Hi,
You can try 2 options to block the deletion permission:
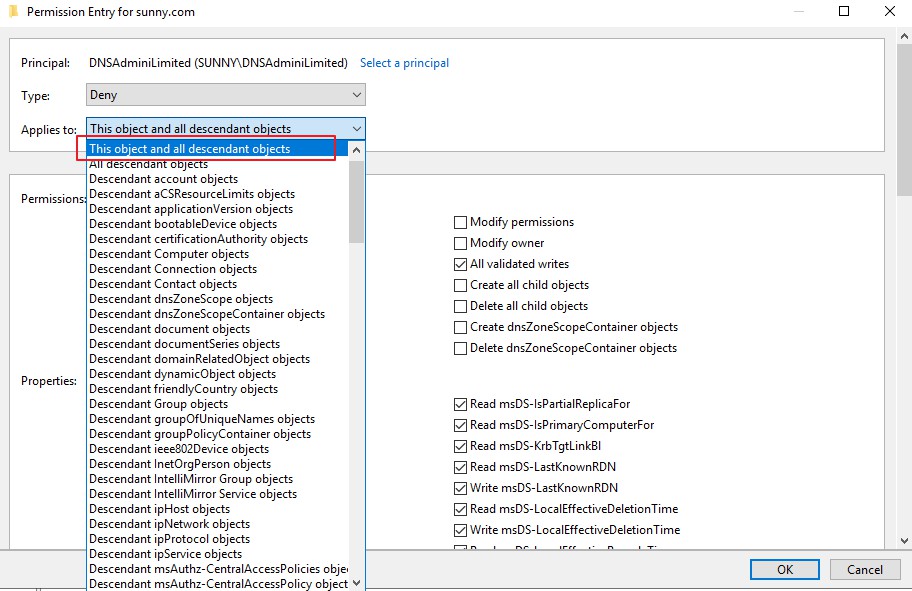
- Go to DNS zone properties , then security tab where you can check deny for delete permission:
You can on security tab go to advanced and uncheck the delete permission:
You can see attached images.
----------
Please don't forget to mark helpful reply as answer [2]: /api/attachments/61539-image.png?platform=QnA