How Defender for Cloud Apps helps protect your OneLogin
As an identity and access management solution, OneLogin holds the keys to your organizations most business critical services. OneLogin manages the authentication and authorization processes for your users. Any abuse of OneLogin by a malicious actor or any human error may expose your most critical assets and services to potential attacks.
Connecting OneLogin to Defender for Cloud Apps gives you improved insights into your OneLogin admin activities and managed users sign-ins and provides threat detection for anomalous behavior.
Main threats
- Compromised accounts and insider threats
- Data leakage
- Insufficient security awareness
- Unmanaged bring your own device (BYOD)
How Defender for Cloud Apps helps to protect your environment
Detect cloud threats, compromised accounts, and malicious insiders
Use the audit trail of activities for forensic investigations
Control OneLogin with policies
| Type | Name |
|---|---|
| Built-in anomaly detection policy | Activity from anonymous IP addresses Activity from infrequent country Activity from suspicious IP addresses Impossible travel Activity performed by terminated user (requires Microsoft Entra ID as IdP) Multiple failed login attempts Unusual administrative activities Unusual impersonated activities |
| Activity policy | Built a customized policy by the OneLogin activities |
For more information about creating policies, see Create a policy.
Automate governance controls
In addition to monitoring for potential threats, you can apply and automate the following OneLogin governance actions to remediate detected threats:
| Type | Action |
|---|---|
| User governance | Notify user on alert (via Microsoft Entra ID) Require user to sign in again (via Microsoft Entra ID) Suspend user (via Microsoft Entra ID) |
For more information about remediating threats from apps, see Governing connected apps.
Protect OneLogin in real time
Review our best practices for securing and collaborating with external users and blocking and protecting the download of sensitive data to unmanaged or risky devices.
Connect OneLogin to Microsoft Defender for Cloud Apps
This section provides instructions for connecting Microsoft Defender for Cloud Apps to your existing OneLogin app using the App Connector APIs. This connection gives you visibility into and control over your organization's OneLogin use.
Prerequisites
- The OneLogin account used for logging into OneLogin must be a Super User. For more information about OneLogin administrative privileges, see this article.
Configure OneLogin
Go to the OneLogin admin portal. Select API Credentials in the Developers dropdown menu.
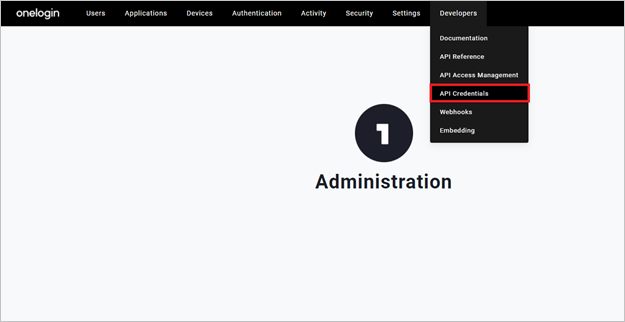
Select New Credential.
Name your new application as Microsoft Defender for Cloud Apps, choose Read all permissions, and select Save.
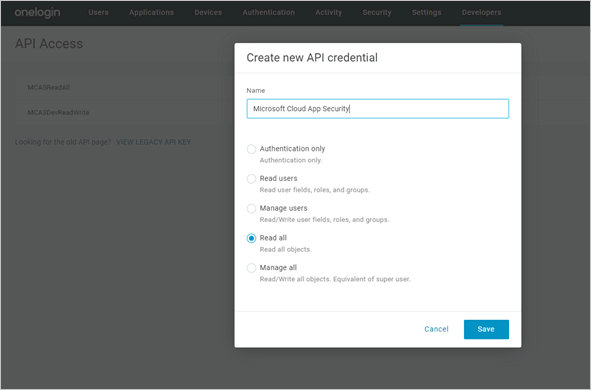
Copy the Client ID and the Client Secret. You'll need them in the following steps.
Configure Defender for Cloud Apps
In the Microsoft Defender Portal, select Settings. Then choose Cloud Apps. Under Connected apps, select App Connectors.
In the App connectors page, select +Connect an app, followed by OneLogin.
In the next window, give the connector a descriptive name, and select Next.
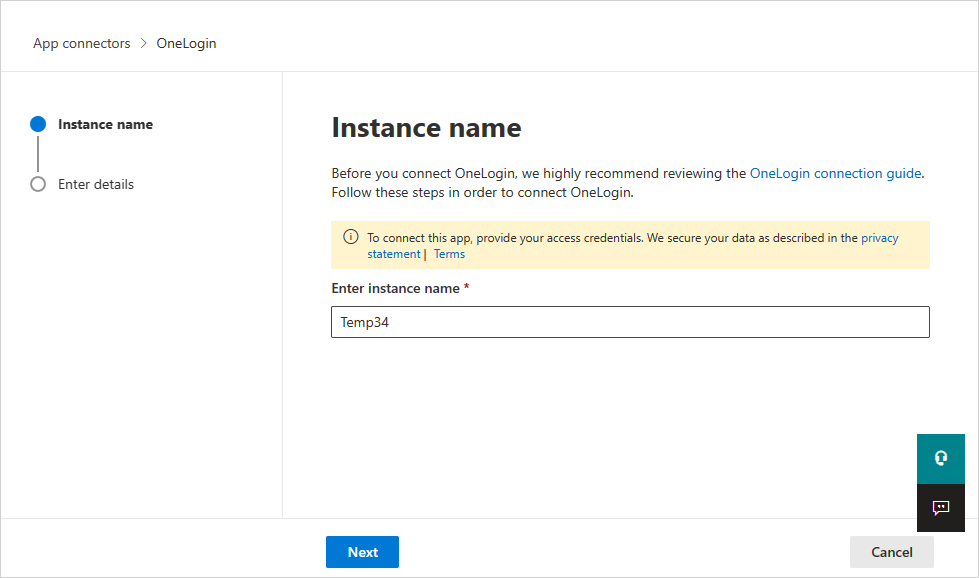
In the Enter details window, enter the Client ID and the Client Secret that you copied and select Submit.
In the Microsoft Defender Portal, select Settings. Then choose Cloud Apps. Under Connected apps, select App Connectors. Make sure the status of the connected App Connector is Connected.
The first connection can take up to 4 hours to get all users and their activities after the connector was established.
After the connector's Status is marked as Connected, the connector is live and working.
Next steps
If you run into any problems, we're here to help. To get assistance or support for your product issue, please open a support ticket.
Обратна връзка
Очаквайте скоро: През цялата 2024 г. постепенно ще отстраняваме проблемите в GitHub като механизъм за обратна връзка за съдържание и ще го заменим с нова система за обратна връзка. За повече информация вижте: https://aka.ms/ContentUserFeedback.
Подаване и преглед на обратна връзка за