Hello @PaulVyile,
Thanks for posting your query on Microsoft Q&A. From your description I could understand that you want to:
Exclude the remote desktop web client from MFA triggered due to integration of Network Policy Server (NPS) infrastructure with Azure AD Multi-Factor Authentication
Please correct me if this is not the case by responding in comments section else follow below suggestions:
- Select the MFA policy you would have created per: https://learn.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-nps-extension#register-users-for-mfa.
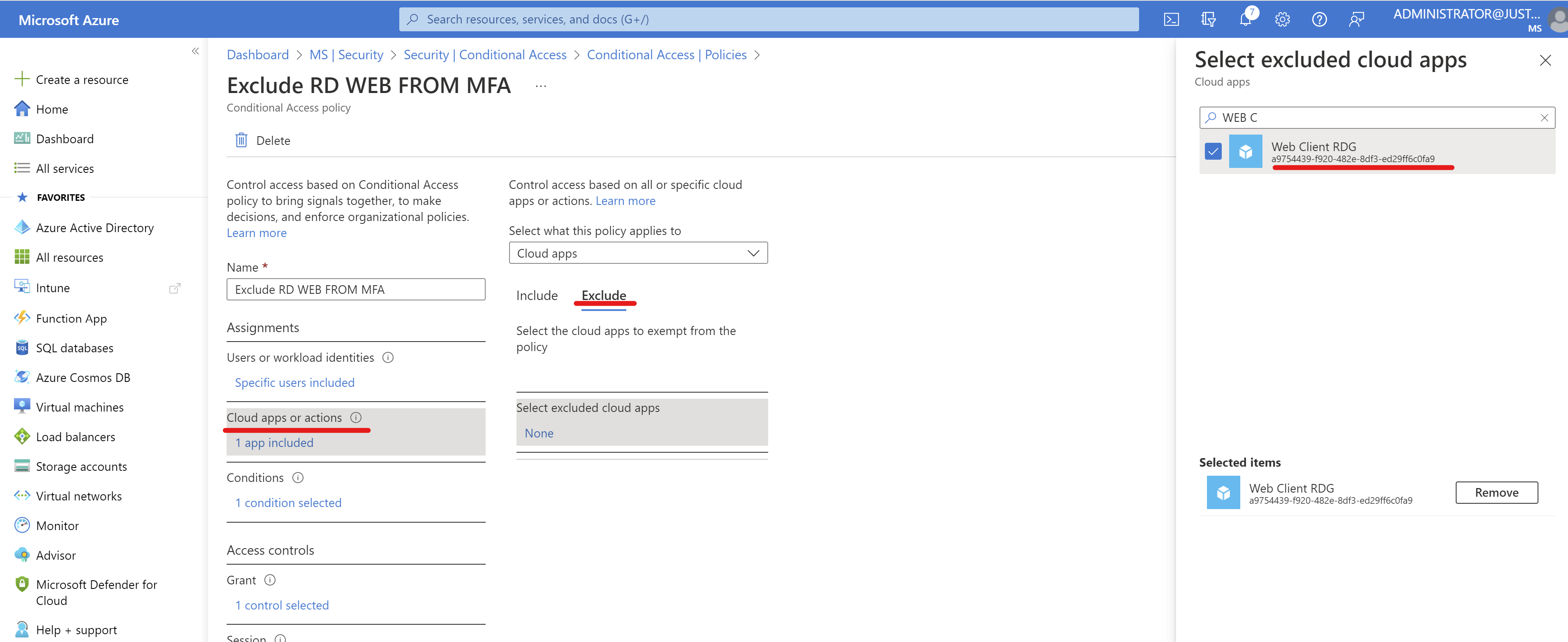
- Navigate to Cloud Apps or actions, under "Exclude" look for the application proxy name you registered the RD Web client with, ref step: https://learn.microsoft.com/en-us/azure/active-directory/app-proxy/application-proxy-integrate-with-remote-desktop-services#publish-the-rd-host-endpoint
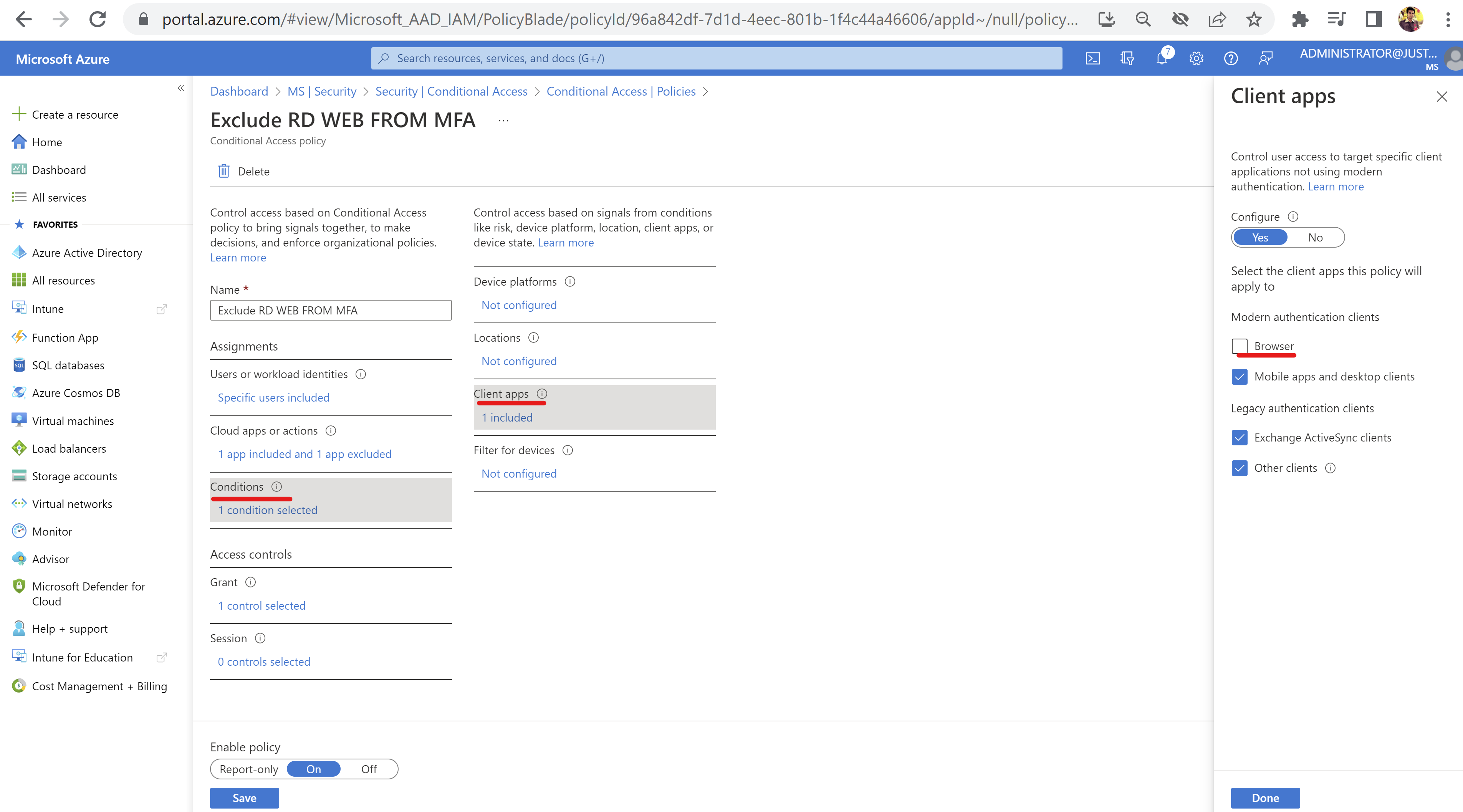
- Then select Conditions > Client Apps > Keep "Browser Clients" unchecked and check all other options, this will enforce the CA policy for MFA only on non-browser clients:
Thanks,
Akshay Kaushik
Do let me know if you have any queries in the comments section OR please "Accept the answer" if the information helped you. This will help us and others in the community as well.

