EDR detection test for verifying device's onboarding and reporting services
Applies to:
Scenario requirements and setup
- Windows 11, Windows 10 version 1709 build 16273 or newer, Windows 8.1, or Windows 7 SP1.
- Windows Server 2022, Windows Server 2019, Windows Server 2016, Windows Server 2012 R2, and Windows Server 2008 R2 SP1.
- Linux
- macOS
- Microsoft Defender for Endpoint
- Microsoft Defender for Endpoint on Linux
Endpoint detection and response for Endpoint provide advanced attack detections that are near real-time and actionable. Security analysts can prioritize alerts effectively, gain visibility into the full scope of a breach, and take response actions to remediate threats.
Run an EDR detection test to verify that the device is properly onboarded and reporting to the service. Perform the following steps on the newly onboarded device:
Windows
Open a Command Prompt window
At the prompt, copy and run the following command. The Command Prompt window closes automatically.
powershell.exe -NoExit -ExecutionPolicy Bypass -WindowStyle Hidden $ErrorActionPreference= 'silentlycontinue';(New-Object System.Net.WebClient).DownloadFile('http://127.0.0.1/1.exe', 'C:\\test-WDATP-test\\invoice.exe');Start-Process 'C:\\test-WDATP-test\\invoice.exe'If successful, the detection test is marked as completed and a new alert appears within a few minutes.
Linux
- Download script file to an onboarded Linux server
curl -o ~/Downloads/MDE-Linux-EDR-DIY.zip -L https://aka.ms/MDE-Linux-EDR-DIY
- Extract the zip
unzip ~/Downloads/MDE-Linux-EDR-DIY.zip
- And run the following command to give the script executable permission:
chmod +x ./mde_linux_edr_diy.sh
- Run the following command to execute the script:
./mde_linux_edr_diy.sh
- After a few minutes, a detection should be raised in Microsoft Defender XDR. Look at the alert details, machine timeline, and perform your typical investigation steps.
macOS
In your browser, Microsoft Edge for Mac or Safari, download MDATP MacOS DIY.zip from https://aka.ms/mdatpmacosdiy and extract.
The following prompt appears:
Do you want to allow downloads on "mdatpclientanalyzer.blob.core.windows.net"?
You can change which websites can download files in Websites Preferences.Click Allow.
Open Downloads.
You must be able to see MDATP MacOS DIY.
Tip
If you double-click MDATP MacOS DIY, you will get the following message:
"MDATP MacOS DIY" cannot be opened because the developer cannot be verifier.
macOS cannot verify that this app is free from malware.
[Move to Trash] [Cancel]Click Cancel.
Right-click MDATP MacOS DIY, and then click Open.
The system displays the following message:
macOS cannot verify the developer of MDATP MacOS DIY. Are you sure you want to open it?
By opening this app, you will be overriding system security which can expose your computer and personal information to malware that may harm your Mac or compromise your privacy.Click Open.
The system will display the following message:
Microsoft Defender for Endpoint - macOS EDR DIY test file
Corresponding alert will be available in the MDATP portal.Click Open.
In few minutes, an alert macOS EDR Test Alert is raised.
Go to Microsoft Defender portal (https://security.microsoft.com/).
Go to the Alert Queue.
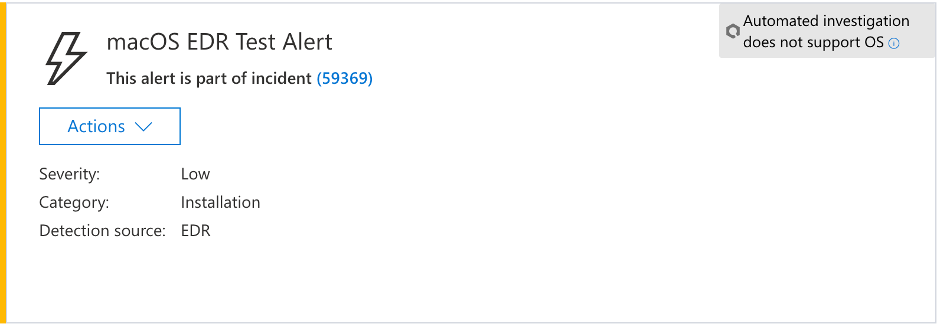
The macOS EDR test alert shows severity, category, detection source, and a collapsed menu of actions.
Look at the alert details and the device timeline, and perform the regular investigation steps.
Next steps
If you're experiencing issues with application compatibility or performance, you might consider adding exclusions. See the following articles for more information:
- Configure and validate exclusions for Microsoft Defender for Endpoint on macOS
- Address false positives/negatives in Microsoft Defender for Endpoint
- Manage suppression rules
- Create indicators of compromise (IoC)
- Create and manage custom detections rules
Also, see the Microsoft Defender for Endpoint Security Operations Guide.