Exposure score in Defender Vulnerability Management
Applies to:
- Microsoft Defender Vulnerability Management
- Microsoft Defender for Endpoint Plan 2
- Microsoft Defender XDR
- Microsoft Defender for Servers Plan 1 & 2
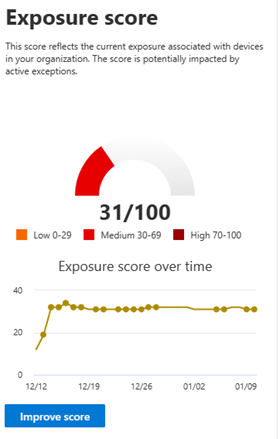
Your exposure score is visible in the Defender Vulnerability Management dashboard in the Microsoft Defender portal. It reflects how vulnerable your organization is to cybersecurity threats. Low exposure score means your devices are less vulnerable to exploitation.
- Quickly understand and identify high-level takeaways about the state of security in your organization.
- Detect and respond to areas that require investigation or action to improve the current state.
- Communicate with peers and management about the impact of security efforts.
The card gives you a high-level view of your exposure score trend over time. Any spikes in the chart give you a visual indication of a high cybersecurity threat exposure that you can investigate further.
Exposure score is broken down into the following levels:
- 0-29: low exposure score
- 30-69: medium exposure score
- 70-100: high exposure score
Tip
Did you know you can try all the features in Microsoft Defender Vulnerability Management for free? Find out how to sign up for a free trial.
How to use exposure score to reduce your vulnerability exposure
When software weaknesses are identified, they're transformed into recommendations and prioritized based on risk to the organization. By remediating vulnerabilities with security recommendations prioritized to reduce your exposure score, you can reduce your overall vulnerability exposure.
To view security recommendations prioritized to reduce your exposure score:
- Go to the Vulnerability management navigation menu and select Dashboard
- Select Improve score on the Exposure score card
The security recommendations page will open with a list of security recommendations prioritized by the potential impact on your exposure score. The higher the impact on lowering your exposure by implementing a recommendation, the less vulnerable you'll be to exploitation. For more information, see security recommendations impact.
Using the top security recommendations, which can be viewed in the Defender Vulnerability Management dashboard can also help you achieve this goal.