This article lists examples of how to delegate Azure role assignment management to other users with conditions.
Prerequisites
For information about the prerequisites to add or edit role assignment conditions, see Conditions prerequisites.
Example: Constrain roles
This condition allows a delegate to only add or remove role assignments for the Backup Contributor or Backup Reader roles.
You must add this condition to any role assignments for the delegate that include the following actions.
Microsoft.Authorization/roleAssignments/writeMicrosoft.Authorization/roleAssignments/delete
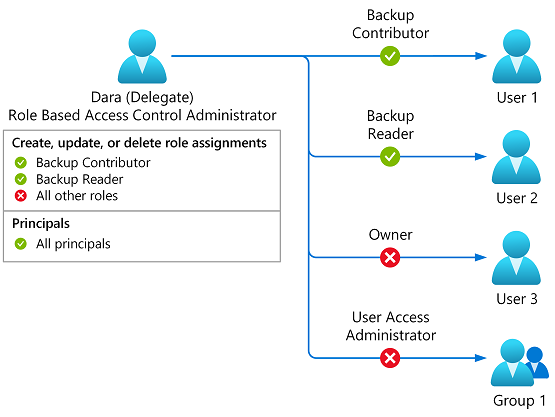
Here are the settings to add this condition using the Azure portal and a condition template.
Here are the settings to add this condition using the Azure portal and the condition editor.
To target both the add and remove role assignment actions, notice that you must add two conditions. You must add two conditions because the attribute source is different for each action. If you try to target both actions in the same condition, you won't be able to add an expression. For more information, see Symptom - No options available error.
(
(
!(ActionMatches{'Microsoft.Authorization/roleAssignments/write'})
)
OR
(
@Request[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAnyValues:GuidEquals {5e467623-bb1f-42f4-a55d-6e525e11384b, a795c7a0-d4a2-40c1-ae25-d81f01202912}
)
)
AND
(
(
!(ActionMatches{'Microsoft.Authorization/roleAssignments/delete'})
)
OR
(
@Resource[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAnyValues:GuidEquals {5e467623-bb1f-42f4-a55d-6e525e11384b, a795c7a0-d4a2-40c1-ae25-d81f01202912}
)
)
Here's how to add this condition using Azure PowerShell.
$roleDefinitionId = "f58310d9-a9f6-439a-9e8d-f62e7b41a168"
$principalId = "<principalId>"
$scope = "/subscriptions/<subscriptionId>"
$condition = "((!(ActionMatches{'Microsoft.Authorization/roleAssignments/write'})) OR (@Request[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAnyValues:GuidEquals {5e467623-bb1f-42f4-a55d-6e525e11384b, a795c7a0-d4a2-40c1-ae25-d81f01202912})) AND ((!(ActionMatches{'Microsoft.Authorization/roleAssignments/delete'})) OR (@Resource[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAnyValues:GuidEquals {5e467623-bb1f-42f4-a55d-6e525e11384b, a795c7a0-d4a2-40c1-ae25-d81f01202912}))"
$conditionVersion = "2.0"
New-AzRoleAssignment -ObjectId $principalId -Scope $scope -RoleDefinitionId $roleDefinitionId -Condition $condition -ConditionVersion $conditionVersion
Example: Constrain roles and principal types
This condition allows a delegate to only add or remove role assignments for the Backup Contributor or Backup Reader roles. Also, the delegate can only assign these roles to principals of type user or group.
You must add this condition to any role assignments for the delegate that include the following actions.
Microsoft.Authorization/roleAssignments/writeMicrosoft.Authorization/roleAssignments/delete

Here are the settings to add this condition using the Azure portal and a condition template.
Here are the settings to add this condition using the Azure portal and the condition editor.
To target both the add and remove role assignment actions, notice that you must add two conditions. You must add two conditions because the attribute source is different for each action. If you try to target both actions in the same condition, you won't be able to add an expression. For more information, see Symptom - No options available error.
(
(
!(ActionMatches{'Microsoft.Authorization/roleAssignments/write'})
)
OR
(
@Request[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAnyValues:GuidEquals {5e467623-bb1f-42f4-a55d-6e525e11384b, a795c7a0-d4a2-40c1-ae25-d81f01202912}
AND
@Request[Microsoft.Authorization/roleAssignments:PrincipalType] ForAnyOfAnyValues:StringEqualsIgnoreCase {'User', 'Group'}
)
)
AND
(
(
!(ActionMatches{'Microsoft.Authorization/roleAssignments/delete'})
)
OR
(
@Resource[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAnyValues:GuidEquals {5e467623-bb1f-42f4-a55d-6e525e11384b, a795c7a0-d4a2-40c1-ae25-d81f01202912}
AND
@Resource[Microsoft.Authorization/roleAssignments:PrincipalType] ForAnyOfAnyValues:StringEqualsIgnoreCase {'User', 'Group'}
)
)
Here's how to add this condition using Azure PowerShell.
$roleDefinitionId = "f58310d9-a9f6-439a-9e8d-f62e7b41a168"
$principalId = "<principalId>"
$scope = "/subscriptions/<subscriptionId>"
$condition = "((!(ActionMatches{'Microsoft.Authorization/roleAssignments/write'})) OR (@Request[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAnyValues:GuidEquals {5e467623-bb1f-42f4-a55d-6e525e11384b, a795c7a0-d4a2-40c1-ae25-d81f01202912} AND @Request[Microsoft.Authorization/roleAssignments:PrincipalType] ForAnyOfAnyValues:StringEqualsIgnoreCase {'User', 'Group'})) AND ((!(ActionMatches{'Microsoft.Authorization/roleAssignments/delete'})) OR (@Resource[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAnyValues:GuidEquals {5e467623-bb1f-42f4-a55d-6e525e11384b, a795c7a0-d4a2-40c1-ae25-d81f01202912} AND @Resource[Microsoft.Authorization/roleAssignments:PrincipalType] ForAnyOfAnyValues:StringEqualsIgnoreCase {'User', 'Group'}))"
$conditionVersion = "2.0"
New-AzRoleAssignment -ObjectId $principalId -Scope $scope -RoleDefinitionId $roleDefinitionId -Condition $condition -ConditionVersion $conditionVersion
Example: Constrain roles and specific groups
This condition allows a delegate to only add or remove role assignments for the Backup Contributor or Backup Reader roles. Also, the delegate can only assign these roles to specific groups named Marketing (28c35fea-2099-4cf5-8ad9-473547bc9423) or Sales (86951b8b-723a-407b-a74a-1bca3f0c95d0).
You must add this condition to any role assignments for the delegate that include the following actions.
Microsoft.Authorization/roleAssignments/writeMicrosoft.Authorization/roleAssignments/delete

Here are the settings to add this condition using the Azure portal and a condition template.
Here are the settings to add this condition using the Azure portal and the condition editor.
To target both the add and remove role assignment actions, notice that you must add two conditions. You must add two conditions because the attribute source is different for each action. If you try to target both actions in the same condition, you won't be able to add an expression. For more information, see Symptom - No options available error.
(
(
!(ActionMatches{'Microsoft.Authorization/roleAssignments/write'})
)
OR
(
@Request[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAnyValues:GuidEquals {5e467623-bb1f-42f4-a55d-6e525e11384b, a795c7a0-d4a2-40c1-ae25-d81f01202912}
AND
@Request[Microsoft.Authorization/roleAssignments:PrincipalId] ForAnyOfAnyValues:GuidEquals {28c35fea-2099-4cf5-8ad9-473547bc9423, 86951b8b-723a-407b-a74a-1bca3f0c95d0}
)
)
AND
(
(
!(ActionMatches{'Microsoft.Authorization/roleAssignments/delete'})
)
OR
(
@Resource[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAnyValues:GuidEquals {5e467623-bb1f-42f4-a55d-6e525e11384b, a795c7a0-d4a2-40c1-ae25-d81f01202912}
AND
@Resource[Microsoft.Authorization/roleAssignments:PrincipalId] ForAnyOfAnyValues:GuidEquals {28c35fea-2099-4cf5-8ad9-473547bc9423, 86951b8b-723a-407b-a74a-1bca3f0c95d0}
)
)
Here's how to add this condition using Azure PowerShell.
$roleDefinitionId = "f58310d9-a9f6-439a-9e8d-f62e7b41a168"
$principalId = "<principalId>"
$scope = "/subscriptions/<subscriptionId>"
$condition = "((!(ActionMatches{'Microsoft.Authorization/roleAssignments/write'})) OR (@Request[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAnyValues:GuidEquals {5e467623-bb1f-42f4-a55d-6e525e11384b, a795c7a0-d4a2-40c1-ae25-d81f01202912} AND @Request[Microsoft.Authorization/roleAssignments:PrincipalId] ForAnyOfAnyValues:GuidEquals {28c35fea-2099-4cf5-8ad9-473547bc9423, 86951b8b-723a-407b-a74a-1bca3f0c95d0})) AND ((!(ActionMatches{'Microsoft.Authorization/roleAssignments/delete'})) OR (@Resource[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAnyValues:GuidEquals {5e467623-bb1f-42f4-a55d-6e525e11384b, a795c7a0-d4a2-40c1-ae25-d81f01202912} AND @Resource[Microsoft.Authorization/roleAssignments:PrincipalId] ForAnyOfAnyValues:GuidEquals {28c35fea-2099-4cf5-8ad9-473547bc9423, 86951b8b-723a-407b-a74a-1bca3f0c95d0}))"
$conditionVersion = "2.0"
New-AzRoleAssignment -ObjectId $principalId -Scope $scope -RoleDefinitionId $roleDefinitionId -Condition $condition -ConditionVersion $conditionVersion
Example: Constrain virtual machine management
This condition allows a delegate to only add or remove role assignments for the Virtual Machine Administrator Login or Virtual Machine User Login roles. Also, the delegate can only assign these roles to a specific user named Dara (ea585310-c95c-4a68-af22-49af4363bbb1).
This condition is useful when you want to allow a delegate to assign a virtual machine login role to themselves for a virtual machine they've just created.
You must add this condition to any role assignments for the delegate that include the following actions.
Microsoft.Authorization/roleAssignments/writeMicrosoft.Authorization/roleAssignments/delete

Here are the settings to add this condition using the Azure portal and a condition template.
Here are the settings to add this condition using the Azure portal and the condition editor.
To target both the add and remove role assignment actions, notice that you must add two conditions. You must add two conditions because the attribute source is different for each action. If you try to target both actions in the same condition, you won't be able to add an expression. For more information, see Symptom - No options available error.
(
(
!(ActionMatches{'Microsoft.Authorization/roleAssignments/write'})
)
OR
(
@Request[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAnyValues:GuidEquals {1c0163c0-47e6-4577-8991-ea5c82e286e4, fb879df8-f326-4884-b1cf-06f3ad86be52}
AND
@Request[Microsoft.Authorization/roleAssignments:PrincipalId] ForAnyOfAnyValues:GuidEquals {ea585310-c95c-4a68-af22-49af4363bbb1}
)
)
AND
(
(
!(ActionMatches{'Microsoft.Authorization/roleAssignments/delete'})
)
OR
(
@Resource[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAnyValues:GuidEquals {1c0163c0-47e6-4577-8991-ea5c82e286e4, fb879df8-f326-4884-b1cf-06f3ad86be52}
AND
@Resource[Microsoft.Authorization/roleAssignments:PrincipalId] ForAnyOfAnyValues:GuidEquals {ea585310-c95c-4a68-af22-49af4363bbb1}
)
)
Here's how to add this condition using Azure PowerShell.
$roleDefinitionId = "f58310d9-a9f6-439a-9e8d-f62e7b41a168"
$principalId = "<principalId>"
$scope = "/subscriptions/<subscriptionId>"
$condition = "((!(ActionMatches{'Microsoft.Authorization/roleAssignments/write'})) OR (@Request[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAnyValues:GuidEquals {1c0163c0-47e6-4577-8991-ea5c82e286e4, fb879df8-f326-4884-b1cf-06f3ad86be52} AND @Request[Microsoft.Authorization/roleAssignments:PrincipalId] ForAnyOfAnyValues:GuidEquals {ea585310-c95c-4a68-af22-49af4363bbb1})) AND ((!(ActionMatches{'Microsoft.Authorization/roleAssignments/delete'})) OR (@Resource[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAnyValues:GuidEquals {1c0163c0-47e6-4577-8991-ea5c82e286e4, fb879df8-f326-4884-b1cf-06f3ad86be52} AND @Resource[Microsoft.Authorization/roleAssignments:PrincipalId] ForAnyOfAnyValues:GuidEquals {ea585310-c95c-4a68-af22-49af4363bbb1}))"
$conditionVersion = "2.0"
New-AzRoleAssignment -ObjectId $principalId -Scope $scope -RoleDefinitionId $roleDefinitionId -Condition $condition -ConditionVersion $conditionVersion
Example: Constrain AKS cluster management
This condition allows a delegate to only add or remove role assignments for the Azure Kubernetes Service RBAC Admin, Azure Kubernetes Service RBAC Cluster Admin, Azure Kubernetes Service RBAC Reader, or Azure Kubernetes Service RBAC Writer roles. Also, the delegate can only assign these roles to a specific user named Dara (ea585310-c95c-4a68-af22-49af4363bbb1).
This condition is useful when you want to allow a delegate to assign Azure Kubernetes Service (AKS) cluster data plane authorization roles to themselves for a cluster they've just created.
You must add this condition to any role assignments for the delegate that include the following actions.
Microsoft.Authorization/roleAssignments/writeMicrosoft.Authorization/roleAssignments/delete

Here are the settings to add this condition using the Azure portal and a condition template.
Here are the settings to add this condition using the Azure portal and the condition editor.
To target both the add and remove role assignment actions, notice that you must add two conditions. You must add two conditions because the attribute source is different for each action. If you try to target both actions in the same condition, you won't be able to add an expression. For more information, see Symptom - No options available error.
(
(
!(ActionMatches{'Microsoft.Authorization/roleAssignments/write'})
)
OR
(
@Request[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAnyValues:GuidEquals {3498e952-d568-435e-9b2c-8d77e338d7f7, b1ff04bb-8a4e-4dc4-8eb5-8693973ce19b, 7f6c6a51-bcf8-42ba-9220-52d62157d7db, a7ffa36f-339b-4b5c-8bdf-e2c188b2c0eb}
AND
@Request[Microsoft.Authorization/roleAssignments:PrincipalId] ForAnyOfAnyValues:GuidEquals {ea585310-c95c-4a68-af22-49af4363bbb1}
)
)
AND
(
(
!(ActionMatches{'Microsoft.Authorization/roleAssignments/delete'})
)
OR
(
@Resource[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAnyValues:GuidEquals {3498e952-d568-435e-9b2c-8d77e338d7f7, b1ff04bb-8a4e-4dc4-8eb5-8693973ce19b, 7f6c6a51-bcf8-42ba-9220-52d62157d7db, a7ffa36f-339b-4b5c-8bdf-e2c188b2c0eb}
AND
@Resource[Microsoft.Authorization/roleAssignments:PrincipalId] ForAnyOfAnyValues:GuidEquals {ea585310-c95c-4a68-af22-49af4363bbb1}
)
)
Here's how to add this condition using Azure PowerShell.
$roleDefinitionId = "f58310d9-a9f6-439a-9e8d-f62e7b41a168"
$principalId = "<principalId>"
$scope = "/subscriptions/<subscriptionId>"
$condition = "((!(ActionMatches{'Microsoft.Authorization/roleAssignments/write'})) OR (@Request[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAnyValues:GuidEquals {3498e952-d568-435e-9b2c-8d77e338d7f7, b1ff04bb-8a4e-4dc4-8eb5-8693973ce19b, 7f6c6a51-bcf8-42ba-9220-52d62157d7db, a7ffa36f-339b-4b5c-8bdf-e2c188b2c0eb} AND @Request[Microsoft.Authorization/roleAssignments:PrincipalId] ForAnyOfAnyValues:GuidEquals {ea585310-c95c-4a68-af22-49af4363bbb1})) AND ((!(ActionMatches{'Microsoft.Authorization/roleAssignments/delete'})) OR (@Resource[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAnyValues:GuidEquals {3498e952-d568-435e-9b2c-8d77e338d7f7, b1ff04bb-8a4e-4dc4-8eb5-8693973ce19b, 7f6c6a51-bcf8-42ba-9220-52d62157d7db, a7ffa36f-339b-4b5c-8bdf-e2c188b2c0eb} AND @Resource[Microsoft.Authorization/roleAssignments:PrincipalId] ForAnyOfAnyValues:GuidEquals {ea585310-c95c-4a68-af22-49af4363bbb1}))"
$conditionVersion = "2.0"
New-AzRoleAssignment -ObjectId $principalId -Scope $scope -RoleDefinitionId $roleDefinitionId -Condition $condition -ConditionVersion $conditionVersion
Example: Constrain ACR management
This condition allows a delegate to only add or remove role assignments for the AcrPull role. Also, the delegate can only assign these roles to principals of type service principal.
This condition is useful when you want to allow a developer to assign the AcrPull role to a managed identity themselves so that it can pull images from the Azure Container Registry (ACR).
You must add this condition to any role assignments for the delegate that include the following actions.
Microsoft.Authorization/roleAssignments/writeMicrosoft.Authorization/roleAssignments/delete

Here are the settings to add this condition using the Azure portal and a condition template.
| Condition |
Setting |
| Template |
Constrain roles and principal types |
| Roles |
AcrPull |
| Principal types |
Service principals |
Here are the settings to add this condition using the Azure portal and the condition editor.
To target both the add and remove role assignment actions, notice that you must add two conditions. You must add two conditions because the attribute source is different for each action. If you try to target both actions in the same condition, you won't be able to add an expression. For more information, see Symptom - No options available error.
(
(
!(ActionMatches{'Microsoft.Authorization/roleAssignments/write'})
)
OR
(
@Request[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAnyValues:GuidEquals {7f951dda-4ed3-4680-a7ca-43fe172d538d}
AND
@Request[Microsoft.Authorization/roleAssignments:PrincipalType] ForAnyOfAnyValues:StringEqualsIgnoreCase {'ServicePrincipal'}
)
)
AND
(
(
!(ActionMatches{'Microsoft.Authorization/roleAssignments/delete'})
)
OR
(
@Resource[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAnyValues:GuidEquals {7f951dda-4ed3-4680-a7ca-43fe172d538d}
AND
@Resource[Microsoft.Authorization/roleAssignments:PrincipalType] ForAnyOfAnyValues:StringEqualsIgnoreCase {'ServicePrincipal'}
)
)
Here's how to add this condition using Azure PowerShell.
$roleDefinitionId = "f58310d9-a9f6-439a-9e8d-f62e7b41a168"
$principalId = "<principalId>"
$scope = "/subscriptions/<subscriptionId>"
$condition = "((!(ActionMatches{'Microsoft.Authorization/roleAssignments/write'})) OR (@Request[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAnyValues:GuidEquals {7f951dda-4ed3-4680-a7ca-43fe172d538d} AND @Request[Microsoft.Authorization/roleAssignments:PrincipalType] ForAnyOfAnyValues:StringEqualsIgnoreCase {'ServicePrincipal'})) AND ((!(ActionMatches{'Microsoft.Authorization/roleAssignments/delete'})) OR (@Resource[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAnyValues:GuidEquals {7f951dda-4ed3-4680-a7ca-43fe172d538d} AND @Resource[Microsoft.Authorization/roleAssignments:PrincipalType] ForAnyOfAnyValues:StringEqualsIgnoreCase {'ServicePrincipal'}))"
$conditionVersion = "2.0"
New-AzRoleAssignment -ObjectId $principalId -Scope $scope -RoleDefinitionId $roleDefinitionId -Condition $condition -ConditionVersion $conditionVersion
Example: Constrain add role assignments
This condition allows a delegate to only add role assignments for the Backup Contributor or Backup Reader roles. The delegate can remove any role assignments.
You must add this condition to any role assignments for the delegate that include the following action.
Microsoft.Authorization/roleAssignments/write

Here are the settings to add this condition using the Azure portal and the condition editor.
(
(
!(ActionMatches{'Microsoft.Authorization/roleAssignments/write'})
)
OR
(
@Request[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAnyValues:GuidEquals {5e467623-bb1f-42f4-a55d-6e525e11384b, a795c7a0-d4a2-40c1-ae25-d81f01202912}
)
)
Here's how to add this condition using Azure PowerShell.
$roleDefinitionId = "f58310d9-a9f6-439a-9e8d-f62e7b41a168"
$principalId = "<principalId>"
$scope = "/subscriptions/<subscriptionId>"
$condition = "((!(ActionMatches{'Microsoft.Authorization/roleAssignments/write'})) OR (@Request[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAnyValues:GuidEquals {5e467623-bb1f-42f4-a55d-6e525e11384b, a795c7a0-d4a2-40c1-ae25-d81f01202912}))"
$conditionVersion = "2.0"
New-AzRoleAssignment -ObjectId $principalId -Scope $scope -RoleDefinitionId $roleDefinitionId -Condition $condition -ConditionVersion $conditionVersion
Example: Allow most roles, but don't allow others to assign roles
This condition allows a delegate to add or remove role assignments for all roles except the Owner, Role Based Access Control Administrator, and User Access Administrator roles.
This condition is useful when you want to allow a delegate to assign most roles, but not allow the delegate to allow others to assign roles.
Note
This condition should be used with caution. If a new built-in or custom role is later added that includes the permission to create role assignments, this condition would not prevent the delegate from assigning roles. The condition would have to be updated to include the new built-in or custom role.
You must add this condition to any role assignments for the delegate that include the following actions.
Microsoft.Authorization/roleAssignments/writeMicrosoft.Authorization/roleAssignments/delete

Here are the settings to add this condition using the Azure portal and a condition template.
Here are the settings to add this condition using the Azure portal and the condition editor.
To target both the add and remove role assignment actions, notice that you must add two conditions. You must add two conditions because the attribute source is different for each action. If you try to target both actions in the same condition, you won't be able to add an expression. For more information, see Symptom - No options available error.
(
(
!(ActionMatches{'Microsoft.Authorization/roleAssignments/write'})
)
OR
(
@Request[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAllValues:GuidNotEquals {8e3af657-a8ff-443c-a75c-2fe8c4bcb635, f58310d9-a9f6-439a-9e8d-f62e7b41a168, 18d7d88d-d35e-4fb5-a5c3-7773c20a72d9}
)
)
AND
(
(
!(ActionMatches{'Microsoft.Authorization/roleAssignments/delete'})
)
OR
(
@Resource[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAllValues:GuidNotEquals {8e3af657-a8ff-443c-a75c-2fe8c4bcb635, f58310d9-a9f6-439a-9e8d-f62e7b41a168, 18d7d88d-d35e-4fb5-a5c3-7773c20a72d9}
)
)
Here's how to add this condition using Azure PowerShell.
$roleDefinitionId = "f58310d9-a9f6-439a-9e8d-f62e7b41a168"
$principalId = "<principalId>"
$scope = "/subscriptions/<subscriptionId>"
$condition = "((!(ActionMatches{'Microsoft.Authorization/roleAssignments/write'})) OR (@Request[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAllValues:GuidNotEquals {8e3af657-a8ff-443c-a75c-2fe8c4bcb635, f58310d9-a9f6-439a-9e8d-f62e7b41a168, 18d7d88d-d35e-4fb5-a5c3-7773c20a72d9})) AND ((!(ActionMatches{'Microsoft.Authorization/roleAssignments/delete'})) OR (@Resource[Microsoft.Authorization/roleAssignments:RoleDefinitionId] ForAnyOfAllValues:GuidNotEquals {8e3af657-a8ff-443c-a75c-2fe8c4bcb635, f58310d9-a9f6-439a-9e8d-f62e7b41a168, 18d7d88d-d35e-4fb5-a5c3-7773c20a72d9}))"
$conditionVersion = "2.0"
New-AzRoleAssignment -ObjectId $principalId -Scope $scope -RoleDefinitionId $roleDefinitionId -Condition $condition -ConditionVersion $conditionVersion
Next steps







