@ChristianL1980
Thank you for your detailed post!
What are the MS-Organization-P2P-Access certificates:
The MS-Organization-P2P-Access certificates are issued by Azure AD to both, Azure AD joined, and hybrid Azure AD joined devices. These certificates are used to enable trust between devices in the same tenant for remote desktop scenarios. One certificate is issued to the device, and another is issued to the user.
The device certificate is present in Local Computer\Personal\Certificates and is valid for one day. This certificate is renewed (by issuing a new certificate) if the device is still active in Azure AD. The user certificate is present in Current User\Personal\Certificates and this certificate is also valid for one day, but it is issued on-demand when a user attempts a remote desktop session to another Azure AD joined device. It is not renewed on expiry.
Both these certificates are issued using the MS-Organization-P2P-Access certificate present in the Local Computer\AAD Token Issuer\Certificates. This certificate is issued by Azure AD during device registration.
Workaround:
Because you're receiving SCOM Alerts from the certificates, I found some related threads that might help point you in the right direction. Since the certificate(s) are only valid for one day, one customer found that you should be able to safely skip this error, for more info. While another customer worked directly with our support team and was told "The expiration date of the certificate is 24Hrs, thus, you can safely ignore them", for more info.
If these workarounds don't work for your environment, or if you'd like our support team to take a closer look into this, please let me know.
Thank you for your time and patience throughout this issue.
----------
Please remember to "Accept Answer" if any answer/reply helped, so that others in the community facing similar issues can easily find the solution.
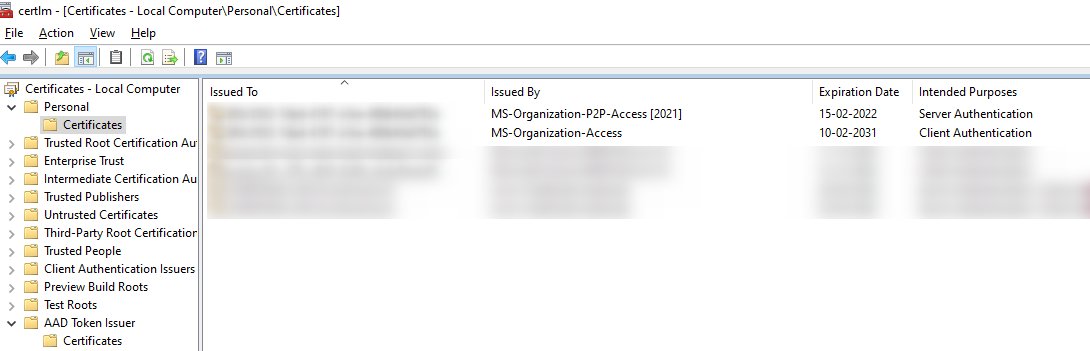
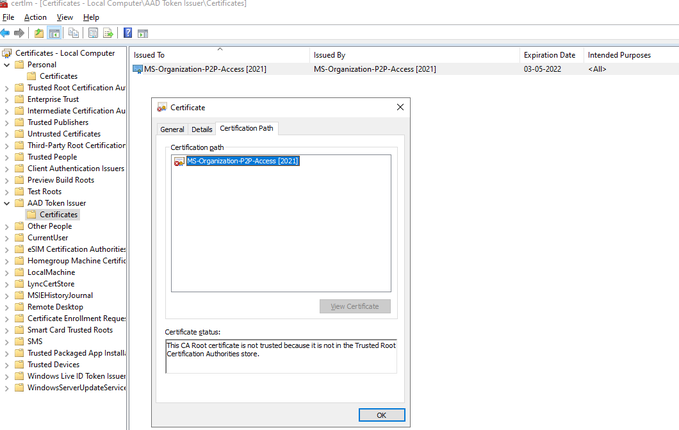 Use case seems to be limited to RDP in same tenant between devices. BUT cert in the AAD Token Issuer folder MS-Organization-P2P-Access [2021] used for issue certs locally not trusted by ROOT CA causing SCOM ALERTS! What is the correct way to solve this? The issuer cert I can read used for self issuing certs locally this is causing issues because the root ca cert not trusted. I can´t find anywhere explaining what to do. please help us solve this as we get lots of SCOM alerts. For now we do not use the RDP using AAD credentials maybe at a later time.
Use case seems to be limited to RDP in same tenant between devices. BUT cert in the AAD Token Issuer folder MS-Organization-P2P-Access [2021] used for issue certs locally not trusted by ROOT CA causing SCOM ALERTS! What is the correct way to solve this? The issuer cert I can read used for self issuing certs locally this is causing issues because the root ca cert not trusted. I can´t find anywhere explaining what to do. please help us solve this as we get lots of SCOM alerts. For now we do not use the RDP using AAD credentials maybe at a later time. 
