We also got the same problem - seems like such a beginner issue, I can't believe MS didn't think of providing a solution for it. When auto-deployments fail at the second run because a role already exists and I cannot skip the step, then they are not much of an auto-deployment...
Azure Bicep authorization roleassignements to storage account fails with error The role assignment already exists
We are trying to assign a user-assigned managed identity to a storage account using Microsoft.Authorization/roleAssignments@2018-01-01-preview resource but it is failing and giving an error if the role already exists. we need to ignore the error to proceed ahead with bicep deployment. Is there any way to check if that role already exists on the resource and skip the assignment?
5 answers
Sort by: Most helpful
-
-
 JamesTran-MSFT 36,371 Reputation points Microsoft Employee
JamesTran-MSFT 36,371 Reputation points Microsoft Employee2022-05-23T21:06:21.75+00:00 @Kuldeep Bhatt
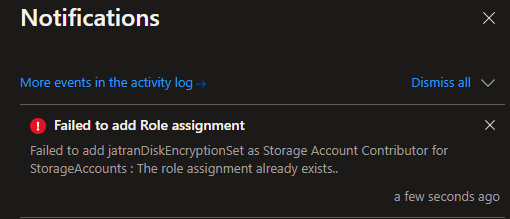
Thank you for your post and I apologize for the delayed response!For the RBAC side of things, if you're receiving an error similar to the below when deploying your resources with Bicep, you can check if the role already exists on the resource by navigating to Access Control (IAM).
Failed to add Role assignment:
Failed to add <<user-assigned managed identity name>> as <<RBAC role>> for <<Resource>>: The role assignment already exists
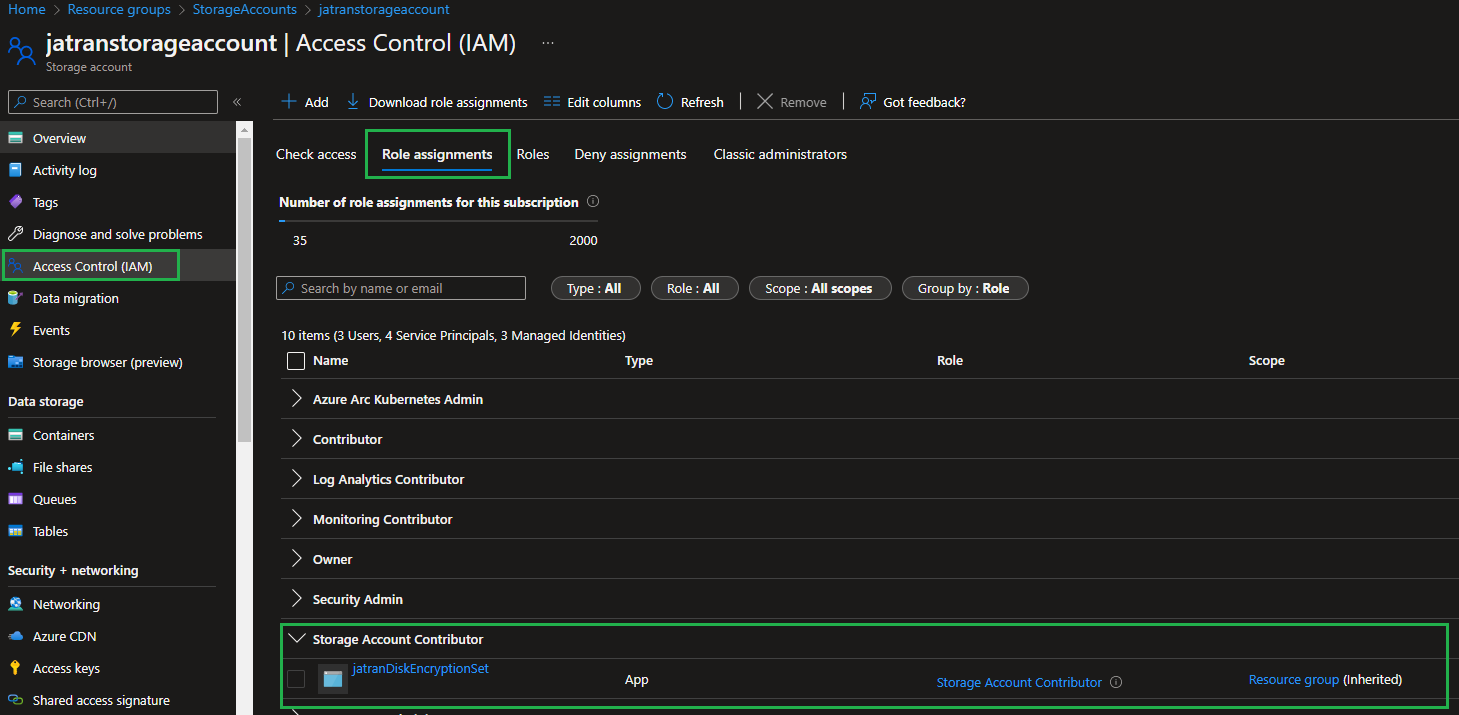
Check Role Assignment: Depending on the scope (Resource Group, Resource, etc.) that you're trying to assign the RBAC role at.
- Navigate to your Storage Account.
- In the navigation menu (left side), click
Access control (IAM). - Select
Role Assignments - Confirm that the User-Assigned Managed Identity has the correct role assigned
I hope this helps!
If you have any other questions, please let me know.
Thank you for your time and patience throughout this issue.----------
Please remember to "Accept Answer" if any answer/reply helped, so that others in the community facing similar issues can easily find the solution.
-
Quackenbush, Rich 1 Reputation point
2022-11-10T18:24:44.99+00:00 Any updates here? I just ran into the same exact problem. I'm using version
Microsoft.Authorization/roleAssignments@2022-04-01of the resource. -
FR5122022 1 Reputation point
2022-12-04T22:45:51.467+00:00 I have the same problem, second deployment fails - I'm using a Group rather that a managed identity.
The role assignment name is constant between deployments so it should check if it already exists?
The group I am adding is a contributor on the Resource Group.
I can successfully give managed identities and users the same role on the same storage account via the same method in bicep!var groupBlobDataReaderUniqueGuid = '0683f386-f9cc-4d28-b7be-71e9a1156009' var azureRBACStorageBlobDataContributorRoleID = 'ba92f5b4-2d11-453d-a403-e96b0029c9fe' resource r_storageBlobDataContributor 'Microsoft.Authorization/roleAssignments@2020-08-01-preview' = { name: guid(groupBlobDataReaderUniqueGuid, subscription().subscriptionId, resourceGroup().id) scope: r_storage properties:{ roleDefinitionId: resourceId('Microsoft.Authorization/roleDefinitions', azureRBACStorageBlobDataContributorRoleID) principalId: groupADObjectId principalType:'Group' } }This is the error message
{
"error": {
"code": "RoleAssignmentExists",
"message": "The role assignment already exists."
}
} (Code:Conflict)Frustrating!
-
Michal Fajta 5 Reputation points
2023-02-23T14:06:47.2366667+00:00 I found the answer here: https://learn.microsoft.com/en-us/answers/questions/1007498/microsoft-authorization-roleassignments-devops-ci
In the end I am testing now with unique resource name for each rerun with guid(utcNow())