Hello,
Thank you so much for posting here.
As far as I know, the built-in domain administrator account will not be locked out actually. It still could be successfully logged in as soon as the correct password is used.
I did the test in my lab. Configured the account lockout policy as shown below. Logged on to the BDC with the domain admin account and typed the wrong password many times. There were events logged on the BDC as shown below.
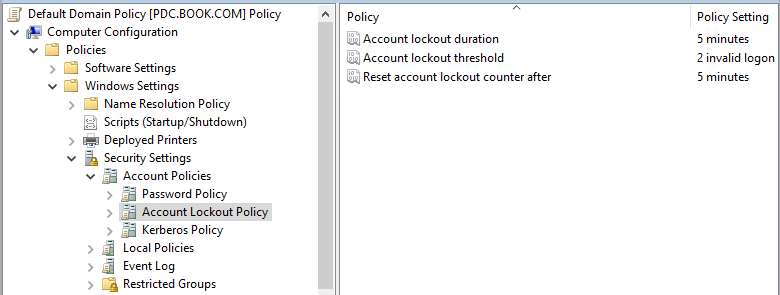
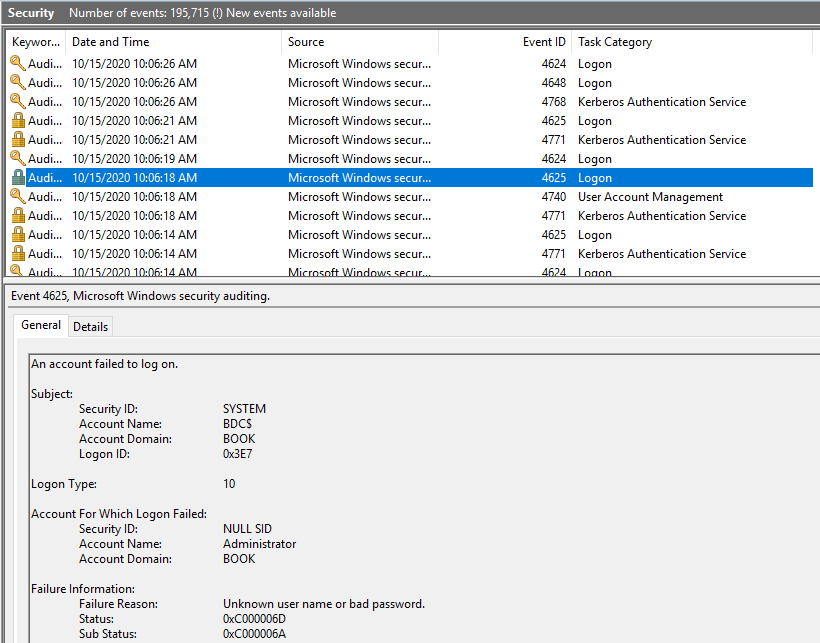
Then on the PDC, I could see the event ID 4740 and 4771. Even though there is event 4740, the admin account could still be logged in as soon as the correct password is used.
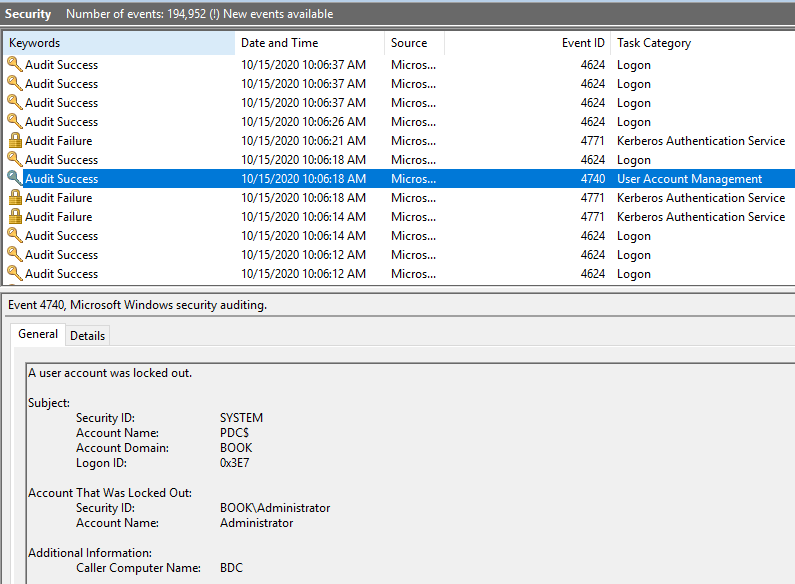
Do we see the 4771 or 4776 event log (including the user's account name and the error code is 0X18 or 0xc000006a) near the 4740 event? Besides, we could try to reset its password to see whether it could solve the issue.
For any question, please feel free to contact us.
Best regards,
Hannah Xiong
============================================
If the Answer is helpful, please click "Accept Answer" and upvote it.
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.



