Configure deployment credentials for Azure App Service
To secure app deployment from a local computer, Azure App Service supports two types of credentials for local Git deployment and FTP/S deployment. These credentials are not the same as your Azure subscription credentials.
User-level credentials: one set of credentials for the entire Azure account. It can be used to deploy to App Service for any app, in any subscription, that the Azure account has permission to access. It's the default set that's surfaced in the portal GUI (such as the Overview and Properties of the app's resource page). When a user is granted app access via Role-Based Access Control (RBAC) or coadmin permissions, that user can use their own user-level credentials until the access is revoked. Do not share these credentials with other Azure users.
App-level credentials: one set of credentials for each app. It can be used to deploy to that app only. The credentials for each app are generated automatically at app creation. They can't be configured manually, but can be reset anytime. For a user to be granted access to app-level credentials via (RBAC), that user must be contributor or higher on the app (including Website Contributor built-in role). Readers are not allowed to publish, and can't access those credentials.
Note
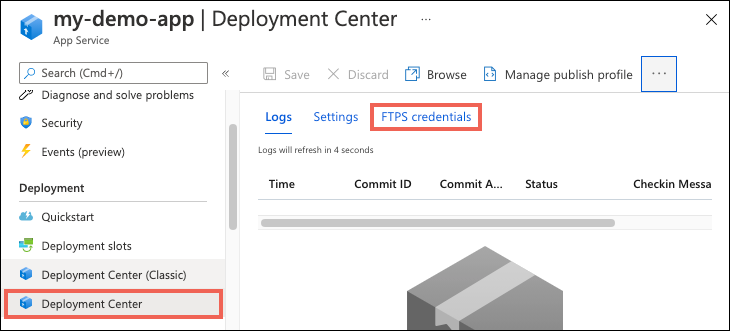
When basic authentication is disabled, you can't view or configure deployment credentials in the Deployment Center.
Configure user-scope credentials
Run the az webapp deployment user set command. Replace <username> and <password> with a deployment user username and password.
- The username must be unique within Azure, and for local Git pushes, must not contain the ‘@’ symbol.
- The password must be at least eight characters long, with two of the following three elements: letters, numbers, and symbols.
az webapp deployment user set --user-name <username> --password <password>
The JSON output shows the password as null.
Use user-scope credentials with FTP/FTPS
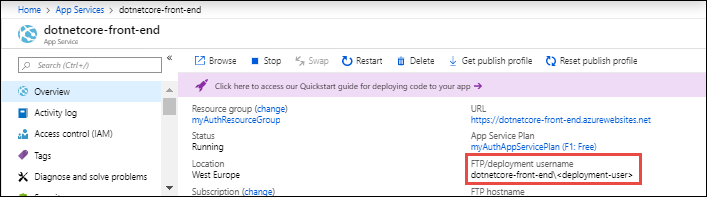
Authenticating to an FTP/FTPS endpoint using user-scope credentials requires a username in the following format:
<app-name>\<user-name>
Since user-scope credentials are linked to the user and not a specific resource, the username must be in this format to direct the sign-in action to the right app endpoint.
Get application-scope credentials
Get the application-scope credentials using the az webapp deployment list-publishing-profiles command. For example:
az webapp deployment list-publishing-profiles --resource-group <group-name> --name <app-name>
For local Git deployment, you can also use the az webapp deployment list-publishing-credentials command to get a Git remote URI for your app, with the application-scope credentials already embedded. For example:
az webapp deployment list-publishing-credentials --resource-group <group-name> --name <app-name> --query scmUri
Note that the returned Git remote URI doesn't contain /<app-name>.git at the end. When you add the remote URI, make sure to append /<app-name>.git to avoid an error 22 with git-http-push. Additionally, when using git remote add ... via shells that use the dollar sign for variable interpolation (such as bash), escape any dollar signs (\$) in the username or password. Failure to escape this character can result in authentication errors.
Reset application-scope credentials
Reset the application-scope credentials using the az resource invoke-action command:
az resource invoke-action --action newpassword --resource-group <group-name> --name <app-name> --resource-type Microsoft.Web/sites
Disable basic authentication
See Disable basic authentication in App Service deployments.
Next steps
Find out how to use these credentials to deploy your app from local Git or using FTP/S.