Thank you for posting your question in Microsoft Q&A.
By looking at the issue it seems that Azure AD is not sending the user role as claim in the token sent to your application.
Not sure what is the protocol you have used to configure Blazor application.
Thinking that you have used SAML protocol, you can use below steps to pass user role as a claim to application.
I have tested this in my lab and it working as expected. To pass the user role as claim you don't have to specifically create additional claim. Roles that will be passed in SAML tokens are defined in application. Azure AD roles cannot be passed in SAML token. Only roles that are defined in application and the roles which are assigned to users when you assign users to application can be sent as a claim in SAML token.
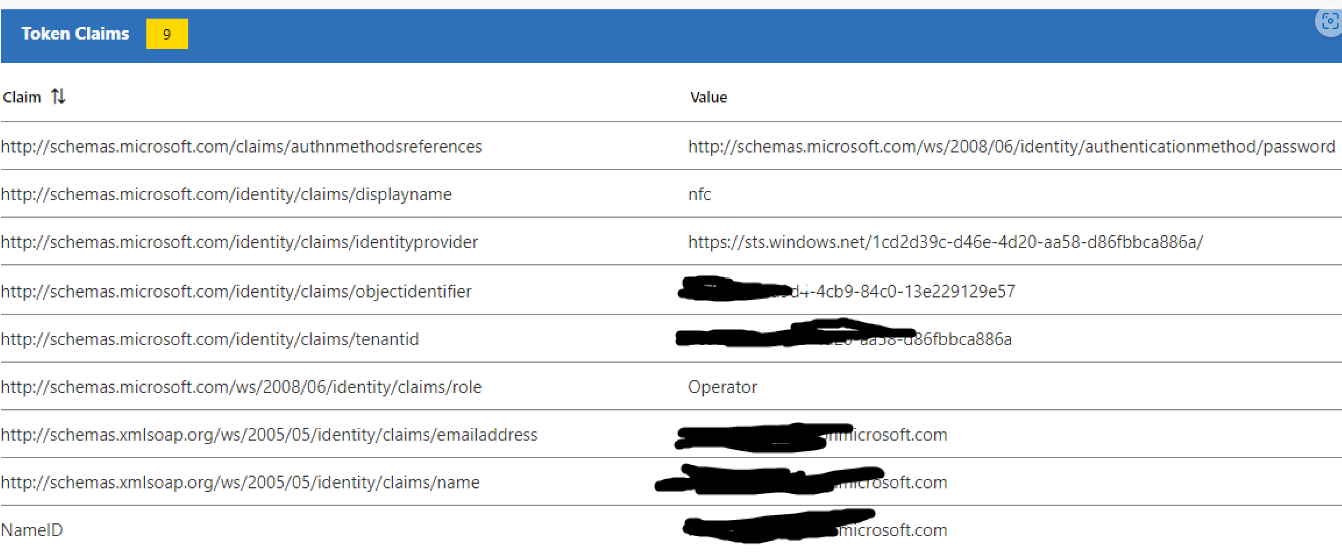
If you do not have any application roles defined, then you can refer below article to create roles using graph explorer,
https://learn.microsoft.com/en-us/azure/active-directory/develop/active-directory-enterprise-app-role-management
Do let us know if you have any further questions on this.
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.