Hello @Lukas , Thanks for posting this query on this forum,
Please refer to these below documents and do let us know if you have further queries and we would be happy to help with Azure IoT Devices and x509 certificates.
If you delete an enrollment group for a certificate, devices that have the certificate in their certificate chain might still be able to enroll if an enabled enrollment group for the root certificate or another intermediate certificate higher up in their certificate chain exists.
Select Disable on the Enable entry switch, and then select Save.
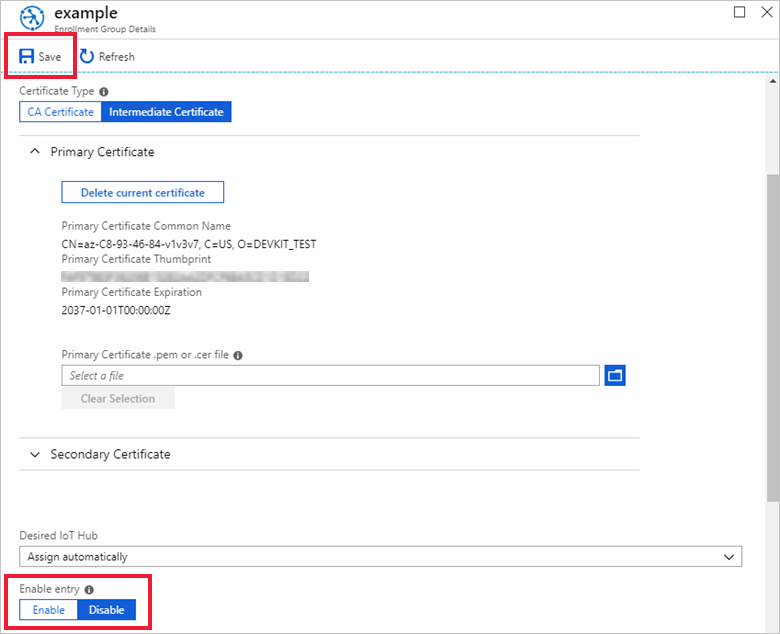
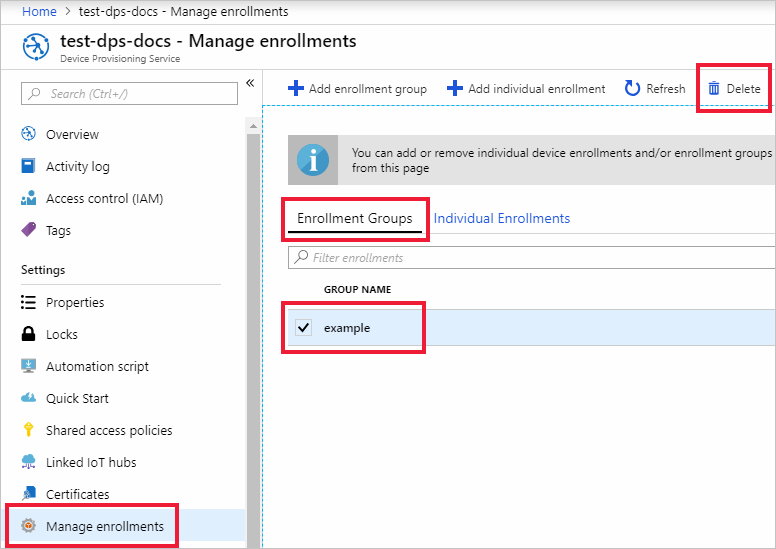
Select Delete at the top of the window, and then select Yes to confirm that you want to remove the enrollment group.
Disallow devices by using an individual enrollment entry
Disallow an X.509 intermediate or root CA certificate by using an enrollment group