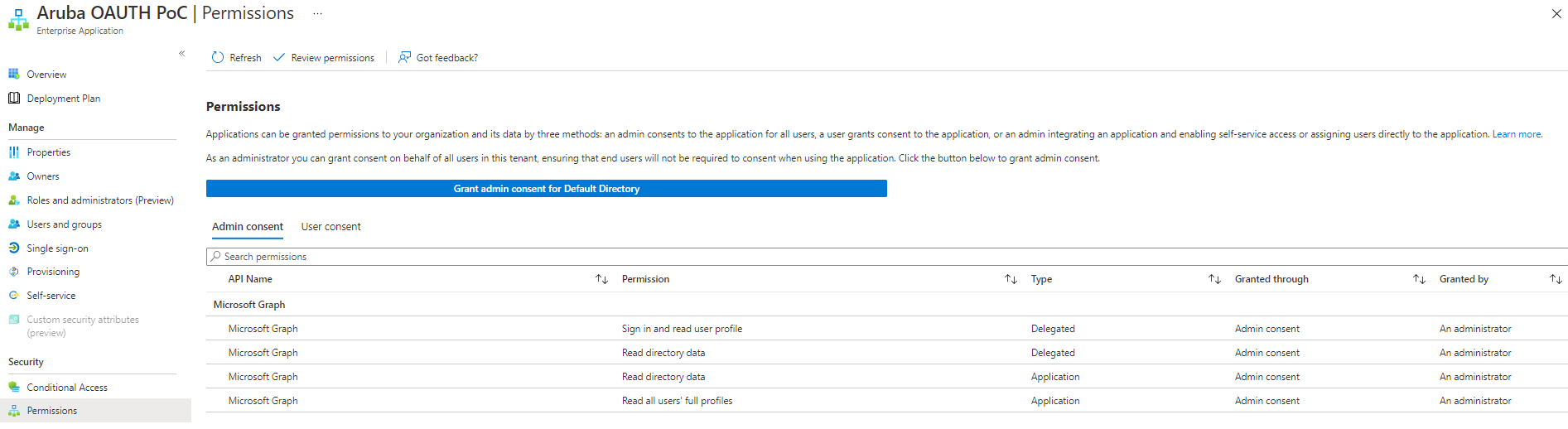
Hi @Kamen
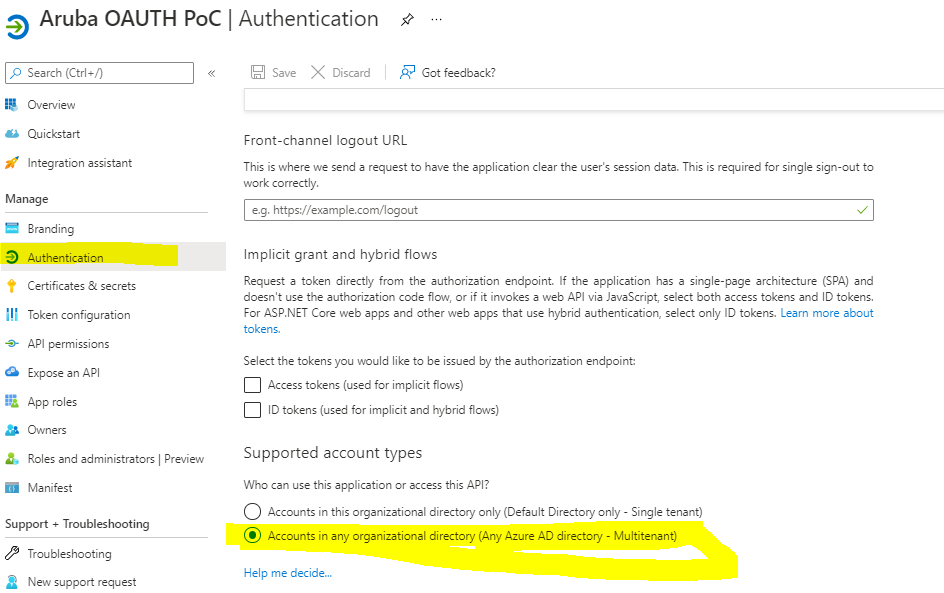
First, make sure your application has been registered as a multi-tenant application in the original tenant.
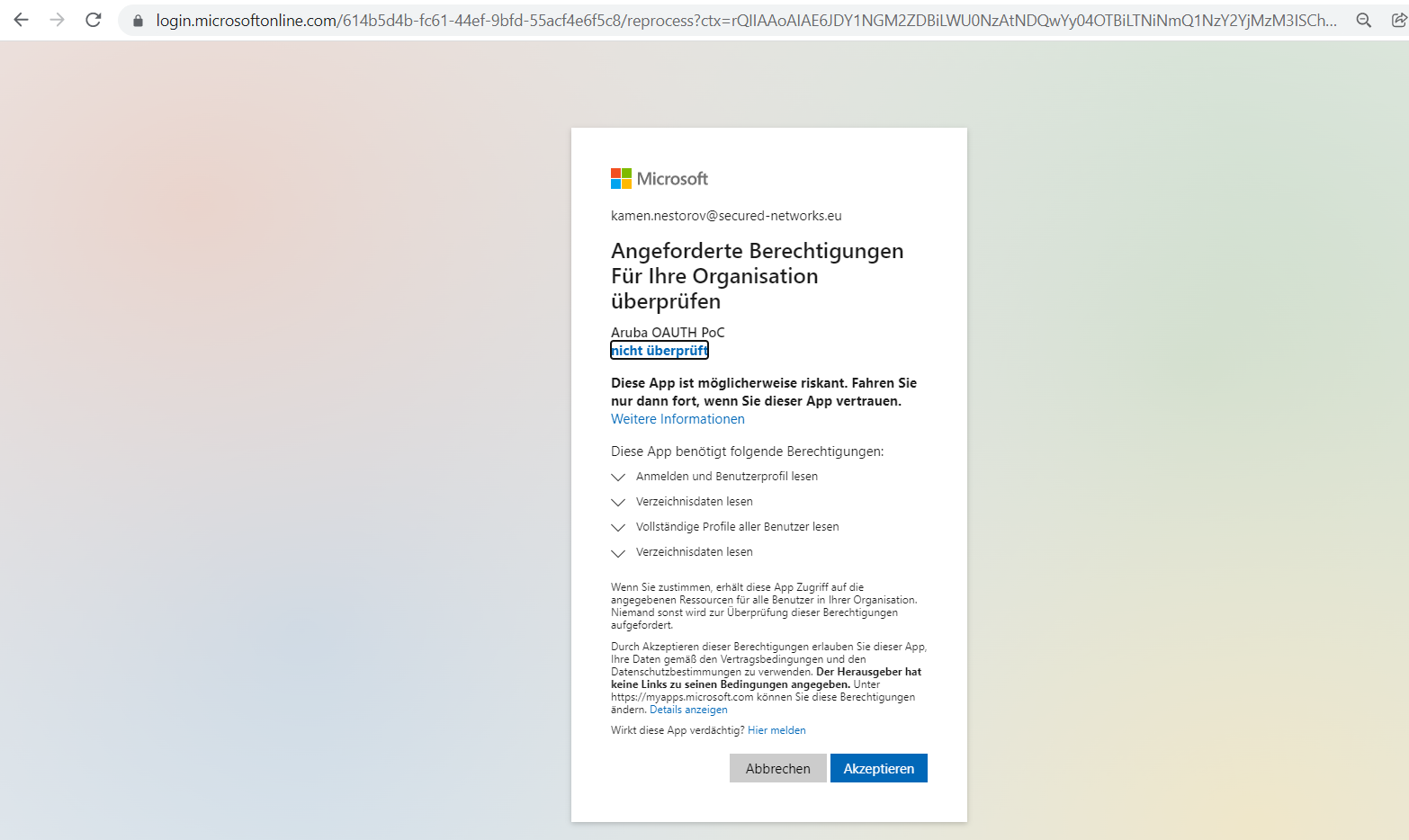
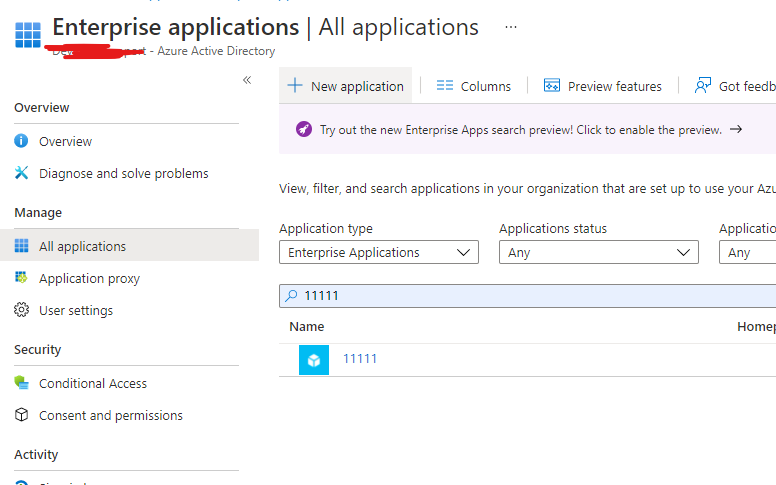
Next you need to run the admin consent url: https://login.microsoftonline.com/{target-tenant-id}/adminconsent?client_id={client-id} in your browser and log in the administrator of the target tenant and consent, after that the multi-tenant application will be added to the target tenant as an enterprise application, and it will also have the permissions you granted in the original tenant.
Finally you will be able to log in to the multi-tenant application with a user in the target tenant.
https://login.microsoftonline.com/{target tenant id}/oauth2/v2.0/authorize?
client_id={client app client id}
&response_type=code
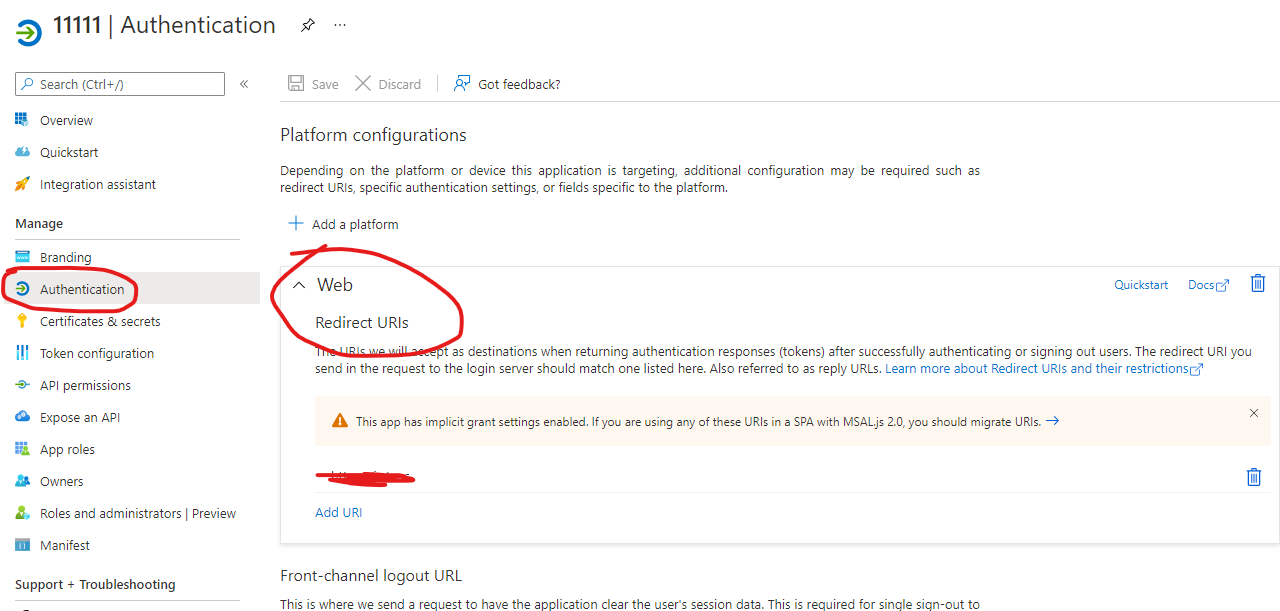
&redirect_uri={redirect_uri}
&response_mode=query
&scope=https://graph.microsoft.com/.default
&state=12345
If the answer is helpful, please click "Accept Answer" and kindly upvote it. If you have extra questions about this answer, please click "Comment".
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.