Device Control for macOS
Applies to:
- Microsoft Defender for Endpoint Plan 1
- Microsoft Defender for Endpoint Plan 2
- Microsoft Defender XDR
- Microsoft Defender for Business
Want to experience Microsoft Defender for Endpoint? Sign up for a free trial.
Requirements
Device Control for macOS has the following prerequisites:
- Microsoft Defender for Endpoint entitlement (can be trial)
- Minimum OS version: macOS 11 or higher
- Minimum product version: 101.34.20
Overview
Microsoft Defender for Endpoint Device Control feature enables you to:
- Audit, allow, or prevent the read, write, or execute access to removable storage; and
- Manage iOS and Portable devices, and Apple APFS encrypted devices and Bluetooth media, with or without exclusions.
Prepare your endpoints
Microsoft Defender for Endpoint entitlement (can be trial)
Minimum OS version: macOS 11 or higher
Deploy Full Disk Access: you may already have previously created and deployed this https://github.com/microsoft/mdatp-xplat/blob/master/macos/mobileconfig/profiles/fulldisk.mobileconfig for other MDE features. You need to grant Full Disk Access permission for a new application:
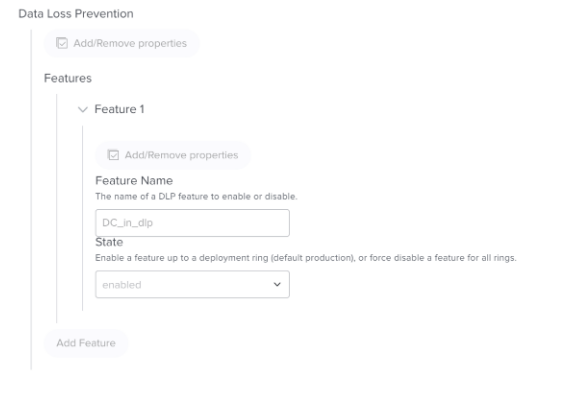
com.microsoft.dlp.daemon.Enable Device Control on the MDE Preference setting:
Data Loss Prevention (DLP)/Features/
For Feature Name, enter "DC_in_dlp"
For State, enter "enabled"
Example 1: JAMF using schema.json
Example 2: [demo.mobileconfig](https://github.com/microsoft/mdatp-devicecontrol/blob/main/Removable%20Storage%20Access%20Control%20Samples/macOS/mobileconfig/demo.mobileconfig)
<key>dlp</key>
<dict>
<key>features</key>
<array>
<dict>
<key>name</key>
<string>DC_in_dlp</string>
<key>state</key>
<string>enabled</string>
</dict>
</array>
</dict>
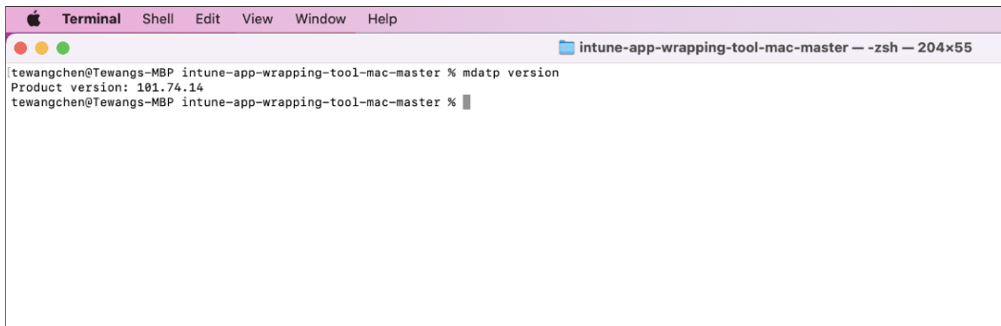
Minimum product version: 101.91.92 or higher
Run mdatp version through Terminal to see the product version on your client machine:
Understanding policies
Policies determine the behavior of device control for macOS. The policy is targeted via Intune or JAMF to a collection of machines or users.
The Device Control for macOS policy includes settings, groups, and rules:
- Global setting called 'settings' allows you to define the global environment.
- Group called 'groups' allows you to create media groups. For example, authorized USB group or encrypted USB group.
- Access policy rule called 'rules' allows you to create policy to restrict each group. For example, only allow authorized user to Write access-authorized USB group.
Note
We recommend you use the examples on the GitHub to understand the properties: mdatp-devicecontrol/Removable Storage Access Control Samples/macOS/policy at main - microsoft/mdatp-devicecontrol (github.com).
You can also use the scripts at mdatp-devicecontrol/tree/main/python#readme at main - microsoft/mdatp-devicecontrol (github.com) to translate Windows Device Control policy to macOS Device Control policy or translate macOS Device Control V1 policy to this V2 policy.
Note
There are known issues with device control for macOS that customers should consider when creating policies.
Best practices
Device control for macOS has similar capabilities to Device control for Windows, but macOS and Windows provide different underlying capabilities to manage devices, so there are some important differences:
- macOS doesn't have a centralized Device Manager or view of devices. Access is granted/denied to applications that interact with devices. This is why on macOS there are a richer set of access types. For example on a
portableDevicedevice control for macOS can deny or allowdownload_photos_from_device. - To stay consistent with Windows, there are
generic_read,generic_writeandgeneric_executeaccess types. Policies with generic access types don't need to be changed if/when additional specific access types are added in the future. The best practice is to use generic access types unless there's a specific need to deny/allow a more specific operation. - Creating a
denypolicy using generic access types is the best way to attempt to completely block all operations for that type of device (e.g. Android phones), but there may still be gaps if the operation is performed using an application that isn't supported by macOS device control.
Settings
Here are the properties you can use when you create the groups, rules, and settings in device control policy for macOS.
| Property name | Description | Options |
|---|---|---|
| features | Feature specific configurations | You can set disable to false or true for following features: - removableMedia- appleDevice- portableDevice, including camera or PTP media- bluetoothDeviceThe default is true, so if you don't configure this value, it will not apply even if you create a custom policy for removableMedia, because it's disabled by default. |
| global | Set default enforcement | You can set defaultEnforcement to- allow (default)- deny |
| ux | You can set a hyperlink on notification. | navigationTarget: string. Example: "http://www.microsoft.com" |
Group
| Property name | Description | Options |
|---|---|---|
$type |
The kind of group | "device" |
id |
GUID, a unique ID, represents the group and will be used in the policy. | You can generate the ID through New-Guid (Microsoft.PowerShell.Utility) - PowerShell or the uuidgen command on macOS |
name |
Friendly name for the group. | string |
query |
The media coverage under this group | See the query properties tables below for details. |
Query
Device Control supports two kinds of queries:
Query type 1 is as follows:
| Property name | Description | Options |
|---|---|---|
$type |
Identify the logical operation to perform on the clauses | all: Any attributes under the clauses are an And relationship. For example, if the administrator puts vendorId and serialNumber, for every connected USB, the system checks to see whether the USB meets both values.and: is equivalent to all any: The attributes under the clauses are Or relationship. For example, if administrator puts vendorId and serialNumber, for every connected USB, system does the enforcement as long as the USB has either an identical vendorId or serialNumber value. or: is equivalent to any |
clauses |
Use media device property to set group condition. | An array of clause objects that are evaluated to determine group membership. See the Clause section below. |
Query type 2 is as follows:
| Property name | Description | Options |
|---|---|---|
$type |
Identify the logical operation to perform on the subquery | not: logical negation of a query |
query |
A subquery | A query which will be negated. |
Clause
Clause properties
| Property name | Description | Options |
|---|---|---|
$type |
The type of clause | See the following table for supported clauses. |
value |
$type specific value to use |
Supported clauses
| clause $type | value | Description |
|---|---|---|
primaryId |
One of: - apple_devices- removable_media_devices - portable_devices - bluetooth_devices |
|
vendorId |
4 digit hexadecimal string | Matches a device's vendor ID |
productId |
4 digit hexadecimal string | Matches a device's product ID |
serialNumber |
string | Matches a device's serial number. Doesn't match if the device doesn't have a serial number. |
encryption |
apfs | Match if a device is apfs-encrypted. |
groupId |
UUID string | Match if a device is a member of another group. The value represents the UUID of the group to match against. The group must be defined within the policy prior to the clause. |
Access policy rule
| Property name | Description | Options |
|---|---|---|
id |
GUID, a unique ID, represents the rule and will be used in the policy. | New-Guid (Microsoft.PowerShell.Utility) - PowerShell uuidgen |
name |
String, the name of the policy and will display on the toast based on the policy setting. | |
includeGroups |
The group(s) that the policy will be applied to. If multiple groups are specified, the policy applies to any media in all those groups. If not specified, the rule applies to all devices. | The id value inside the group must be used in this instance. If multiple groups are in the includeGroups, it's AND. "includeGroups": ["3f082cd3-f701-4c21-9a6a-ed115c28e217"] |
excludeGroups |
The group(s) that the policy doesn't apply to. | The id value inside the group must be used in this instance. If multiple groups are in the excludeGroups, it's OR. |
entries |
One rule can have multiple entries; each entry with a unique GUID tells Device Control one restriction. | See entry properties table later in this article to get the details. |
The following table lists the properties you can use in your entry:
| Property name | Description | Options |
|---|---|---|
$type |
Includes: - removableMedia- appleDevice- PortableDevice- bluetoothDevice- generic |
|
| enforcement | - $type:- allow- deny- auditAllow- auditDenyWhen $type allow is selected, options value supports: - disable_audit_allowEven if Allow happens and the auditAllow is setting configured, the system won't send event. When $type deny is selected, options value supports: disable_audit_denyEven if Block happens and the auditDeny is setting configured, the system won't show notification or send event. When $type auditAllow is selected, options value supports: send_eventWhen $type auditDeny is selected, options value supports: send_eventshow_notification |
|
access |
Specify one or more access rights for this rule. These may include either device specific granular permissions, or broader generic permissions. See table below for more details on the valid access types for a given entry $type. | |
id |
UUID |
The following table lists the properties you can use in entry:
Enforcement
Enforcement property name
| Property name | Description | Options |
|---|---|---|
$type |
The type of enforcement | See table below for supported enforcements |
options |
$type specific value to use | An array of options for the entry. May be omitted if not options are desired. |
Enforcement type
| Property name | Description | Options |
|---|---|---|
Enforcement $type |
options values [string] |
Description |
allow |
disable_audit_allow |
Even if Allow happens and the auditAllow is setting configured, the system won't send event. |
deny |
disable_audit_deny |
Even if Block happens and the auditDeny is setting configured, the system won't show notification or send event. |
auditAllow |
send_event |
Send telemetry |
auditDeny |
- send_event- show_notification |
- Send telemetry - Display Block UX to user |
Access types
| entry $type | 'access' values [string] | Generic Access | Description |
|---|---|---|---|
| appleDevice | backup_device | generic_read | |
| appleDevice | update_device | generic_write | |
| appleDevice | download_photos_from_device | generic_read | download photo from the specific iOS device to local machine |
| appleDevice | download_files_from_device | generic_read | download file(s) from the specific iOS device to local machine |
| appleDevice | sync_content_to_device | generic_write | sync content from local machine to specific iOS device |
| portableDevice | download_files_from_device | generic_read | |
| portableDevice | send_files_to_device | generic_write | |
| portableDevice | download_photos_from_device | generic_read | |
| portableDevice | debug | generic_execute | ADB tool control |
| *removableMedia | read | generic_read | |
| removableMedia | write | generic_write | |
| removableMedia | execute | generic_execute | generic_read |
| bluetoothDevice | download_files_from_device | ||
| bluetoothDevice | send_files_to_device | generic_write | |
| generic | generic_read | Equivalent to setting all access values denoted in this table that map to generic_read. | |
| generic | generic_write | Equivalent to setting all access values denoted in this table that map to generic_write. | |
| generic | generic_execute | Equivalent to setting all access values denoted in this table that map to generic_execute. |
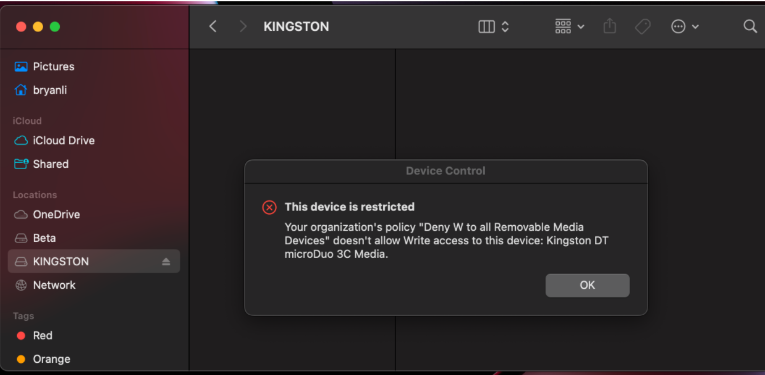
End-user experience
Once Deny happens and the notification is enabled in the policy, the end user sees a dialog:
Status
Use mdatp health --details device_control to inspect the Device Control status:
active : ["v2"]
v1_configured : false
v1_enforcement_level : unavailable
v2_configured : true
v2_state : "enabled"
v2_sensor_connection : "created_ok"
v2_full_disk_access : "approved"
active- feature version, you should see ["v2"]. (Device Control is enabled, but not configured.)- [] - Device Control isn't configured on this machine.
- ["v1"] - You are on a preview version of Device Control. Migrate to version 2 using this guide. v1 is considered obsolete and not described in this documentation.
- ["v1","v2"] - You have both v1 and v2 enabled. Offboard from v1.
v1_configured- v1 configuration is appliedv1_enforcement_level- when v1 is enabledv2_configured- v2 configuration is appliedv2_state- v2 status,enabledif fully workingv2_sensor_connection- ifcreated_ok, then Device Control established connection to the system extensionv2_full_disk_access- if notapproved, then Device Control can't prevent some or all operations
Reporting
You are able to see the policy event on Advanced hunting and Device Control report. For more information, see Protect your organization's data with Device Control.
Scenarios
Here are some common scenarios to help you familiarize with Microsoft Defender for Endpoint and Microsoft Defender for Endpoint Device Control.
Scenario 1: Deny any removable media but allow specific USBs
In this scenario, you need to create two groups: one group for any removable media, and another group for approved USBs group. You also need to create an access policy rule.
Step 1: Settings: enable Device Control and set Default Enforcement
"settings": {
"features": {
"removableMedia": {
"disable": false
}
},
"global": {
"defaultEnforcement": "allow"
},
"ux": {
"navigationTarget": "http://www.deskhelp.com"
}
}
Step 2: Groups: Create any removable media group and approved-USBs group
-1. Create a group to cover any removable media devices -1. Create a group for approved USBs -1. Combine those groups into one 'groups'
"groups": [
{
"type": "device",
"id": "3f082cd3-f701-4c21-9a6a-ed115c28e211",
"name": "All Removable Media Devices",
"query": {
"$type": "all",
"clauses": [
{
"$type": "primaryId",
"value": "removable_media_devices"
}
]
}
},
{
"type": "device",
"id": "3f082cd3-f701-4c21-9a6a-ed115c28e212",
"name": "Kingston Devices",
"query": {
"$type": "all",
"clauses": [
{
"$type": "vendorId",
"value": "0951"
}
]
}
}
]
Step 3: Rules: Create Deny policy for unallowed USBs
Create access policy rule and put into 'rules':
"rules": [
{
"id": "772cef80-229f-48b4-bd17-a69130092981",
"name": "Deny RWX to all Removable Media Devices except Kingston",
"includeGroups": [
"3f082cd3-f701-4c21-9a6a-ed115c28e211"
],
"excludeGroups": [
"3f082cd3-f701-4c21-9a6a-ed115c28e212"
],
"entries": [
{
"$type": "removableMedia",
"id": "A7CEE2F8-CE34-4B34-9CFE-4133F0361035",
"enforcement": {
"$type": "deny"
},
"access": [
"read",
"write",
"execute"
]
},
{
"$type": "removableMedia",
"id": "18BA3DD5-4C9A-458B-A756-F1499FE94FB4",
"enforcement": {
"$type": "auditDeny",
"options": [
"send_event",
"show_notification"
]
},
"access": [
"read",
"write",
"execute"
]
}
]
}
]
In this case, only have one access rule policy, but if you have multiple, make sure to add all into 'rules'.
Known Issues
Warning
In macOS Sonoma 14.3.1, Apple made a change to the handling of Bluetooth devices that impacts Defender for Endpoint device controls ability to intercept and block access to Bluetooth devices. At this time, the recommended mitigation is to use a version of macOS less than 14.3.1.
Warning
Device Control on macOS restricts Android devices that are connected using PTP mode only. Device control does not restrict other modes such as File Transfer, USB Tethering and MIDI
See also
- Deploy Device Control by using Intune
- Deploy Device Control by using JAMF
- Deploy Device Control manually
- macOS Device Control frequently asked questions (FAQ)
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender for Endpoint Tech Community.
Feedback
Kommer snart: Under hela 2024 kommer vi att fasa ut GitHub-problem som feedbackmekanism för innehåll och ersätta det med ett nytt feedbacksystem. Mer information finns i: https://aka.ms/ContentUserFeedback.
Skicka och visa feedback för