@PRUTHWIRAJ JAGADALE
Thank you for your detailed post!
Within the article that you referenced - Azure AD Multi-tenant Apps: API Chains and Cyclic Dependencies, the author ran into the same error message you did. However, they were able to resolve their issue a little further down, as seen in the screenshot below.
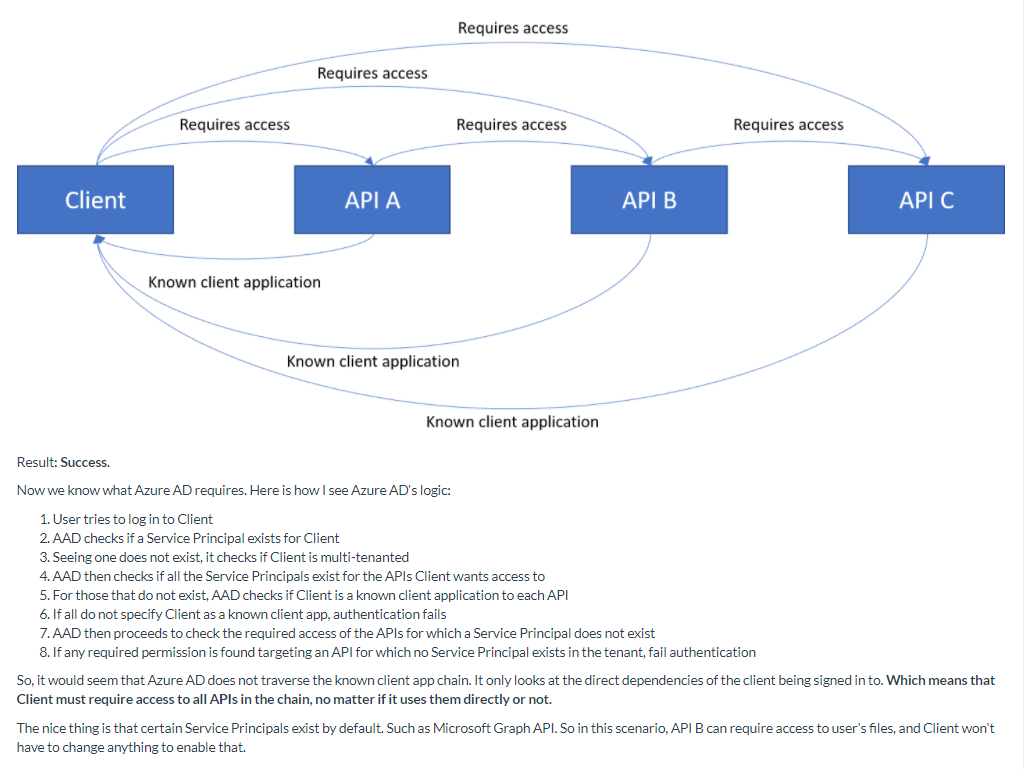
The author also describes in their conclusion that: "based on my experiments, Azure AD does not traverse API chains to gather the permissions required for consent. It only checks the direct dependencies of the client. So make sure that your client requires access to all the APIs in the chain. And then also ensure the client is a known client application of all the APIs. The APIs in the chain should still require access to the APIs they need to use. But they do not need to be known clients of them."
I hope this helps!
Thank you for your time and patience throughout this issue.
----------
Please remember to "Accept Answer" if any answer/reply helped, so that others in the community facing similar issues can easily find the solution.
