DFSR-SYSVOL Authoritative / Non-Authoritative Restore Powershell Functions
Hi folks,
For this new post we are going to talk about DFSR replication SYSVOL restore.
You might be familiar with the following KB that explains the process of doing "D4/D2" like restore for SYSVOL when replicated over DFSR : https://support.microsoft.com/kb/2218556
Basically instead of having to configure registry keys like with FRS, you now need to change AD attributes to trigger either non-authoritative or authoritative restore of SYSVOL.
The attributes belong to the following object (one for each DC replication SYSVOL)
CN=SYSVOL Subscription,CN=Domain System Volume,CN=DFSR-LocalSettings,CN= <the server name> ,OU=Domain Controllers,DC= <domain>
They are msdfsr-Enabled and msdfsr-options
The above KB recommend ADSIEDIT.MSC to modify those values and its fine if you have a small number of DCs to manage.
But being a proper AD admin, even 3 DCs is a large number for me.. and especially if you happen to have to do that procedure on Windows 2008R2 Core..during a disaster recovery procedure… No don't look around ADSIEDIT is not there…
It's from that experience that I decided to create some new powershell functions to help me ( and now you too) with this kind of situation.
So what are those functions?
There are 3 of them:
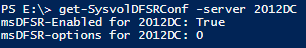
- Get-SysvolDFSRconf
Pretty straight forward, it will simply give you the values of the attributes "msdfsr-Enabled" and "msdfsr-options" on the server you will specify
- Set-nonauthDFSRsysvol:
This function will allow you to set the values for the attribute msdfsr-Enable like explained in the chapter "How to perform a non-authoritative synchronization of DFSR Replicated SYSVOL"
There is a switch called "step" that can take the values 1 or 2.
The first command you need to run is:
Set-nonauthDFSRSysvol –server <servername> -step 1
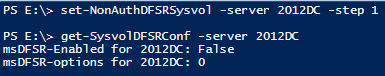
It will set the attribute of the specified server to FALSE (Step 1 of the KB procedure)
The second command you will have to run is:
Set-nonauthDFSRSysvol –server <servername> -step 2
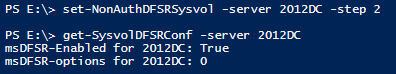
It will set the attribute of the specified server to TRUE (Step 5 of the KB procedure)
I have not integrated the DFSRDIAG POLLAD in the function as I wanted to keep things separated.
If you want to run it on a remote server you can use the following command:
Dfsrdiag pollad /member:DOMAIN\servername
You can easily combine that function with a foreach loop that will contain all the DC you want to set as non-authoritative in the case of a global SYSVOL restore (step 11 of the chapter How to perform a authoritative synchronization of DFSR Replicated SYSVOL")
- Set-authDFSRSysvol:
This function will allow you to set the values for the attribute msdfsr-Enable and msdfsr-Options like explained in the chapter "How to perform a authoritative synchronization of DFSR Replicated SYSVOL"
There is a switch called "step" that can take the values 1 or 2.
The first command you need to run is:
Set-authDFSRSysvol –server <servername> -step 1
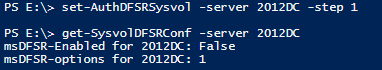
It will set the attribute msdfsr-Enabled of the specified server to FALSE and the attribute msdfsr-options to 1 (Step 1 of the KB procedure)
The second command you will have to run is:
Set-authDFSRSysvol –server <servername> -step 2
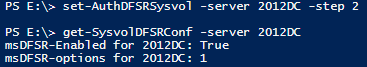
It will set the attribute msdfsr-Enabled of the specified server to TRUE (Step 6 of the KB procedure)
I have not integrated the DFSRDIAG POLLAD in the function as I wanted to keep things separated.
If you want to run it on a remote server you can use the following command:
Dfsrdiag pollad /member:DOMAIN\servername
You can download the PS script with the functions here.
You will need to "dot" it to register the functions in your environment.

Hope you find those useful in any of your SYSVOL restore operations and please give me feedback.
Comments
Anonymous
January 01, 2003
In which Powershell module does Get-SysvolDFSRconf and Set-authDFSRSysvol: belong?
Best regards, FlemmingAnonymous
January 01, 2003
Hi Flemming,
They are not part of any module. They are functions I created that you can add to your environment by running the script I have created. The link to the script is in the last paragraphe of the article.Anonymous
January 01, 2003
Thanks for the support Pierre ;) sorry I missed the comment. Another issue with these functions is that they assumed the DC are in the Domain Controllers OU. If they are not (which is not supported btw) they fail.
A soon as I have time I will update them to check the type of DC and the location of the DC.Anonymous
January 01, 2003
You cannot set the msDFSR-Enabled on an RODC since it is read only. Do it with its RW replication partner and wait (or force) the replication.Anonymous
January 01, 2003
Very useful post. Thank you.Anonymous
August 28, 2013
looks simply effective, thank youAnonymous
December 06, 2013
This is extremely useful Thomas,Anonymous
February 12, 2014
great post, thanks a lot! also thanks for sharing your script - i tried it in my testlab and it worked flawlessly.Anonymous
January 02, 2016
Very informative. Will be looking at this at some point.Anonymous
March 24, 2016
Didn't helped me.. still nothing on DC2 and DC3