Hello! I'm almost done configuring my conditional access test and I want to confirm I'm reading the Sign-In logs correctly. Specifically the Conditional Access Policy Results. I've added screenshots below.
My policy: For all locations Except the corporate network, prompt for MFA. I currently have it setup for one user only when logging into office.com.
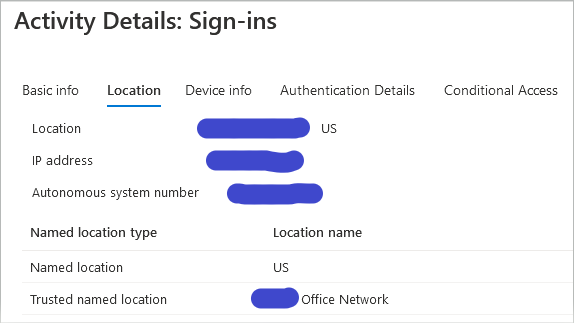
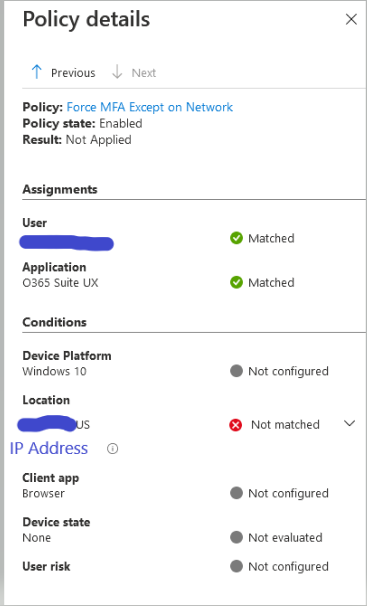
The first image shows the sign-in log's Location Tab. It shows the Trusted Network listed. However, the second image (same Sign-In Log) shows the Conditional Access evaluation fails at the Location with a "Not Matched" result.
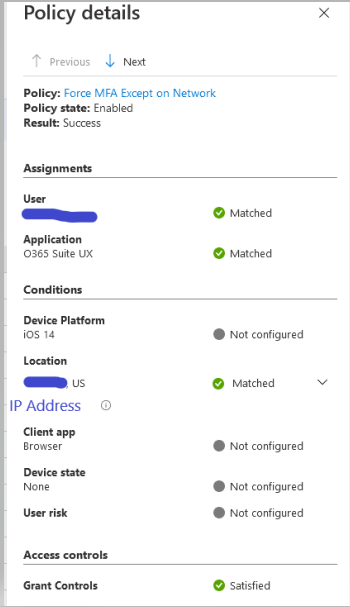
The third image is a login off the corporate network. I used the cellular data on my personal phone. I was successfully prompted for MFA.
Shouldn't the Corporate Network login read "Matched" because the log in came from the Trusted Network? I'm getting the desired result, but I'm worried I won't be reading the policy evaluations correctly when moving forward and adding more and more policies.