
Everythin has started to work when I moved the settings from custom GPO to Default Domain Policy.
Looks like a bug in Group Policies
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
I have been trying to set Advance Audit Policy to our servers through GPO but they are not getting applied. I have already set Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings. to Enabled and also appears in RSOP.msc of the servers. The audit policies are not getting applied however. I ran auditpol.exe /clear and then ran gpupdate /force. Now when I check with auditpol.exe /get /category:* almost all appear as No Auditing.
We are monitoring servers in Azure Security Center and it is recommending us to enable certain Audit policies to be ISO 27001 compliant. But these policies are not getting applied. Please let me know what is the problem here, I will list the audit policies below. The correct GPO is also applied so no question their.
Everythin has started to work when I moved the settings from custom GPO to Default Domain Policy.
Looks like a bug in Group Policies
Hello,
Thank you so much for posting here.
Have you linked the GPO to an OU containing the servers? To check the policy applied or not, we could run gpresult /h C:\report.html to get the group policy report.
If you use Advanced Audit Policy Configuration settings, you should enable the Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings policy setting under Local Policies\Security Options. This will prevent conflicts between similar settings by forcing basic security auditing to be ignored.
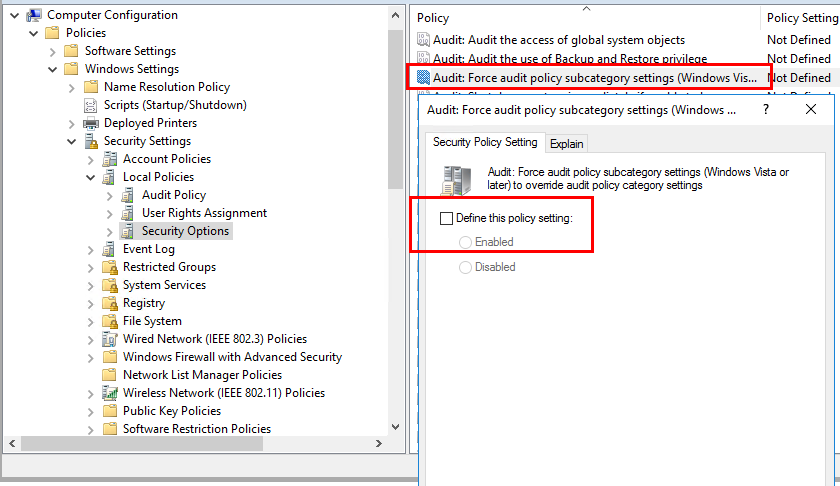
More information: https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/dd772710(v=ws.10)?redirectedfrom=MSDN
For any question, please feel free to contact us.
Best regards,
Hannah Xiong
============================================
If the Answer is helpful, please click "Accept Answer" and upvote it.
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.
Hello,
Thank you so much for your kindly reply.
According to our description, the policies are applied to the servers in Azure Security Center. We mainly focus on on-premise AD, as for our issue, I discussed with my AAD colleagues. Did we configure the GPO in AAD domain? Besides, the servers in Azure Security Center are joined to the AAD domain, right?
If there is any misunderstanding, please let me know. Thanks.
If the configuration is correct and the GPO is applied as shown in the gpresult, it is suggested that we could enable GPSVC debug logging to further troubleshoot.
1.On problematic machine, create the “usermode” folder under “%windir%\debug\” directory.
2.Create the following registry keys:
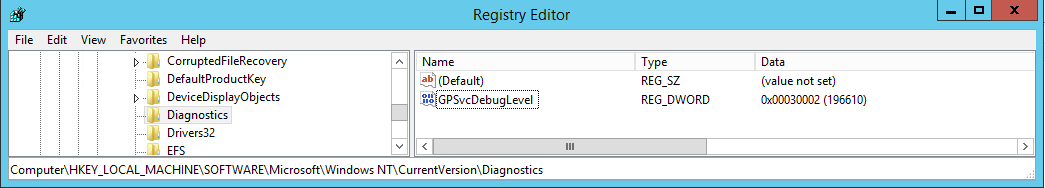
Under HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion , create a new Key “Diagnostics” there
3.Then create a new value “GPSvcDebugLevel” under the key “Diagnostics”:
Entry: GPSvcDebugLevel
Type: REG_DWORD
Value data: 30002 (Hexadecimal)
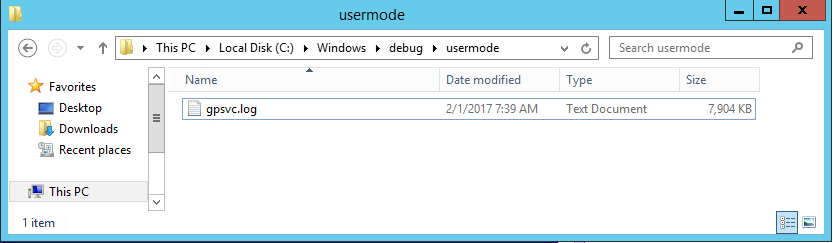
At this point, use the GPSVC analysis blog to get further:
Please note: Due to forum rules and security considerations, we do not analyze logs here.
Thank you so much for your understanding and support.
Best regards,
Hannah Xiong