Hi all,
Continuation of the topic https://learn.microsoft.com/en-us/answers/questions/999137/defender-onboarding-co-management.html and a guide in it I believe.
What I wanted to achieve is to apply automatically bitlocker through Co-Management. All is set fine, devices are co managed. After understanding all from previous post, we managed to clean the workloads and there were no further conflicts. Policies for bitlocker arrived to device which I could see for example through Intune or regedit (key saying require encryption was set to 1) etc.
We were sure policies do apply.
In event viewer Bitlocker API, for my two devices I was getting two entries:
- The following DMA (Direct Memory Access) capable devices are not declared as protected from external access, which can block security features such as BitLocker automatic device encryption:
- Bitlocker cannot use Secure Boot for integrity because the UEFI variable 'SecureBoot' could not be read
Error Message: A required privilege is not held by the client
Bitlocker encryption doesn't happen automagically at all. What is even weirder, is that TPM 2.0 UEFI and all that settings were on, except for secure boot.
Troubleshooting so far was to:
- Set policy to act like below with explanation: Compatible TPM startup PIN
Compatible TPM startup key
Compatible TPM startup key and PIN
These settings are all very related and coordinating the selections is important. The BitLocker CSP documentation has a brief note that says “Only one of the additional authentication options can be required at startup, otherwise an error occurs.” That error will be a “Policy Conflict”, because if you Require any one of these then you CANNOT Allow anything else. So we’ll Require TPM, and set the other three to “Do not allow
This removed the 1st error, so the DMA one.
Secondly, I've turned secure boot on one of two machines and tested if secure boot is really needed
From that point I have verified if TPM and all other components are setup correctly and they were in 99%!
the only issue was that Key protectors were empty, for every built device, these are factory new, built and connected with co management devices, user connected to them
I ran manage-bde -protectors c: -get to validate that 7,11 are the PCR used - And this is the ONLY missing thing, it was simply empty. In my understanding is that if TPM owner is known, if system works properly, hardware and all that stuff is put in place, this should populate on its own. It didn't, so I ran the following:
manage-bde -protectors c: -delete -t tpm
manage-bde -protectors c: -add -tpm
This didn't still trigger any auto apply both on Secure Boot enabled and disabled device. I've switched off the enabled one, and after logging back in I've received
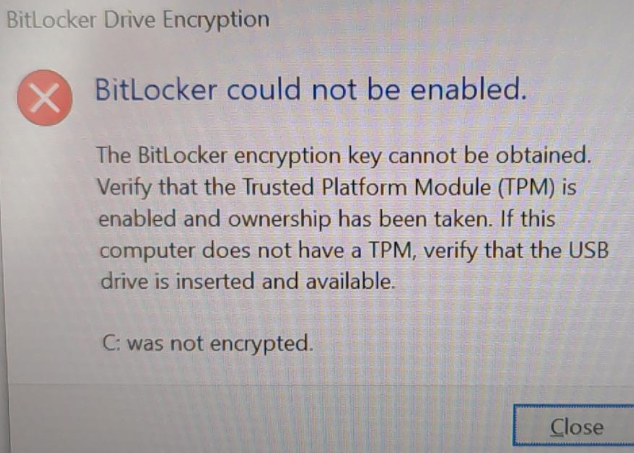
I ran out of ideas what is happening. What I assume is that somehow the policy is not able to start the auto encryption, but why?
My workaround was to run a TS from MECM
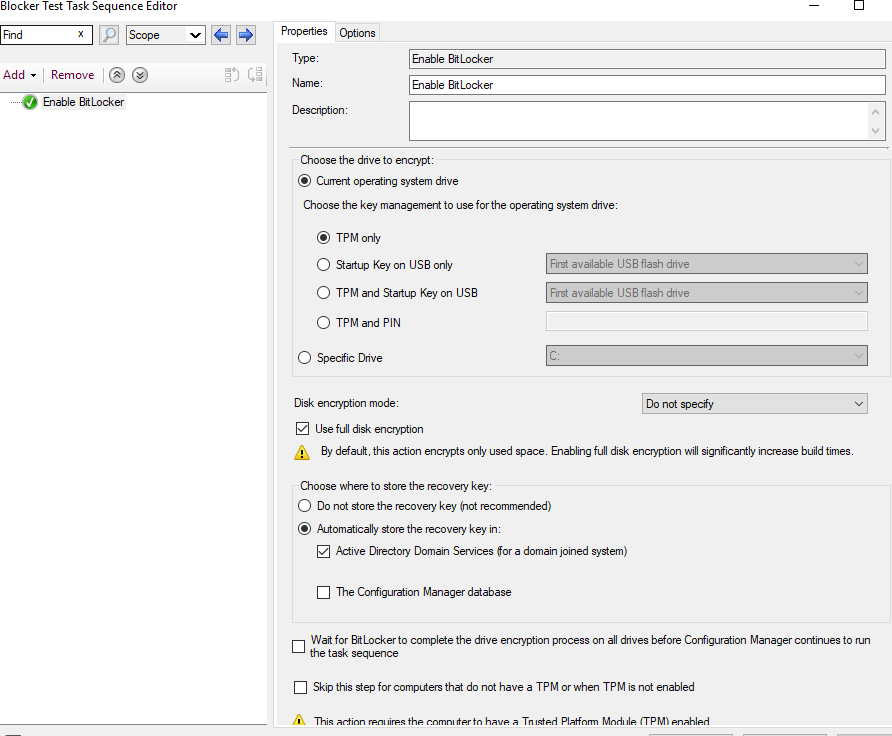
It worked in few minutes on both Secure Boot Enabled and Disabled devices. I know the supremacy of MECM in many aspects, but the general decision is to unify security and some policies in one place, that would be cloud. This means it is only a temporary solution... Can someone give me some hints what could I test later on when I will be trying to do it via cloud again?


