Hello @Naveen Begur nagaraj ,
Thanks for reaching out.
Could you please confirm, are you creating a "New Policy definition" or "assigning existing policy?
Looking at above error which appears to be pipeline creating New Policy definition along with definition Name parameter value which exceed 64 characters rather than assigning existing policy .
You must use New-AzPolicyDefinition for Create a policy definition and New-AzPolicyAssignment for Policy assignment so could you please confirm PowerShell cmdlets that you were used within Azure Devops pipeline for assignment?
Here are some example for creating new policy definition and Policy assignment:
Example: Create a policy definition
New-AzPolicyDefinition -Name 'VMPolicyDefinition' -DisplayName 'Virtual Machine policy definition' -Policy '{"if":{"field":"type","equals":"Microsoft.Compute/virtualMachines"},"then":{"effect":"deny"}}'
Example: Policy assignment
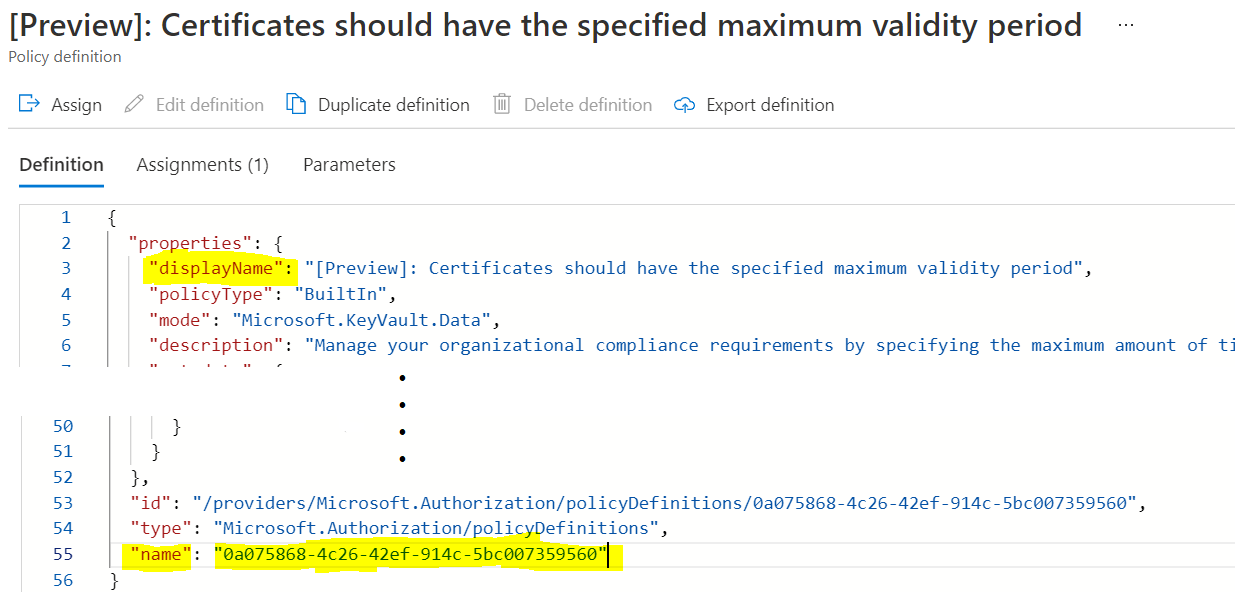
$definition = Get-AzPolicyDefinition | Where-Object { $_.Properties.DisplayName -eq '[Preview]: Certificates should have the specified maximum validity period'}
New-AzPolicyAssignment -Name "DenyKeyVaultCert" -PolicyDefinition $definition
*Note: You can assign build-it policy definition directly rather than creating newly , following is one of the built-in policy definition [Preview]: Certificates should have the specified maximum validity period *
In above cmdlets in both example, the policy definition Display Name has the name length limit of 128 characters and policy Definition Resource Name has the limit of 64 characters.
Policy Definition Display Name :
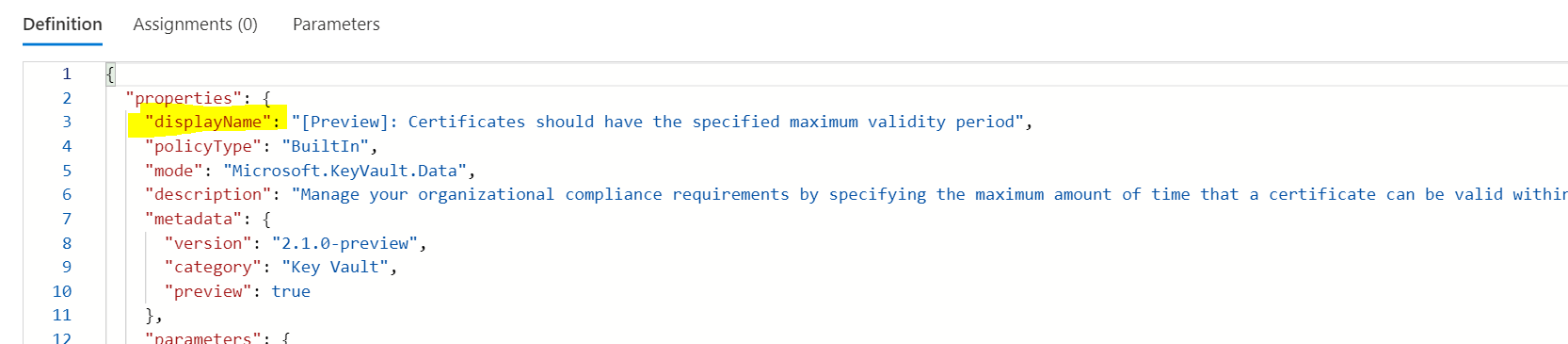
Policy Definition Resource Name :
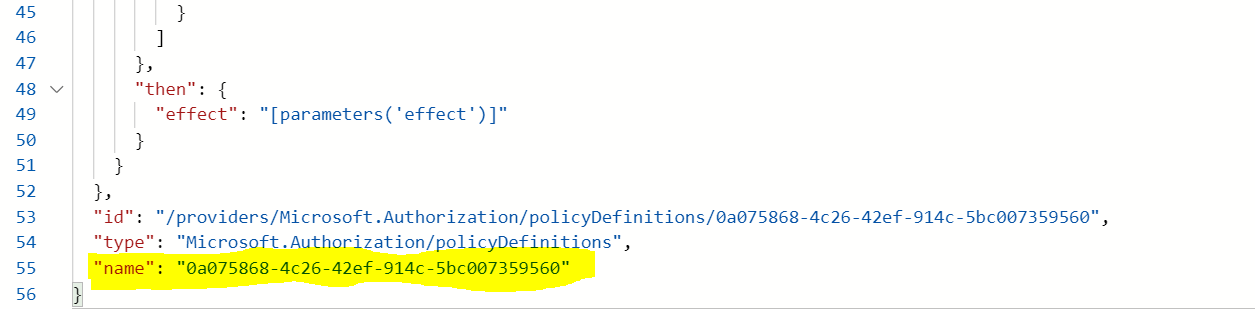
This limitation is by design and you need to limit the name accordingly. Please refer this article for reference.
So please make sure you don't exceed Max. allowed character length for Display Name and policy Definition Resource Name while creating/assigning policy definition.
Its worth referring to this article: https://techcommunity.microsoft.com/t5/azure-paas-blog/azure-policy-perform-policy-operations-through-azure-devops/ba-p/2045515
Hope this helps.
------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.