نشر التحكم في تطبيق الوصول المشروط لأي تطبيق ويب باستخدام PingOne كموفر الهوية (IdP)
يمكنك تكوين عناصر تحكم الجلسة في Microsoft Defender for Cloud Apps للعمل مع أي تطبيق ويب وأي IdP غير Microsoft. توضح هذه المقالة كيفية توجيه جلسات عمل التطبيق من PingOne إلى Defender for Cloud Apps لعناصر التحكم في جلسة العمل في الوقت الحقيقي.
بالنسبة لهذه المقالة، سنستخدم تطبيق Salesforce كمثال لتطبيق ويب يتم تكوينه لاستخدام عناصر تحكم جلسة Defender for Cloud Apps. لتكوين تطبيقات أخرى، قم بتنفيذ نفس الخطوات وفقا لمتطلباتها.
المتطلبات الأساسية
يجب أن يكون لدى مؤسستك التراخيص التالية لاستخدام التحكم في تطبيق الوصول المشروط:
- ترخيص PingOne ذي صلة (مطلوب لتسجيل الدخول الأحادي)
- Microsoft Defender for Cloud Apps
تكوين تسجيل الدخول الأحادي ل PingOne موجود للتطبيق باستخدام بروتوكول مصادقة SAML 2.0
لتكوين عناصر تحكم الجلسة لتطبيقك باستخدام PingOne كمعرف
استخدم الخطوات التالية لتوجيه جلسات عمل تطبيق الويب من PingOne إلى Defender for Cloud Apps.
ملاحظة
يمكنك تكوين معلومات تسجيل الدخول الأحادي الخاصة بالتطبيق SAML التي يوفرها PingOne باستخدام إحدى الطرق التالية:
- الخيار 1: تحميل ملف بيانات تعريف SAML للتطبيق.
- الخيار 2: توفير بيانات SAML للتطبيق يدويا.
في الخطوات التالية، سنستخدم الخيار 2.
الخطوة 1: احصل على إعدادات تسجيل الدخول الأحادي لتطبيقك SAML
الخطوة 2: تكوين Defender for Cloud Apps بمعلومات SAML لتطبيقك
الخطوة 3: إنشاء تطبيق مخصص في PingOne
الخطوة 4: تكوين Defender for Cloud Apps بمعلومات تطبيق PingOne
الخطوة 5: إكمال التطبيق المخصص في PingOne
الخطوة 6: الحصول على تغييرات التطبيق في Defender for Cloud Apps
الخطوة 7: إكمال تغييرات التطبيق
الخطوة 8: إكمال التكوين في Defender for Cloud Apps
الخطوة 1: احصل على إعدادات تسجيل الدخول الأحادي لتطبيقك SAML
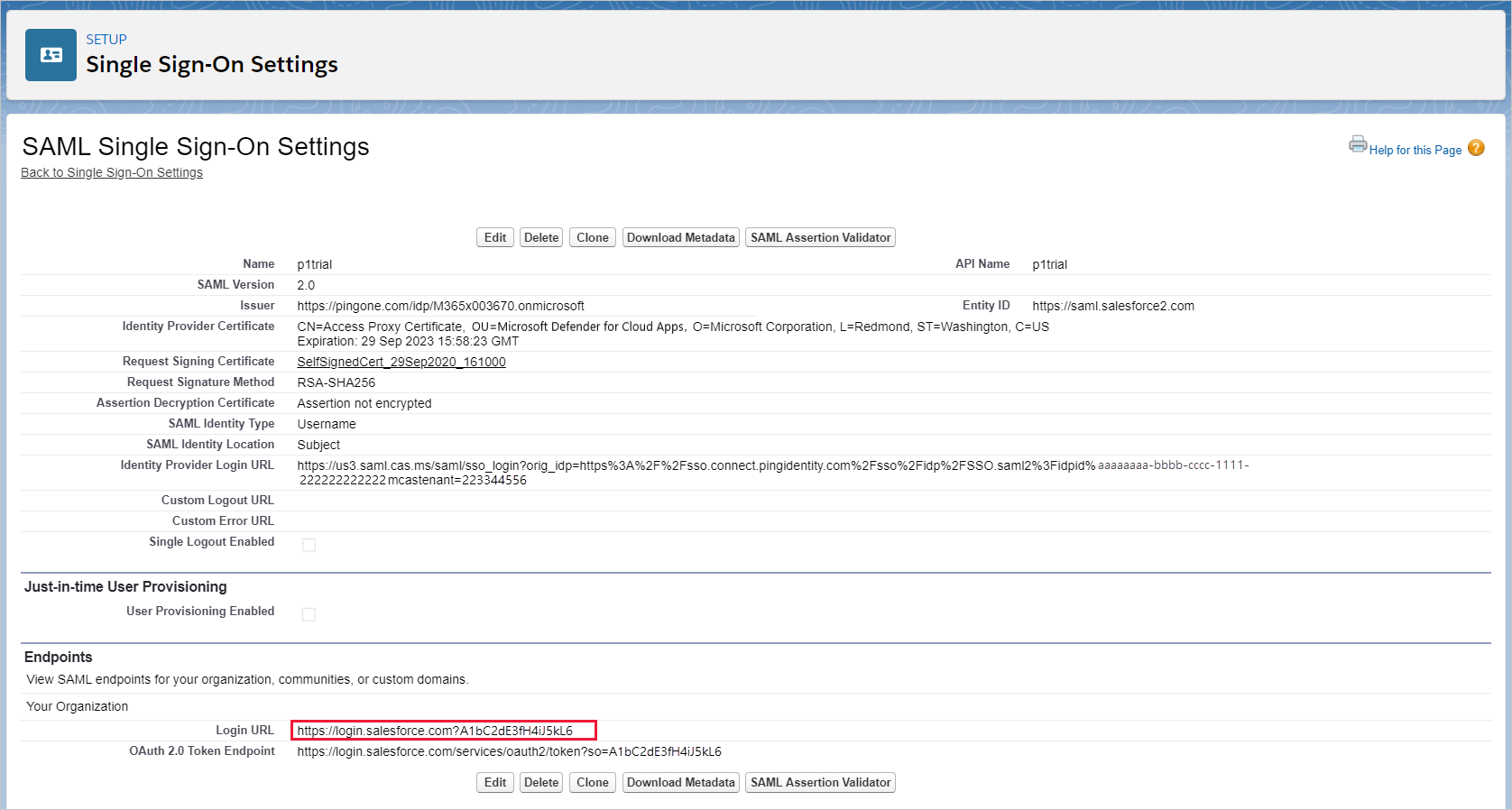
في Salesforce، استعرض للوصول إلىإعدادات الإعدادات>>هوية>واحدة Sign-On الإعدادات.
ضمن Single Sign-On Settings، حدد اسم تكوين SAML 2.0 الحالي.

في صفحة SAML Single Sign-On Setting ، دون ملاحظة عن عنوان URL لتسجيل الدخول إلى Salesforce. ستحتاج إلى هذا لاحقا.
ملاحظة
إذا كان تطبيقك يوفر شهادة SAML، فنزل ملف الشهادة.
الخطوة 2: تكوين Defender for Cloud Apps بمعلومات SAML لتطبيقك
في مدخل Microsoft Defender، حدد الإعدادات. ثم اختر تطبيقات السحابة.
ضمن التطبيقات المتصلة، حدد Conditional Access App Control apps.
حدد +إضافة، وفي النافذة المنبثقة، حدد التطبيق الذي تريد نشره، ثم حدد بدء المعالج.
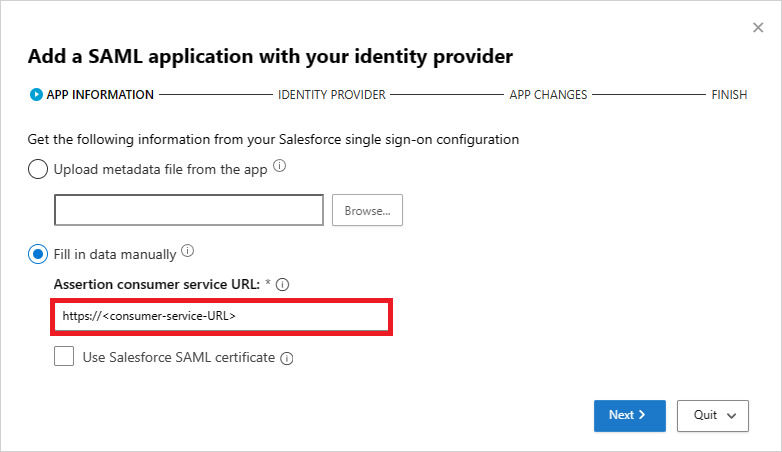
في صفحة معلومات التطبيق ، حدد تعبئة البيانات يدويا، في عنوان URL لخدمة مستهلك التأكيد أدخل عنوان URL لتسجيل الدخول إلى Salesforce الذي لاحظته سابقا، ثم حدد التالي.
ملاحظة
إذا كان تطبيقك يوفر شهادة SAML، فحدد Use <app_name> SAML certificate وقم بتحميل ملف الشهادة.
الخطوة 3: إنشاء تطبيق مخصص في PingOne
قبل المتابعة، استخدم الخطوات التالية للحصول على معلومات من تطبيق Salesforce الحالي.
في PingOne، قم بتحرير تطبيق Salesforce الحالي.
في صفحة تعيين سمة SSO ، قم بتدوين السمة والقيمة SAML_SUBJECT، ثم قم بتنزيل ملفات شهادة التوقيع وبيانات تعريف SAML .

افتح ملف بيانات تعريف SAML وقم بتدوين موقع PingOne SingleSignOnService. ستحتاج إلى هذا لاحقا.

في صفحة الوصول إلى المجموعة ، دون ملاحظة عن المجموعات المعينة.

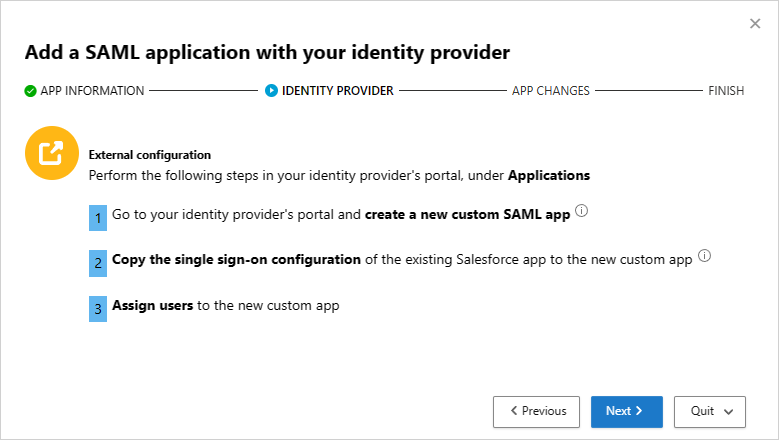
ثم استخدم الإرشادات من صفحة إضافة تطبيق SAML مع موفر الهوية لتكوين تطبيق مخصص في مدخل موفر الهوية الخاص بك.
ملاحظة
يمكنك تكوين تطبيق مخصص من اختبار التطبيق الحالي باستخدام عناصر التحكم في الوصول والجلسة دون تغيير السلوك الحالي لمؤسستك.
إنشاء تطبيق SAML جديد.

في صفحة تفاصيل التطبيق ، املأ النموذج، ثم حدد متابعة إلى الخطوة التالية.
تلميح
استخدم اسم تطبيق سيساعدك على التمييز بين التطبيق المخصص والتطبيق الحالي Salesforce.

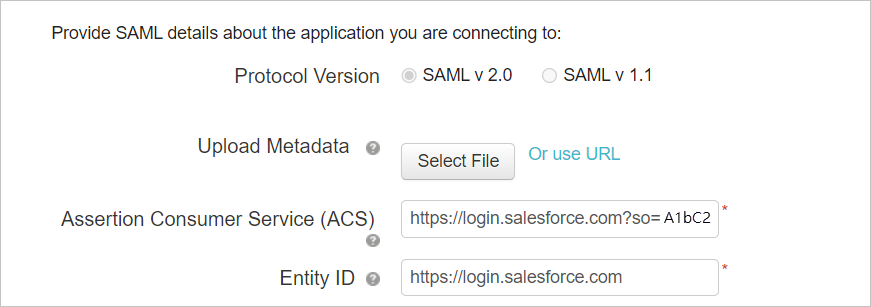
في صفحة تكوين التطبيق ، قم بما يلي، ثم حدد متابعة إلى الخطوة التالية.
- في الحقل Assertion Consumer Service (ACS)، أدخل عنوان URL لتسجيل الدخول إلى Salesforce الذي لاحظته سابقا.
- في حقل Entity ID ، أدخل معرفا فريدا بدءا من
https://. تأكد من أن هذا يختلف عن تكوين تطبيق Salesforce PingOne. - دون معرف الكيان. ستحتاج إلى هذا لاحقا.
في صفحة تعيين سمة تسجيل الدخول الأحادي، أضف السمة والقيمة SAML_SUBJECT لتطبيق Salesforce الموجودة التي لاحظتها سابقا، ثم حدد متابعة إلى الخطوة التالية.

في صفحة الوصول إلى المجموعة ، أضف مجموعات تطبيق Salesforce الموجودة التي لاحظتها سابقا، وأكمل التكوين.

الخطوة 4: تكوين Defender for Cloud Apps بمعلومات تطبيق PingOne
مرة أخرى في صفحة موفر الهوية Defender for Cloud Apps، حدد التالي للمتابعة.
في الصفحة التالية، حدد تعبئة البيانات يدويا، وقم بما يلي، ثم حدد التالي.
- بالنسبة إلى عنوان URL لخدمة مستهلك التأكيد، أدخل عنوان URL لتسجيل الدخول إلى Salesforce الذي لاحظته سابقا.
- حدد Upload identity provider's SAML certificate وقم بتحميل ملف الشهادة الذي قمت بتنزيله سابقا.

في الصفحة التالية، قم بتدوين المعلومات التالية، ثم حدد التالي. ستحتاج إلى المعلومات لاحقا.
- عنوان URL لتسجيل الدخول الأحادي Defender for Cloud Apps
- Defender for Cloud Apps السمات والقيم

الخطوة 5: إكمال التطبيق المخصص في PingOne
في PingOne، حدد موقع تطبيق Salesforce المخصص وقم بتحريره.

في الحقل Assertion Consumer Service (ACS)، استبدل عنوان URL بعنوان URL لتسجيل الدخول الأحادي Defender for Cloud Apps الذي لاحظته سابقا، ثم حدد Next.

أضف سمات Defender for Cloud Apps والقيم التي لاحظتها سابقا إلى خصائص التطبيق.

احفظ الإعدادات الخاصة بك.
الخطوة 6: الحصول على تغييرات التطبيق في Defender for Cloud Apps
مرة أخرى في صفحة Defender for Cloud Apps APP CHANGES، قم بما يلي، ولكن لا تحدد إنهاء. ستحتاج إلى المعلومات لاحقا.
- نسخ عنوان URL لتسجيل الدخول الأحادي إلى Defender for Cloud Apps SAML
- تنزيل شهادة DEFENDER FOR CLOUD APPS SAML

الخطوة 7: إكمال تغييرات التطبيق
في Salesforce، استعرضللإعدادات>إعدادات>الهوية>الأحادية Sign-On الإعدادات، وقم بما يلي:
مستحسن: إنشاء نسخة احتياطية من الإعدادات الحالية.
استبدل قيمة حقل عنوان URL لتسجيل الدخول لموفر الهوية بعنوان URL لتسجيل الدخول الأحادي Defender for Cloud Apps SAML الذي سجلته سابقا.
قم بتحميل شهادة Defender for Cloud Apps SAML التي قمت بتنزيلها مسبقا.
استبدل قيمة حقل Entity ID بمعرف كيان تطبيق PingOne المخصص الذي لاحظته سابقا.
حدد حفظ.
ملاحظة
شهادة Defender for Cloud Apps SAML صالحة لمدة عام واحد. بعد انتهاء صلاحيتها، ستحتاج إلى إنشاء شهادة جديدة.

الخطوة 8: إكمال التكوين في Defender for Cloud Apps
- مرة أخرى في صفحة Defender for Cloud Apps APP CHANGES، حدد Finish. بعد إكمال المعالج، سيتم توجيه جميع طلبات تسجيل الدخول المقترنة إلى هذا التطبيق من خلال التحكم في تطبيق الوصول المشروط.
المحتويات ذات الصلة
إذا واجهت أي مشاكل، فنحن هنا للمساعدة. للحصول على المساعدة أو الدعم لقضية المنتج، يرجى فتح تذكرة دعم.