Hi,
Thanks for your feedback.
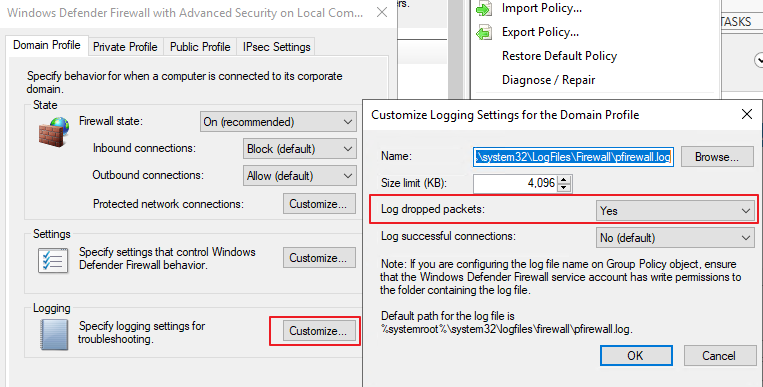
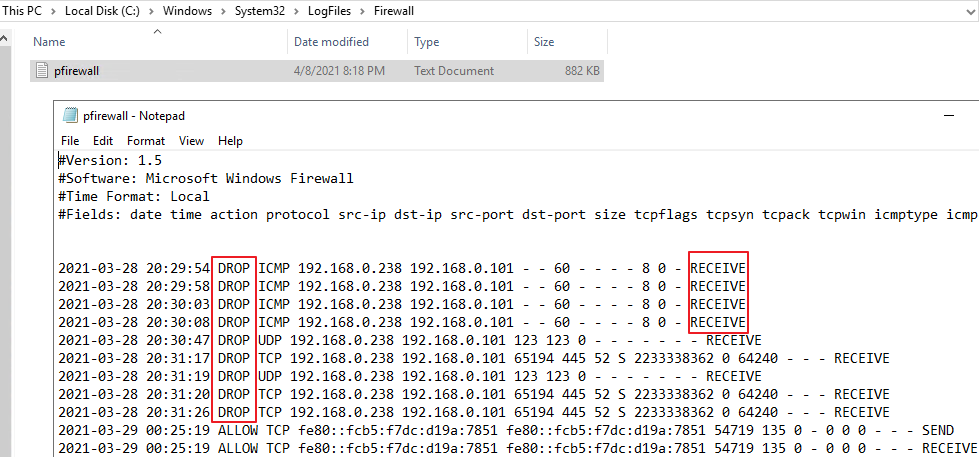
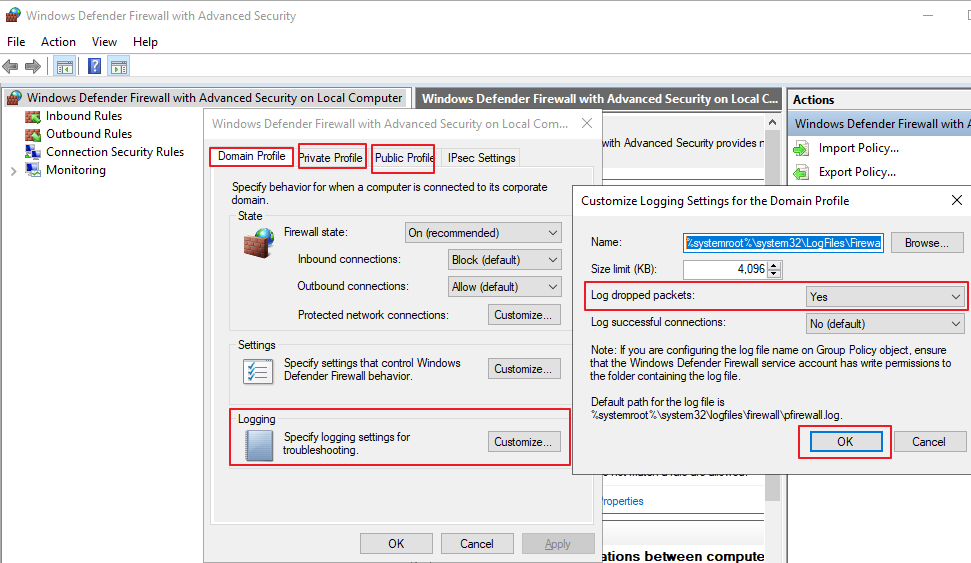
I understand the rule is actually configured for domain, private and public profiles. If you want to check whether this rule is taking effect in our firewall, we need check firewall log, and the firewall log need be enabled for domain, private and public profiles separately. I noticed that the firewall for domain profile in your environment has been disabled, so you need enable firewall log for private and public profiles for checking.
As for there are so many traffic from 5.188.xxx.xxx were triggered, it's an expected behavior. Please allow me explain an similar example for you to explain the workflow of windows firewall. For example, you have a friend who is the person you don't like, but he/her wants to contact you by sending letter to you. You don't know when will he/her send this letter to you, you can receive his/her letter anyhow, however, when you received this letter, you have the right to reject this letter or return it to sender.
Meanwhile, based on my research, is it possible that these IP address are belongs to mail servers? You could try to add these IP to black list to see if the issue can be resolved.
Hope my answer will help you. Thank you for your understanding.
Best Regards,
Sunny
----------
If the Answer is helpful, please click "Accept Answer" and upvote it.
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.