Azure Firewall
An Azure network security service that is used to protect Azure Virtual Network resources.
578 questions
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.

Hey,
we are trying to find best practices for our alert-management in Azure. We have a next generation Azure firewall/Application Gateway/WAF and the OWASP rules activated.
Now we are trying to create "good" alerts to notify us. Does anybody have a set of rules they can share e.g. alert by 100 blocked requests/minute?
Thanks in advance!
Frank

Hi Frank,
I have some guidelines, but I prefer making my rules to match the required conditions for a given web site...
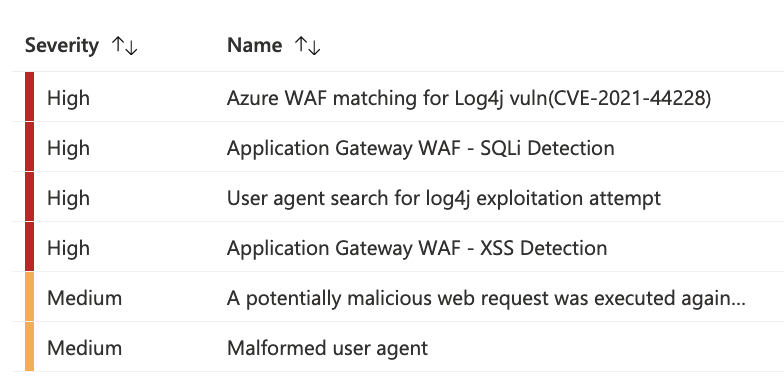
Guidelines:
Here are some common use cases for waf:
Good luck!