Hi,
Based on experience, you are right .
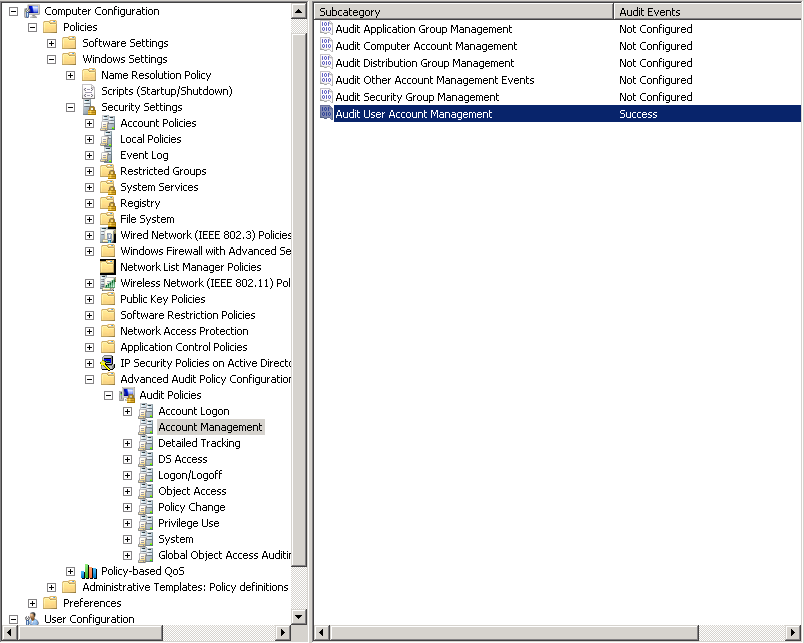
If you can't find any events about the account lockout , then we need to enable the audit policy on the Domain controllers under[Computer Configuration\Windows Settings\Security Settings\Local Policies\Audit Policy\Audit account management]
You can enable or disable it as your requirements.
According to the audit events on PDC determine which clients or DCs sent the failed authentication request. If the failed authentication request was sent by a DC, then we should gather the audit event on the DC. So we can find out which clients sent the BAD password.
After we get the workstations IP, then we need enable Audit Logon Events – Failure and Audit Process Tracking for this client, then analyze the event log to find out which process or apps send the BAD passwod.
Best Regards,