@Santi
Thank you for your post!
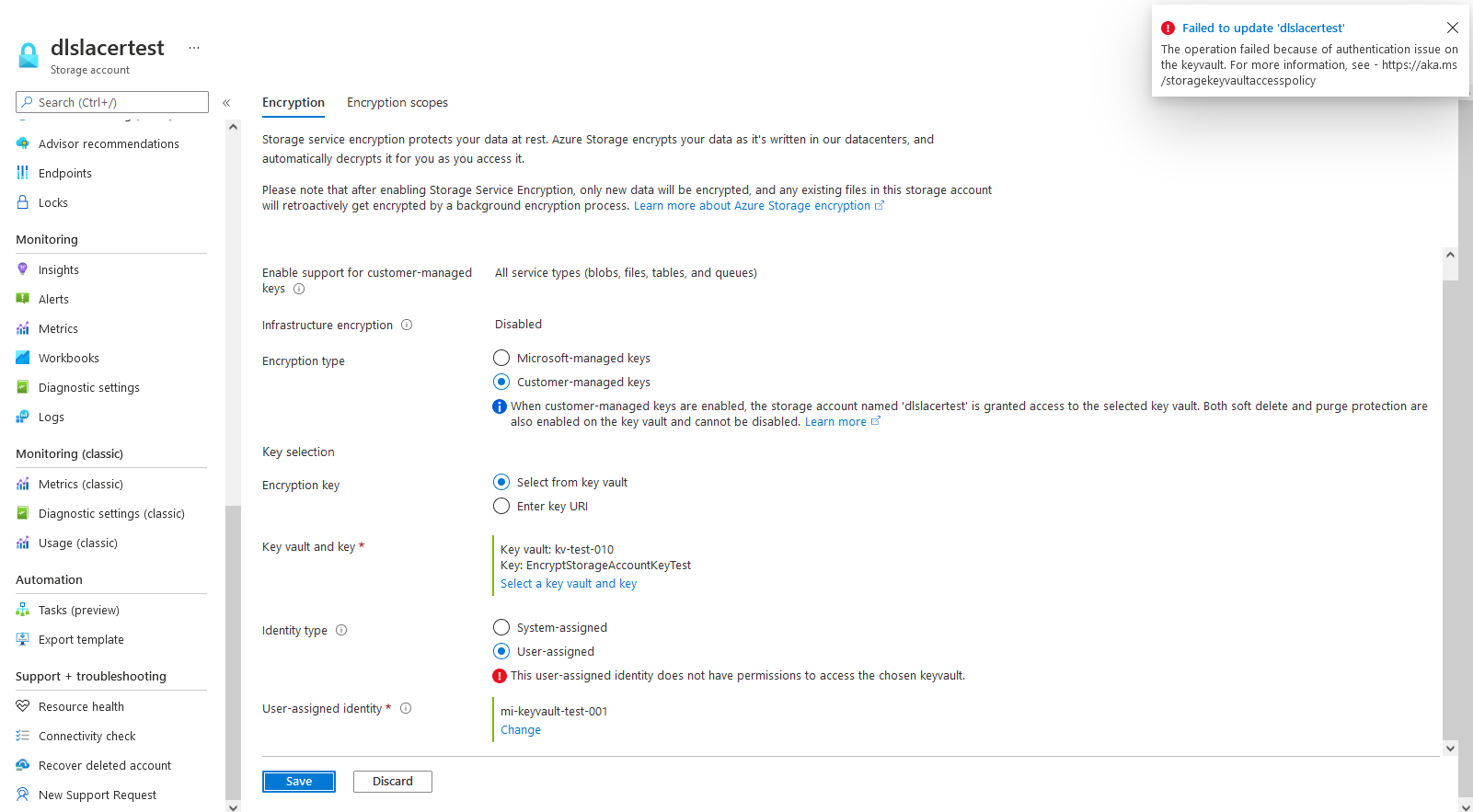
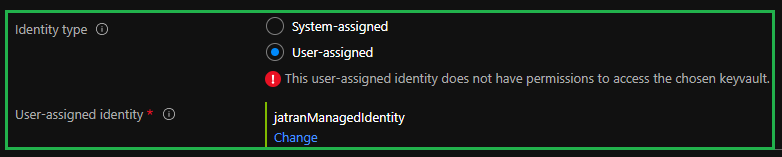
From the article https://aka.ms/storagekeyvaultaccesspolicy within your error, the managed identity mi-keyvault-test-001 doesn't have the proper permissions to access Key Vault kv-test-010.
Troubleshooting:
Following the Configure encryption with customer-managed keys stored in Azure Key Vault documentation, you'll need to add your managed identity to your Key Vault's access policies.
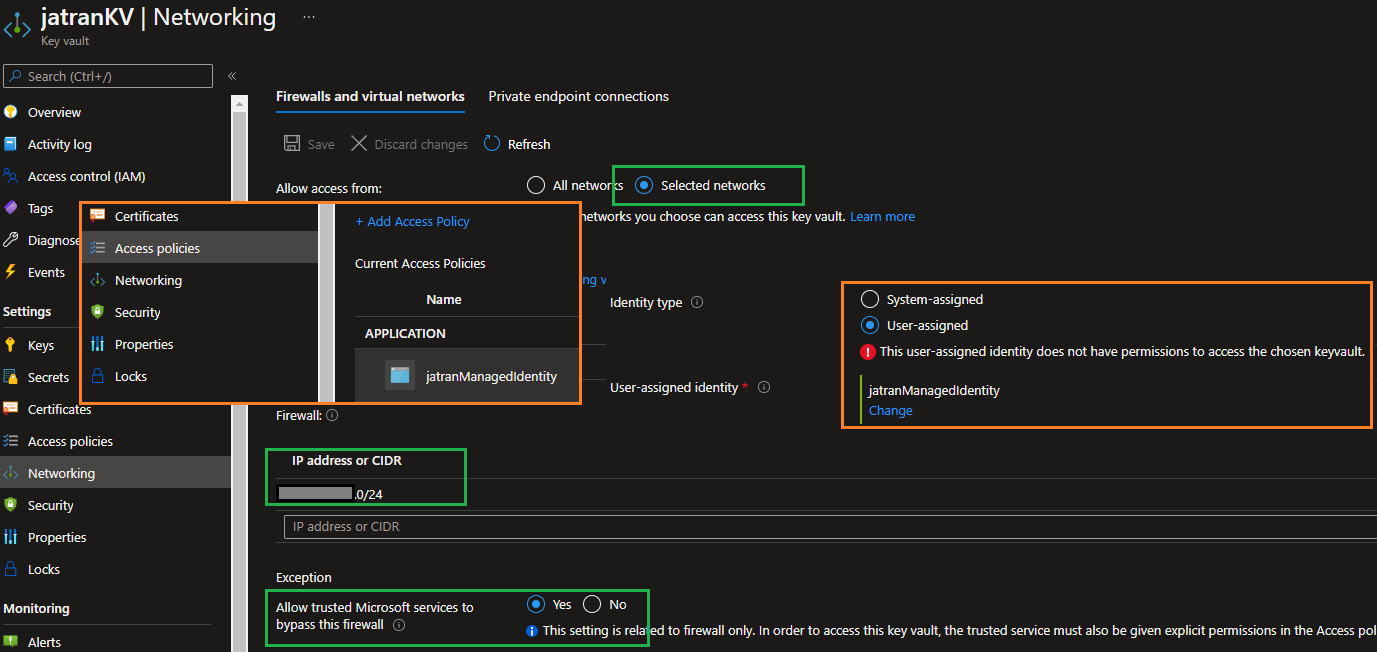
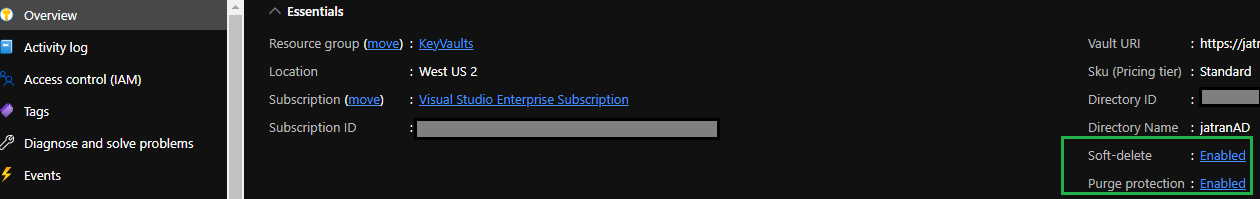
1) Navigate to your Key vault kv-test-010
2) From the Overview page, confirm Soft-delete and Purge Protection are enabled for your vault, since this is required by Azure Storage encryption.
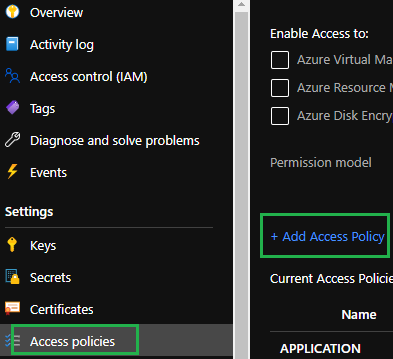
3) Select Access Policies, then Add Access Policies.
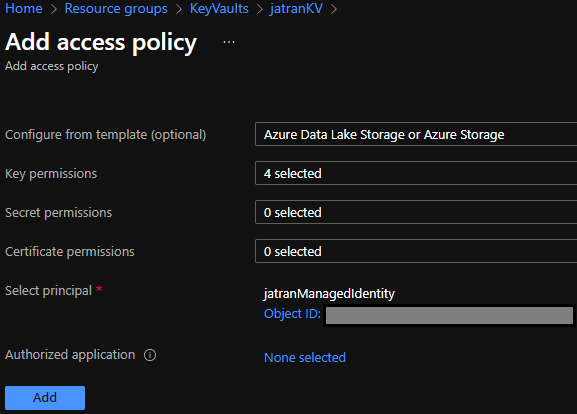
4) Select the permissions you'd like your Managed Identity to have. I selected the Azure Data Lake Storage or Azure Storage template.
5) Select your managed identity mi-keyvault-test-001 as the principal. Select Add, then Save.
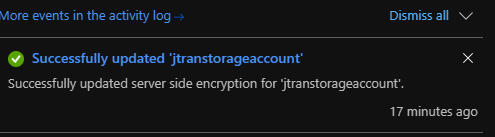
6) Navigate to your Storage account and retry the operation.
If you have any other questions, please let me know.
Thank you for your time and patience throughout this issue.
Please remember to "Accept Answer" if any answer/reply helped, so that others in the community facing similar issues can easily find the solution.