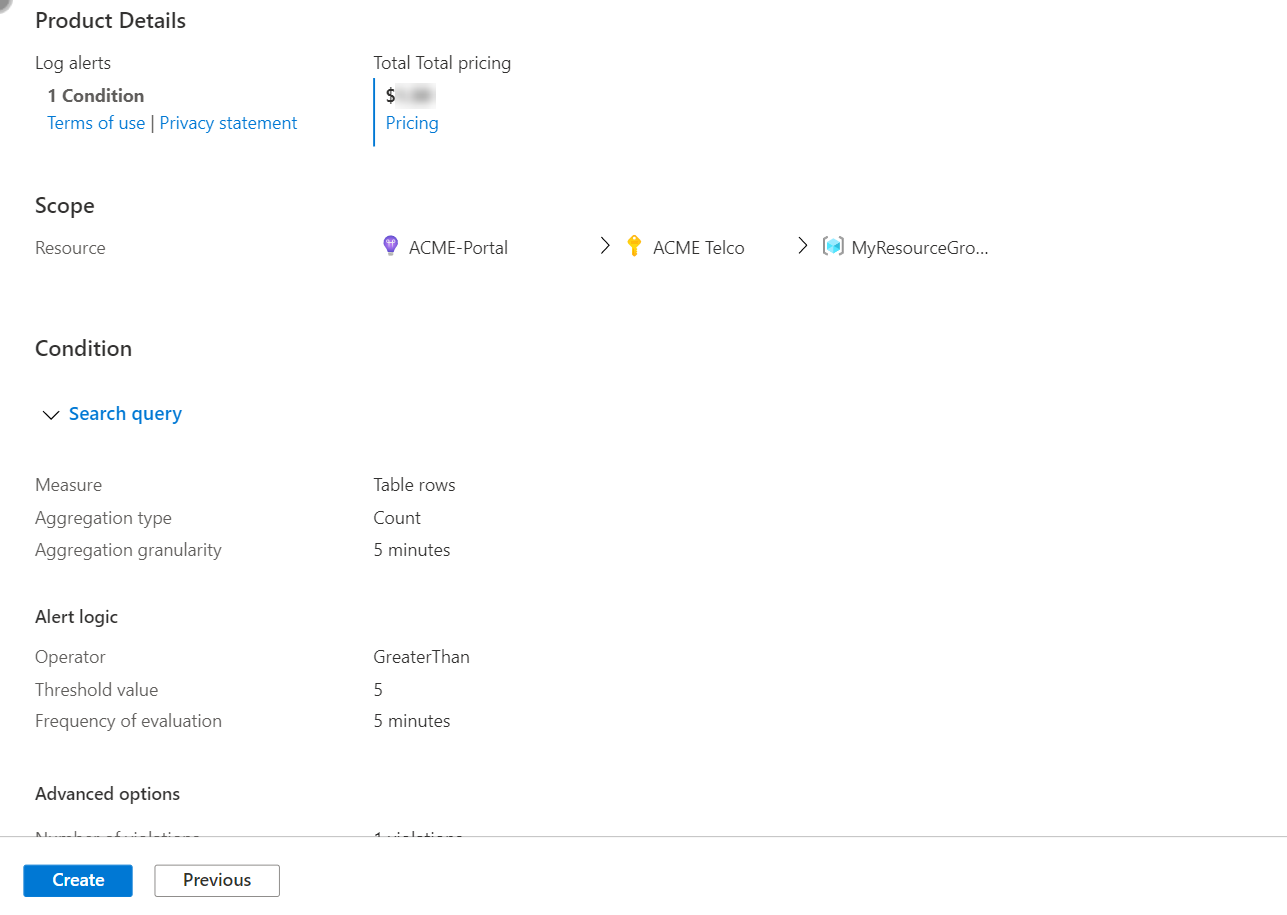
On the Review + create tab, the rule is validated. If there's a problem, go back and fix it.
When validation passes and you've reviewed the settings, select the Create button.
Događaj
Izgradite AI aplikacije i agente
17. mar 21 - 21. mar 10
Pridružite se seriji sastanaka kako biste izgradili skalabilna AI rešenja zasnovana na stvarnim slučajevima korišćenja sa kolegama programerima i stručnjacima.
Registrujte se odmahObuka
Modul
Configure alerts and responses - Training
In this module, you learn how Azure Monitoring alerts proactively notifies you when Azure Monitor data indicates there might be a problem with your infrastructure or applications before the problem becomes one for your users.
Certifikacija
Microsoft Certified: Azure Administrator Associate - Certifications
Demonstrate key skills to configure, manage, secure, and administer key professional functions in Microsoft Azure.