@Gómez González María
Thank you for your post!
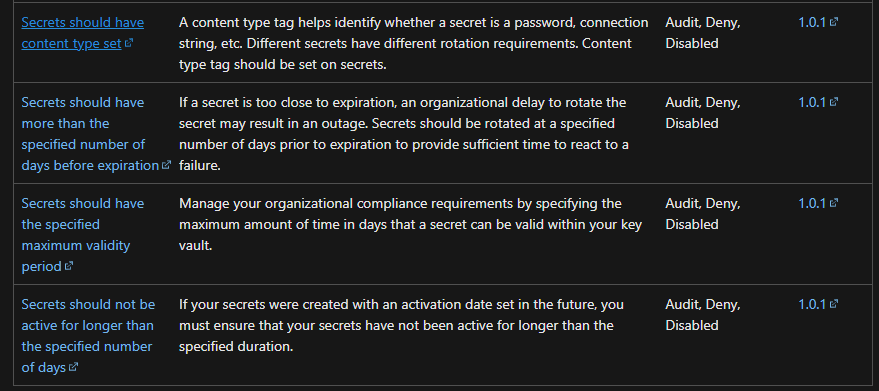
When it comes to creating a policy where Secrets should have a defined expiration date and not be permanent, you should be able to do this via the Azure Policy built-in definitions for Key Vault.
Key Vault secrets should have an expiration date:
"properties": {
"displayName": "Key Vault secrets should have an expiration date",
"policyType": "BuiltIn",
"mode": "Microsoft.KeyVault.Data",
"description": "Secrets should have a defined expiration date and not be permanent. Secrets that are valid forever provide a potential attacker with more time to compromise them. It is a recommended security practice to set expiration dates on secrets.",
"metadata": {
"version": "1.0.2",
"category": "Key Vault"
},
"parameters": {
"effect": {
"type": "String",
"metadata": {
"displayName": "Effect",
"description": "'Audit' allows a non-compliant resource to be created, but flags it as non-compliant. 'Deny' blocks the resource creation. 'Disable' turns off the policy."
},
"allowedValues": [
"Audit",
"Deny",
"Disabled"
],
"defaultValue": "Audit"
}
},
"policyRule": {
"if": {
"allOf": [
{
"field": "type",
"equals": "Microsoft.KeyVault.Data/vaults/secrets"
},
{
"field": "Microsoft.KeyVault.Data/vaults/secrets/attributes.expiresOn",
"exists": false
}
]
},
"then": {
"effect": "[parameters('effect')]"
}
For your specific policy, it looks like you might have to change attributes.exp to /attributes.expiresOn:
"allOf": [
{
"field": "type",
"equals": "Microsoft.KeyVault.Data/vaults/secrets"
},
{
"field": "Microsoft.KeyVault.Data/vaults/secrets/attributes.expiresOn",
"exists": false
If you have any other questions, please let me know.
Thank you for your time and patience throughout this issue.
----------
Please remember to "Accept Answer" if any answer/reply helped, so that others in the community facing similar issues can easily find the solution.