Hi @rdth ,
Thanks for using Microsoft Q&A!!
If I understand correctly, you want to provide access to managed identity of your ADF to ADLS Gen2 based storage linked service.
In order to do so, you need to either use PowerShell cmdlet -New-AzRoleAssignment or CLI cmdlet - az role assignment create. You can either provide "Storage Blob Data Reader" or "Storage Blob Data Contributor" role to grant access as per the documentation Storage Gen2 - System-assigned managed identity authentication for source or sink purpose.
Your PowerShell/CLI command will look like below -
New-AzRoleAssignment -ObjectId "{ADF-Managed-Identity-Id}" -RoleDefinitionName "Storage Blob Data Contributor" -Scope "/subscriptions/{Subscription Id}/resourceGroups/{Resource group Name}/providers/Microsoft.Storage/storageAccounts/{Storage Account Name}"
OR
az role assignment create --assignee "{ADF-Managed-Identity-Id}" --role "Storage Blob Data Contributor" --scope "/subscriptions/{Subscription Id}/resourceGroups/{Resource group Name}/providers/Microsoft.Storage/storageAccounts/{Storage Account Name}"
Here, you can get the managed identity of your ADF from linked service popup blade from ADF UI.
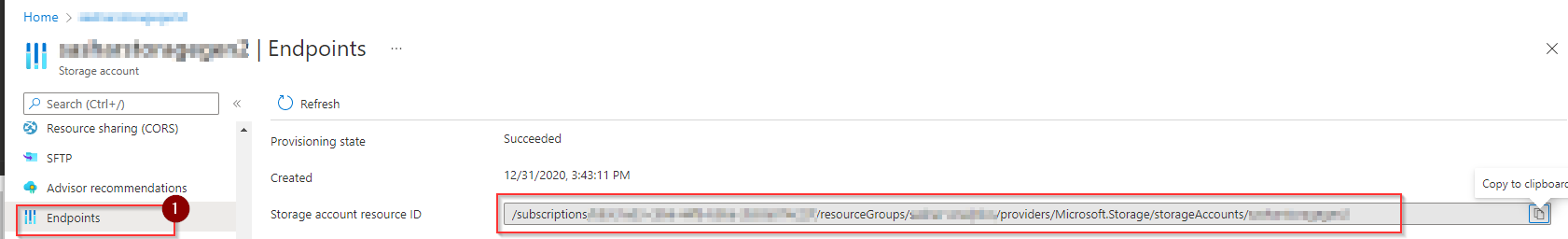
You can get the resource scope of the storage account by going to Azure Portal > ADLS Gen2 Storage Account Name > Endpoints
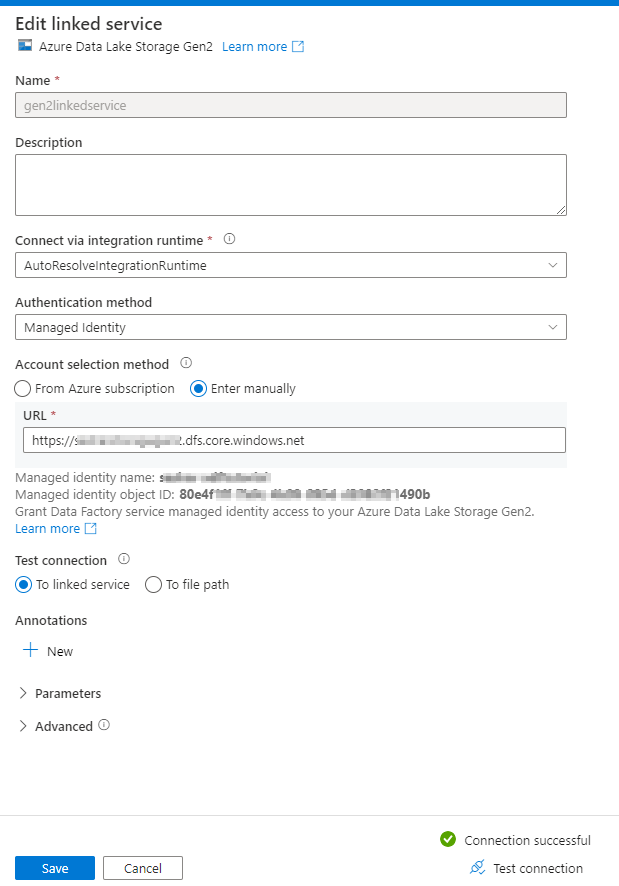
Once proper permissions are granted, you should be able to validate the Linked Services -
Please refer to below documents for additional details -
Please let me know if you have any questions.
Thanks
Saurabh
----------
Please do not forget to "Accept the answer" wherever the information provided helps you to help others in the community.
