Detailed SSH troubleshooting steps for issues connecting to a Linux VM in Azure
Applies to: ✔️ Linux VMs
There are many possible reasons that the SSH client might not be able to reach the SSH service on the VM. If you have followed through the more general SSH troubleshooting steps, you need to further troubleshoot the connection issue. This article guides you through detailed troubleshooting steps to determine where the SSH connection is failing and how to resolve it.
Take preliminary steps
The following diagram shows the components that are involved.
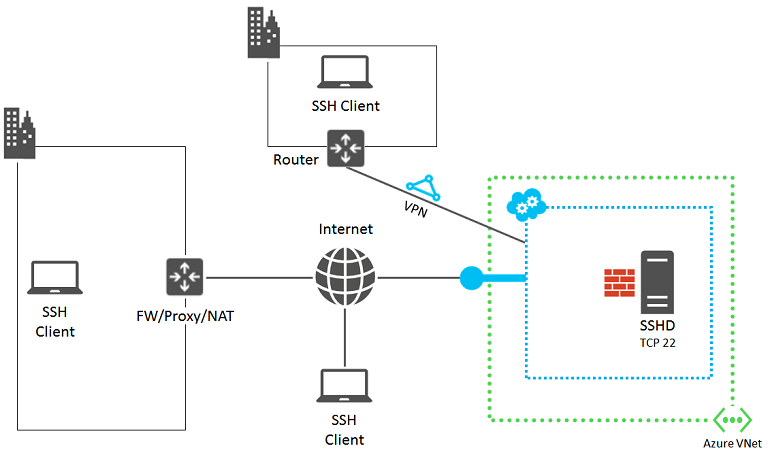
The following steps help you isolate the source of the failure and figure out solutions or workarounds.
Check the status of the VM in the portal. In the Azure portal, select Virtual machines > VM name.
The status pane for the VM should show Running. Scroll down to show recent activity for compute, storage, and network resources.
Select Settings to examine endpoints, IP addresses, network security groups, and other settings.
The VM should have an endpoint defined for SSH traffic that you can view in Endpoints or Network security group. Endpoints in VMs that were created by using Resource Manager are stored in a network security group. Verify that the rules have been applied to the network security group and are referenced in the subnet.
To verify network connectivity, check the configured endpoints and see if you can connect to the VM through another protocol, such as HTTP or another service.
After these steps, try the SSH connection again.
Find the source of the issue
The SSH client on your computer might fail to connect to the SSH service on the Azure VM due to issues or misconfigurations in the following areas:
Source 1: SSH client computer
To eliminate your computer as the source of the failure, verify that it can make SSH connections to another on-premises, Linux-based computer.
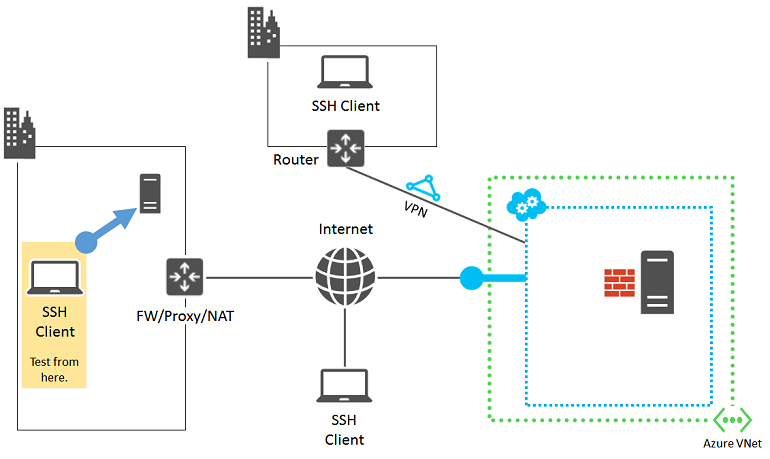
If the connection fails, check for the following issues on your computer:
- A local firewall setting that is blocking inbound or outbound SSH traffic (TCP 22)
- Locally installed client proxy software that is preventing SSH connections
- Locally installed network monitoring software that is preventing SSH connections
- Other types of security software that either monitor traffic or allow/disallow specific types of traffic
If one of these conditions apply, temporarily disable the software and try an SSH connection to an on-premises computer to find out the reason the connection is being blocked on your computer. Then work with your network administrator to correct the software settings to allow SSH connections.
If you are using certificate authentication, verify that you have these permissions to the .ssh folder in your home directory:
- Chmod 700 ~/.ssh
- Chmod 644 ~/.ssh/*.pub
- Chmod 600 ~/.ssh/id_rsa (or any other files that have your private keys stored in them)
- Chmod 644 ~/.ssh/known_hosts (contains hosts that you’ve connected to via SSH)
Source 2: Organization edge device
To eliminate your organization edge device as the source of the failure, verify that a computer directly connected to the Internet can make SSH connections to your Azure VM. If you are accessing the VM over a site-to-site VPN or an Azure ExpressRoute connection, skip to Source 3: Network security groups.
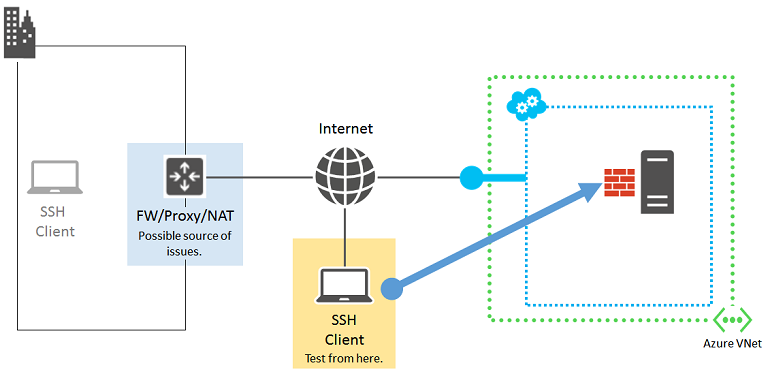
If you don't have a computer that is directly connected to the Internet, create a new Azure VM in its own resource group or cloud service and use that new VM. For more information, see Create a virtual machine running Linux in Azure. Delete the resource group or VM and cloud service when you're done with your testing.
If you can create an SSH connection with a computer that's directly connected to the Internet, check your organization edge device for:
- An internal firewall that's blocking SSH traffic with the Internet
- A proxy server that's preventing SSH connections
- Intrusion detection or network monitoring software running on devices in your edge network that's preventing SSH connections
Work with your network administrator to correct the settings of your organization edge devices to allow SSH traffic with the Internet.
Source 3: Network security groups
Network security groups enable you to have more granular control of allowed inbound and outbound traffic. You can create rules that span subnets and cloud services in an Azure virtual network. Check your network security group rules to ensure that SSH traffic to and from the Internet is allowed. For more information, see About network security groups.
You can also use IP Verify to validate the NSG configuration. For more information, see Azure network monitoring overview.
Source 4: Linux-based Azure virtual machine
The last source of possible problems is the Azure virtual machine itself.
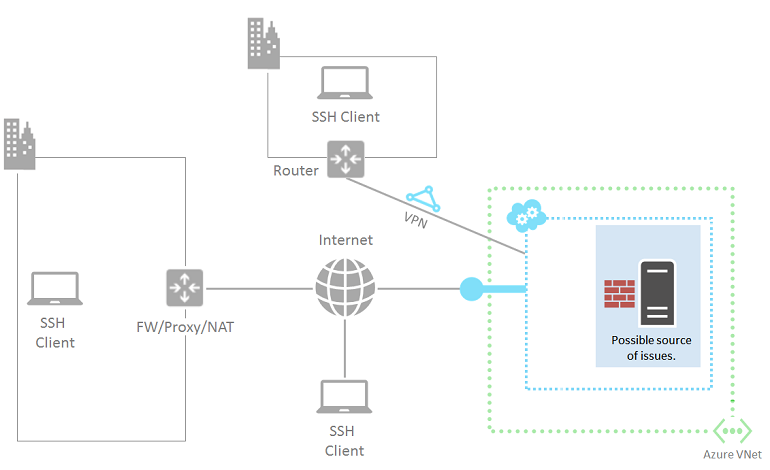
If you haven't done so already, follow the instructions to reset a password Linux-based virtual machines.
Try connecting from your computer again. If it still fails, the following are some of the possible issues:
- The SSH service is not running on the target virtual machine.
- The SSH service is not listening on TCP port 22. To test, install a telnet client on your local computer and run "telnet cloudServiceName.cloudapp.net 22". This step determines if the virtual machine allows inbound and outbound communication to the SSH endpoint.
- The local firewall on the target virtual machine has rules that are preventing inbound or outbound SSH traffic.
- Intrusion detection or network monitoring software that's running on the Azure virtual machine is preventing SSH connections.
Additional resources
For more information about troubleshooting application access, see Troubleshoot access to an application running on an Azure virtual machine.
Contact us for help
If you have questions or need help, create a support request, or ask Azure community support. You can also submit product feedback to Azure feedback community.