I am stuck on the Intune enrollment process. The computers in the domain are all AAD, however, when the GPO that i created to enroll AAD devices into Intune runs, it fails with the multiple errors:
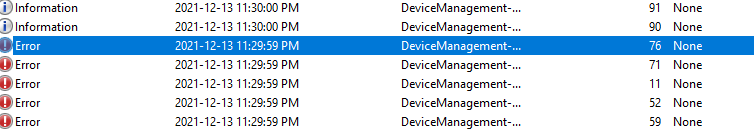
Event ID: 71 - MDM Enroll: Failed
Event ID: 76 - Auto MDM Enroll: Device Credentials (0x0) Failed
Event ID: 11 - MDM Enrollment: Failed to receive or parse cert enroll response.
Event ID: 52 - MDM Enroll: Server returned Fault/code/subcode/value=(messageformat) fault/reason/text=(device based token is not supported for enrollment type onpremisegrouppolicycomanaged).
Event ID: 59 - MDM Enroll: server context
The one thing that is different about this environment, is that their local domain is: CompanyA.local and their tenant domain is Company123.com. Under the local domain, i made sure that the new UPN for the tenant was there. But that did not make a difference when i manually resync'd the process. This is a hybrid environment with an AD connect server.
As for the GPO, i have set it from Device to Client to see if it makes a difference - and nothing.
By the way, this new GPO object has an application id. Not sure what that is, so i left it blank.
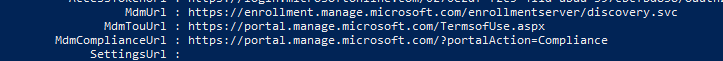
When i run a dsregcmd /status - AzureAD joined is YES and so is DomainJoined. What is a bit strange, is that under Tenant Details, the mdmurl section is blank.
I have pretty much done everything that i can find on this forum and elsewhere but i cannot get the devices to enroll successfully into Intune/Endpoint manager.
Thanks in advance.