Note
Access to this page requires authorization. You can try signing in or changing directories.
Access to this page requires authorization. You can try changing directories.
Object replication asynchronously copies block blobs from a container in one storage account to a container in another storage account. When you configure an object replication policy, you specify the source account and container and the destination account and container. After the policy is configured, Azure Storage automatically copies the results of create, update, and delete operations on a source object to the destination object. For more information about object replication in Azure Storage, see Object replication for block blobs.
An authorized user can configure an object replication policy where the source account is in one Microsoft Entra tenant and the destination account is in a different tenant if cross tenant replication is allowed across Microsoft Entra tenants. If your security policies require that you restrict object replication to storage accounts that reside within the same tenant only, you can disallow the creation of policies where the source and destination accounts are in different tenants. By default, cross-tenant object replication is disabled for all new storage accounts created after Dec 15, 2023, unless you explicitly allow it.
This article describes how to remediate cross-tenant object replication for your storage accounts. It also describes how to create policies to enforce a prohibition on cross-tenant object replication for new and existing storage accounts.
For more information on how to configure object replication policies, including cross-tenant policies, see Configure object replication for block blobs.
Remediate cross-tenant object replication
To prevent object replication across Microsoft Entra tenants, set the AllowCrossTenantReplication property for the storage account to false. If a storage account doesn't currently participate in any cross-tenant object replication policies, then setting the AllowCrossTenantReplication property to false prevents future configuration of cross-tenant object replication policies with this storage account as the source or destination. However, if a storage account currently participates in one or more cross-tenant object replication policies, then setting the AllowCrossTenantReplication property to false isn't permitted until you delete the existing cross-tenant policies.
Cross-tenant policies aren't permitted by default for a storage account created after Dec 15, 2023. However, the AllowCrossTenantReplication property wasn't set by default for an existing storage account created before Dec 15, 2023, and doesn't return a value until you had explicitly set it. The storage account can participate in object replication policies across tenants when the property value is either null or true for accounts created prior to Dev 15, 2023. For accounts created after that time, the property needs to be set to true. Setting the AllowCrossTenantReplication property doesn't incur any downtime on the storage account.
Remediate cross-tenant replication for a new account
To disallow cross-tenant replication for a new storage account, use the Azure portal, PowerShell, or Azure CLI. The property defaults to false for new accounts created after Dec 15, 2023, even when not set explicitly.
To disallow cross-tenant object replication for a storage account, follow these steps:
In the Azure portal, navigate to the Storage accounts page, and select Create.
Fill out the Basics tab for the new storage account.
On the Advanced tab, in the Blob storage section, locate the Allow cross-tenant replication setting, and uncheck the box.
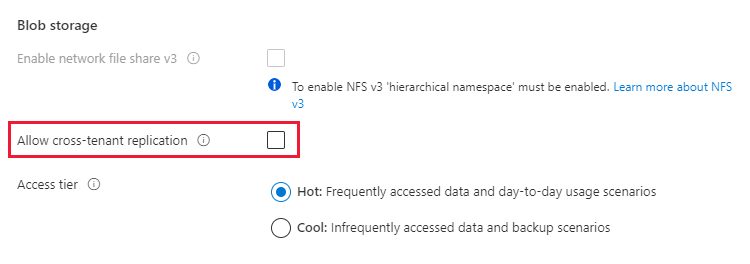
Complete the process of creating the account.
Remediate cross-tenant replication for an existing account
To disallow cross-tenant replication for an existing storage account, use the Azure portal, PowerShell, or Azure CLI.
To disallow cross-tenant object replication for an existing storage account that isn't currently participating in any cross-tenant policies, follow these steps:
Navigate to your storage account in the Azure portal.
Under Data management, select Object replication.
Select Advanced settings.
Uncheck Allow cross-tenant replication. By default, this box is checked, because cross-tenant object replication is permitted for a storage account unless you explicitly disallow it.
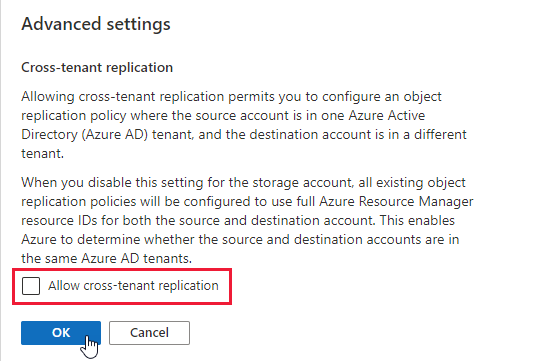
Select OK to save your changes.
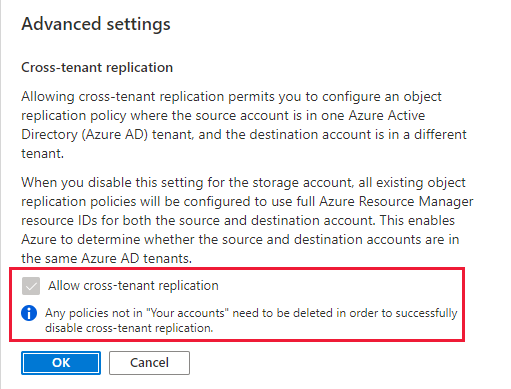
If the storage account is currently participating in one or more cross-tenant replication policies, you will not be able to disallow cross-tenant object replication until you delete those policies. In this scenario, the setting is unavailable in the Azure portal, as shown in the following image.
After you disallow cross-tenant replication, attempting to configure a cross-tenant policy with the storage account as the source or destination fails. Azure Storage returns an error indicating that cross-tenant object replication isn't permitted for the storage account.
When cross-tenant object replication is disallowed for a storage account, then any new object replication policies that you create with that account must include the full Azure Resource Manager IDs for the source and destination account. Azure Storage requires the full resource ID to verify whether the source and destination accounts reside within the same tenant. For more information, see Specify full resource IDs for source and destination accounts.
The AllowCrossTenantReplication property is supported for storage accounts that use the Azure Resource Manager deployment model only. For information about which storage accounts use the Azure Resource Manager deployment model, see Types of storage accounts.
Permissions for allowing or disallowing cross-tenant replication
To set the AllowCrossTenantReplication property for a storage account, a user must have permissions to create and manage storage accounts. Azure role-based access control (Azure RBAC) roles that provide these permissions include the Microsoft.Storage/storageAccounts/write or Microsoft.Storage/storageAccounts/* action. Built-in roles with this action include:
- The Azure Resource Manager Owner role
- The Azure Resource Manager Contributor role
- The Storage Account Contributor role
These roles do not provide access to data in a storage account via Microsoft Entra ID. However, they include the Microsoft.Storage/storageAccounts/listkeys/action, which grants access to the account access keys. With this permission, a user can use the account access keys to access all data in a storage account.
Role assignments must be scoped to the level of the storage account or higher to permit a user to allow or disallow cross-tenant object replication for the storage account. For more information about role scope, see Understand scope for Azure RBAC.
Be careful to restrict assignment of these roles only to those who require the ability to create a storage account or update its properties. Use the principle of least privilege to ensure that users have the fewest permissions that they need to accomplish their tasks. For more information about managing access with Azure RBAC, see Best practices for Azure RBAC.
Note
The classic subscription administrator roles Service Administrator and Co-Administrator include the equivalent of the Azure Resource Manager Owner role. The Owner role includes all actions, so a user with one of these administrative roles can also create and manage storage accounts. For more information, see Azure roles, Microsoft Entra roles, and classic subscription administrator roles.
Use Azure Policy to audit for compliance
If you have a large number of storage accounts, you may want to perform an audit to make sure that those accounts are configured to prevent cross-tenant object replication. To audit a set of storage accounts for their compliance, use Azure Policy. Azure Policy is a service that you can use to create, assign, and manage policies that apply rules to Azure resources. Azure Policy helps you to keep those resources compliant with your corporate standards and service level agreements. For more information, see Overview of Azure Policy.
Create a policy with an Audit effect
Azure Policy supports effects that determine what happens when a policy rule is evaluated against a resource. The Audit effect creates a warning when a resource isn't in compliance, but doesn't stop the request. For more information about effects, see Understand Azure Policy effects.
To create a policy with an Audit effect for the cross-tenant object replication setting for a storage account with the Azure portal, follow these steps:
In the Azure portal, navigate to the Azure Policy service.
Under the Authoring section, select Definitions.
Select Add policy definition to create a new policy definition.
For the Definition location field, select the More button to specify where the audit policy resource is located.
Specify a name for the policy. You can optionally specify a description and category.
Under Policy rule, add the following policy definition to the policyRule section.
{ "if": { "allOf": [ { "field": "type", "equals": "Microsoft.Storage/storageAccounts" }, { "not": { "field":"Microsoft.Storage/storageAccounts/allowCrossTenantReplication", "equals": "false" } } ] }, "then": { "effect": "audit" } }Save the policy.
Assign the policy
Next, assign the policy to a resource. The scope of the policy corresponds to that resource and any resources beneath it. For more information on policy assignment, see Azure Policy assignment structure.
To assign the policy with the Azure portal, follow these steps:
- In the Azure portal, navigate to the Azure Policy service.
- Under the Authoring section, select Assignments.
- Select Assign policy to create a new policy assignment.
- For the Scope field, select the scope of the policy assignment.
- For the Policy definition field, select the More button, then select the policy you defined in the previous section from the list.
- Provide a name for the policy assignment. The description is optional.
- Leave Policy enforcement set to Enabled. This setting has no effect on the audit policy.
- Select Review + create to create the assignment.
View compliance report
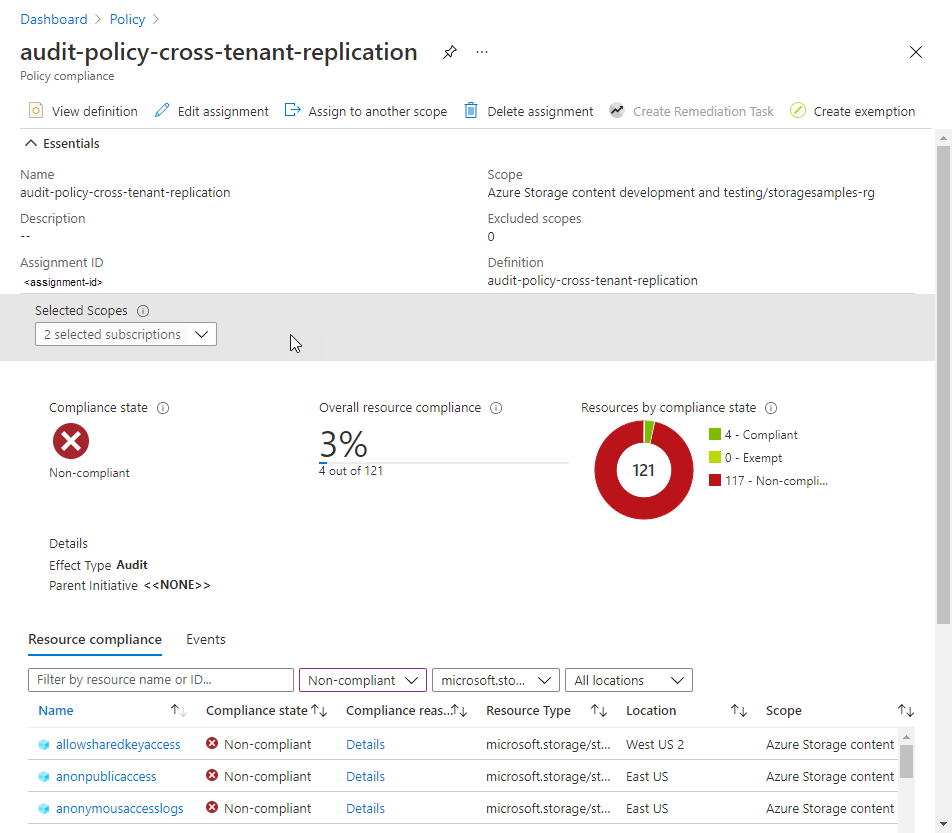
After you've assigned the policy, you can view the compliance report. The compliance report for an audit policy provides information on which storage accounts are still permitting cross-tenant object replication policies. For more information, see Get policy compliance data.
It may take several minutes for the compliance report to become available after the policy assignment is created.
To view the compliance report in the Azure portal, follow these steps:
In the Azure portal, navigate to the Azure Policy service.
Select Compliance.
Filter the results for the name of the policy assignment that you created in the previous step. The report shows resources that aren't in compliance with the policy.
You can drill down into the report for additional details, including a list of storage accounts that aren't in compliance.
Use Azure Policy to enforce same-tenant replication policies
Azure Policy supports cloud governance by ensuring that Azure resources adhere to requirements and standards. To ensure that storage accounts in your organization disallow cross-tenant replication, you can create a policy that prevents the creation of a new storage account that allows cross-tenant object replication policies. The enforcement policy uses the Deny effect to prevent a request that would create or modify a storage account to allow cross-tenant object replication. The Deny policy will also prevent all configuration changes to an existing account if the cross-tenant object replication setting for that account isn't compliant with the policy. For more information about the Deny effect, see Understand Azure Policy effects.
To create a policy with a Deny effect for cross-tenant object replication, follow the same steps described in Use Azure Policy to audit for compliance, but provide the following JSON in the policyRule section of the policy definition:
{
"if": {
"allOf": [
{
"field": "type",
"equals": "Microsoft.Storage/storageAccounts"
},
{
"not": {
"field":"Microsoft.Storage/storageAccounts/allowCrossTenantReplication",
"equals": "false"
}
}
]
},
"then": {
"effect": "deny"
}
}
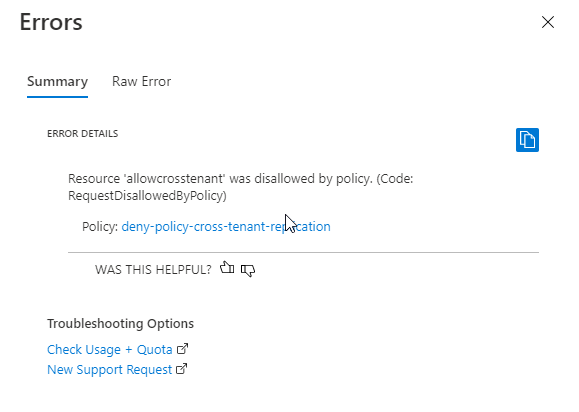
After you create the policy with the Deny effect and assign it to a scope, a user cannot create a storage account that allows cross-tenant object replication. Nor can a user make any configuration changes to an existing storage account that currently allows cross-tenant object replication. Attempting to do so results in an error. The AllowCrossTenantReplication property for the storage account must be set to false to proceed with account creation or configuration updates, in compliance with the policy.
The following image shows the error that occurs if you try to create a storage account that allows cross-tenant object replication (the default for a new account) when a policy with a Deny effect requires that cross-tenant object replication is disallowed.