Събитие
9.04, 15 ч. - 10.04, 12 ч.
Програмирайте бъдещето с AI и се свържете с Java колеги и експерти на JDConf 2025.
Регистрирайте се сегаТози браузър вече не се поддържа.
Надстройте до Microsoft Edge, за да се възползвате от най-новите функции, актуализации на защитата и техническа поддръжка.
An external authentication method (EAM) lets users choose an external provider to meet multifactor authentication (MFA) requirements when they sign in to Microsoft Entra ID. An EAM can satisfy MFA requirements from Conditional Access policies, Microsoft Entra ID Protection risk-based Conditional Access policies, Privileged Identity Management (PIM) activation, and when the application itself requires MFA.
EAMs differ from federation in that the user identity is originated and managed in Microsoft Entra ID. With federation, the identity is managed in the external identity provider. EAMs require at least a Microsoft Entra ID P1 license.
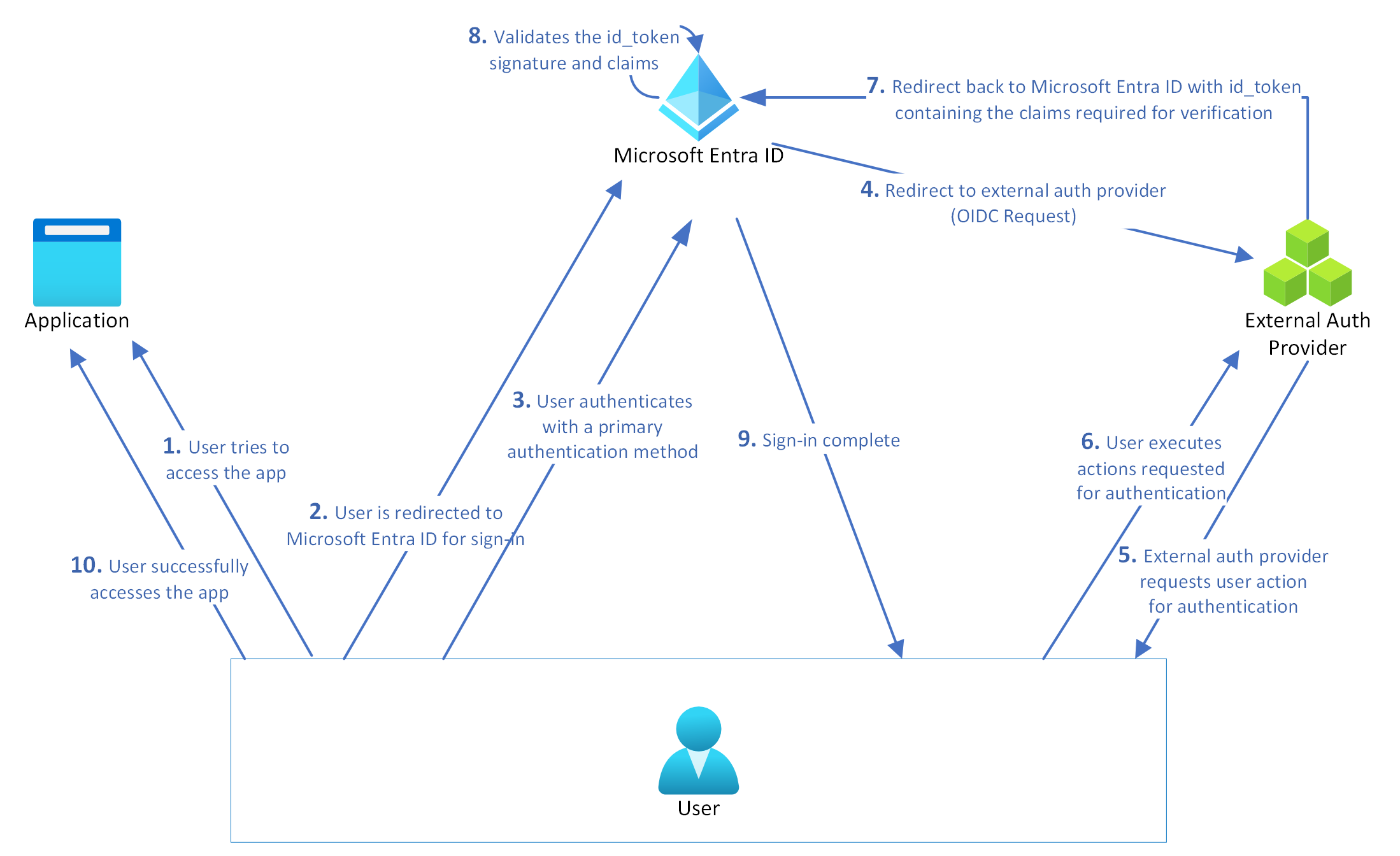
To create an EAM, you need the following information from your external authentication provider:
An Application ID is generally a multitenant application from your provider, which is used as part of the integration. You need to provide admin consent for this application in your tenant.
A Client ID is an identifier from your provider used as part of the authentication integration to identify Microsoft Entra ID requesting authentication.
A Discovery URL is the OpenID Connect (OIDC) discovery endpoint for the external authentication provider.
Бележка
See Configure a new external authentication provider with Microsoft Entra ID to set up the App registration.
Важно
Ensure that the kid (Key ID) property is base64-encoded in both the JWT header of the id_token and in the JSON Web Key Set (JWKS) retrieved from the provider’s jwks_uri. This encoding alignment is essential for the seamless validation of token signatures during authentication processes. Misalignment can result in issues with key matching or signature validation.
EAMs are managed with the Microsoft Entra ID Authentication methods policy, just like built-in methods.
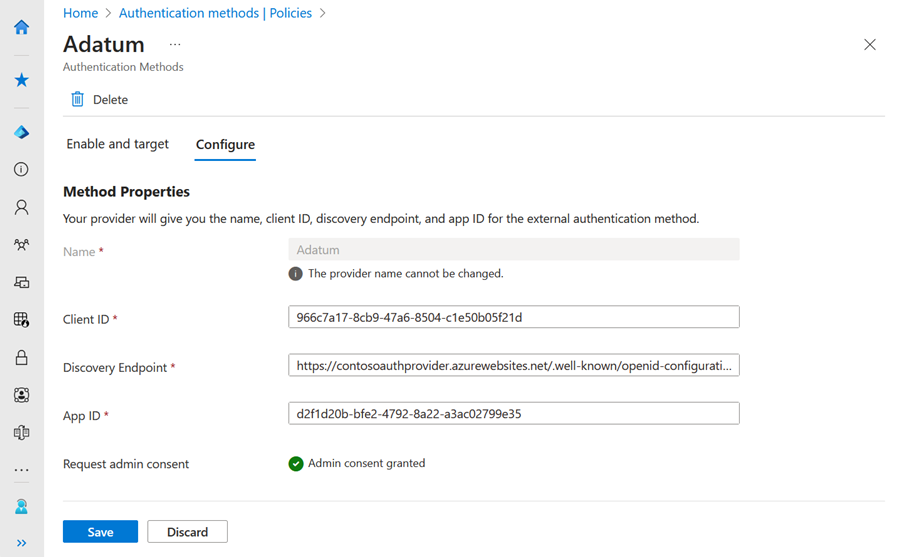
Before you create an EAM in the admin center, make sure you have the metadata to configure an EAM.
Sign in to the Microsoft Entra admin center as at least a Privileged Role Administrator.
Browse to Protection > Authentication methods > Add external method (Preview).
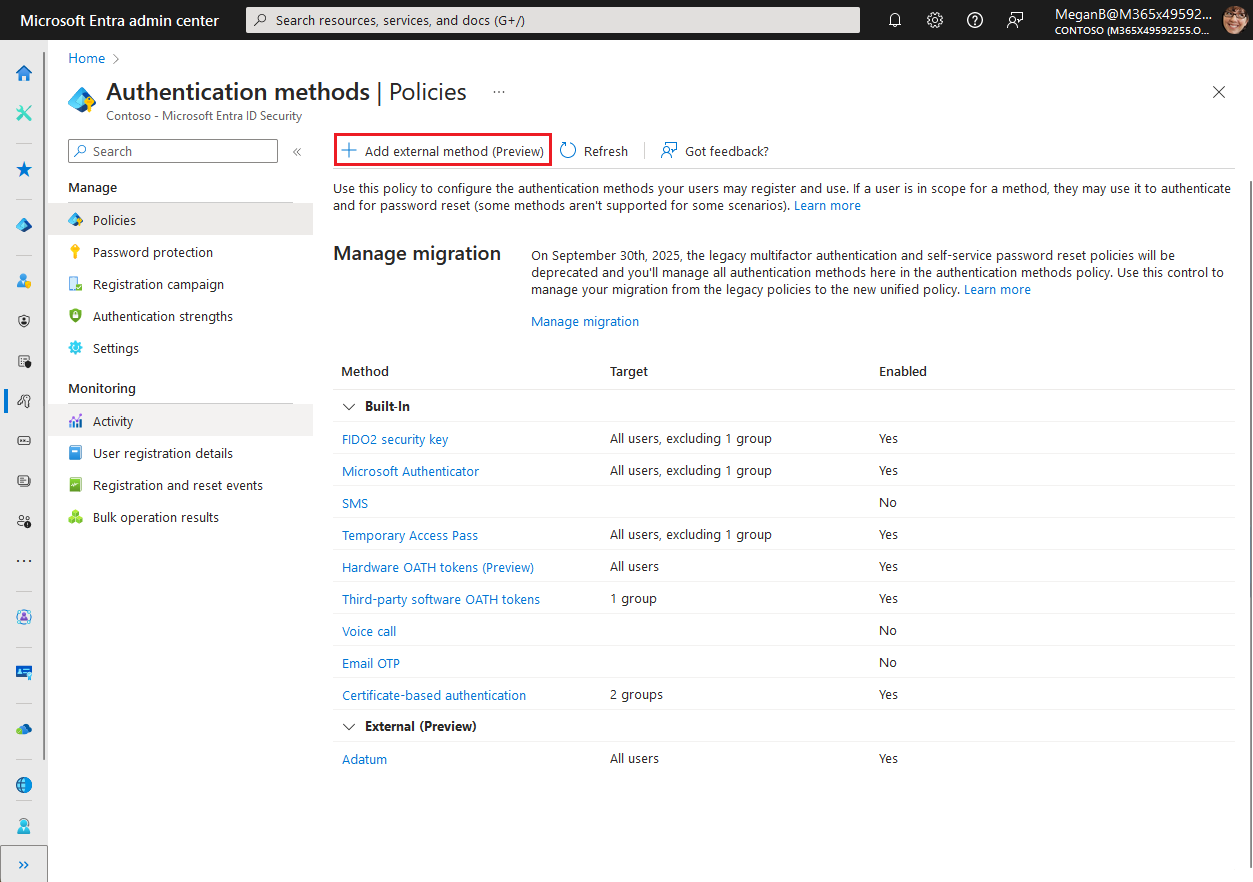
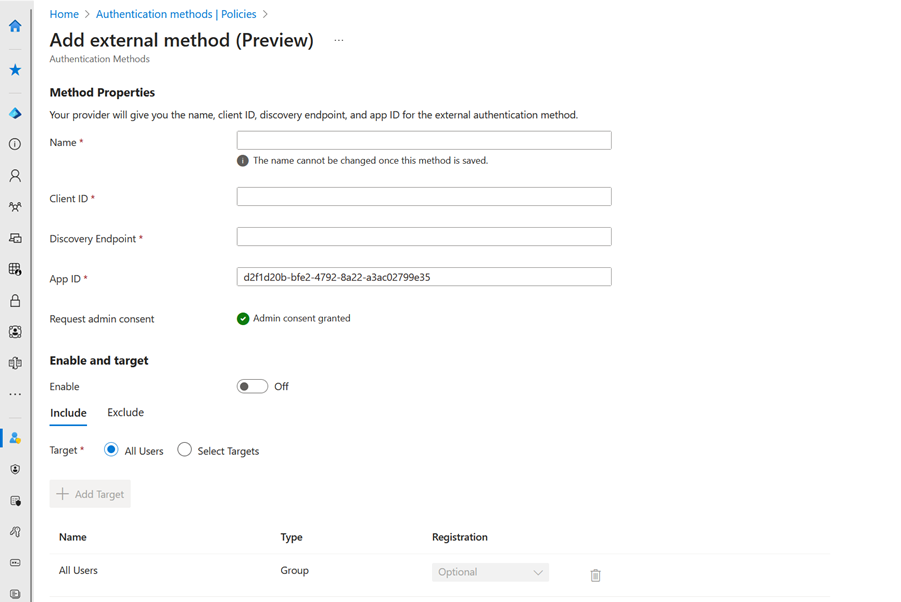
Add method properties based on configuration information from your provider. For example:
https://adatum.com/.well-known/openid-configurationВажно
The display name is the name that's shown to the user in the method picker. It can't be changed after the method is created. Display names must be unique.
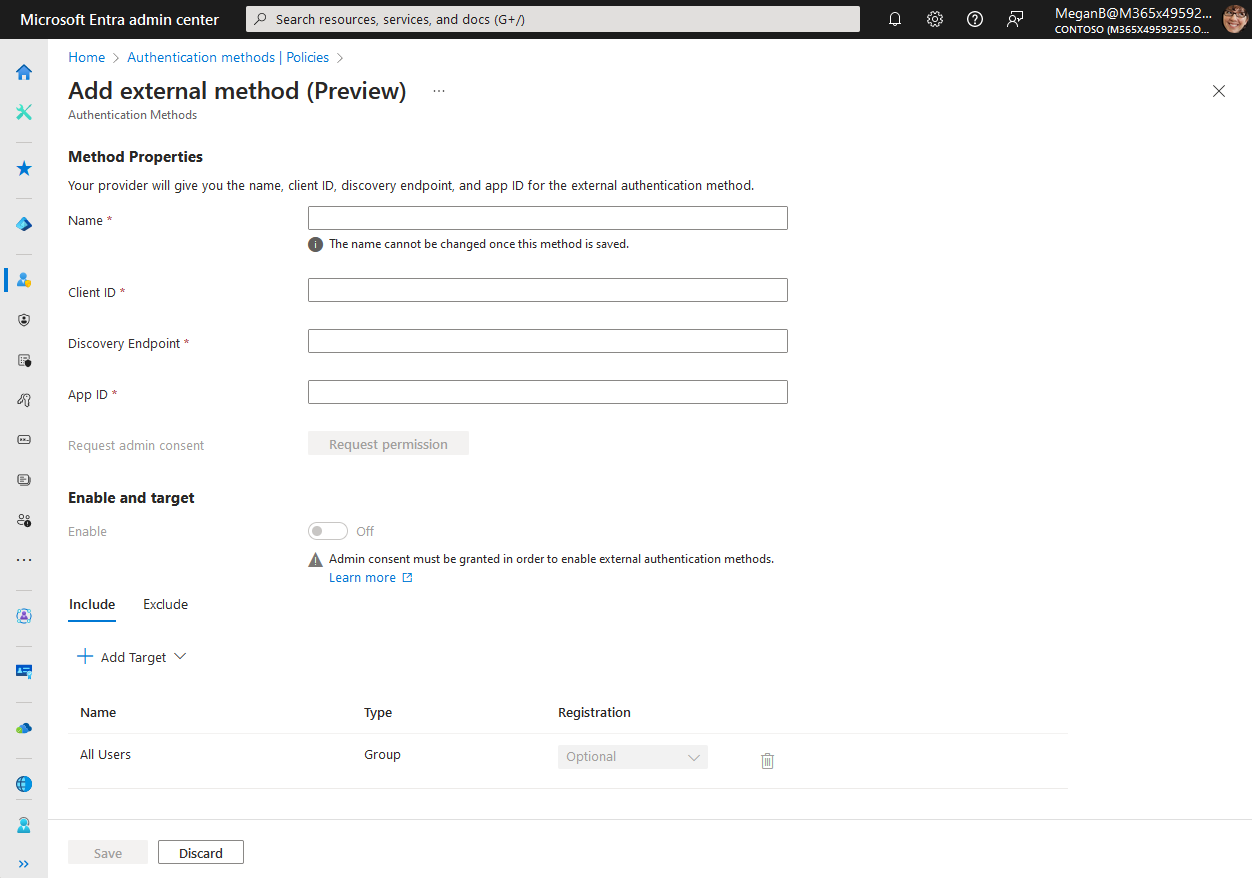
You need at least the Privileged Role Administrator role to grant admin consent for the provider’s application. If you don't have the role required to grant consent, you can still save your authentication method, but you can't enable it until consent is granted.
After you enter the values from your provider, press the button to request for admin consent to be granted to the application so that it can read the required info from the user to authenticate correctly. You're prompted to sign in with an account with admin permissions and grant the provider’s application with the required permissions.
After you sign in, click Accept to grant admin consent:
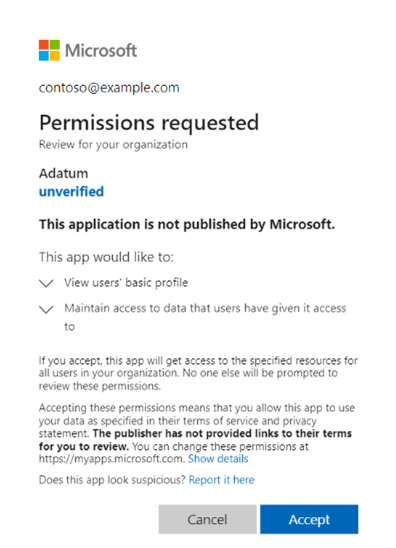
You can see the permissions that the provider application requests before you grant consent. After you grant admin consent and the change replicates, the page refreshes to show that admin consent was granted.
If the application has permissions, then you can also enable the method before saving. Otherwise, you need to save the method in a disabled state, and enable after the application is granted consent.
Once the method is enabled, all users in scope can choose the method for any MFA prompts. If the application from the provider doesn't have consent approved, then any sign-in with the method fails.
If the application is deleted or no longer has permission, users see an error and sign-in fails. The method can't be used.
To manage your EAMs in the Microsoft Entra admin center, open the Authentication methods policy. Select the method name to open the configuration options. You can choose which users are included and excluded from using this method.
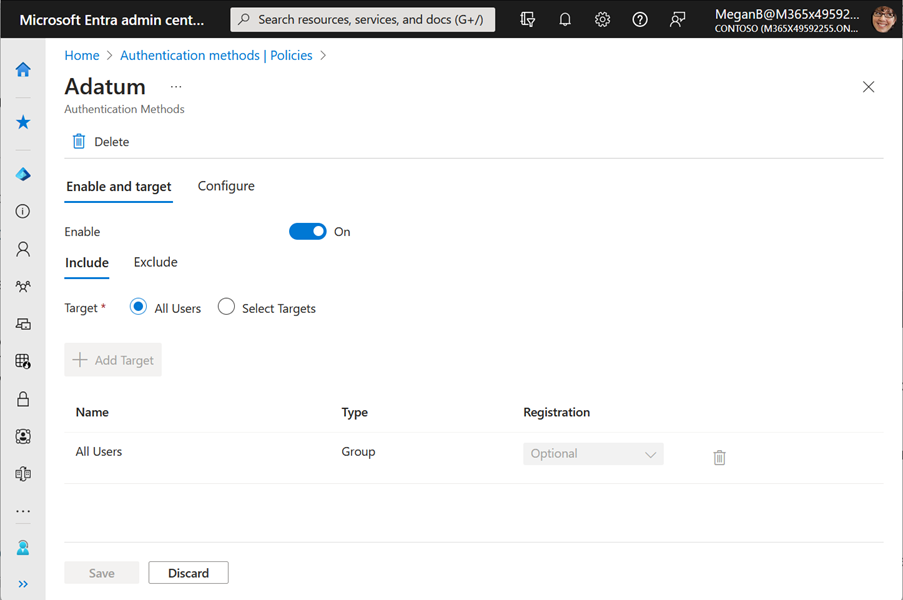
If you no longer want your users to be able to use the EAM, you can either:
To manage the Authentication methods policy by using Microsoft Graph, you need the Policy.ReadWrite.AuthenticationMethod permission. For more information, see Update authenticationMethodsPolicy.
Users who are enabled for the EAM can use it when they sign-in and multifactor authentication is required.
If the user has other ways to sign in and system-preferred MFA is enabled, those other methods appear by default order. The user can choose to use a different method, and then select the EAM. For example, if the user has Authenticator enabled as another method, they get prompted for number matching.
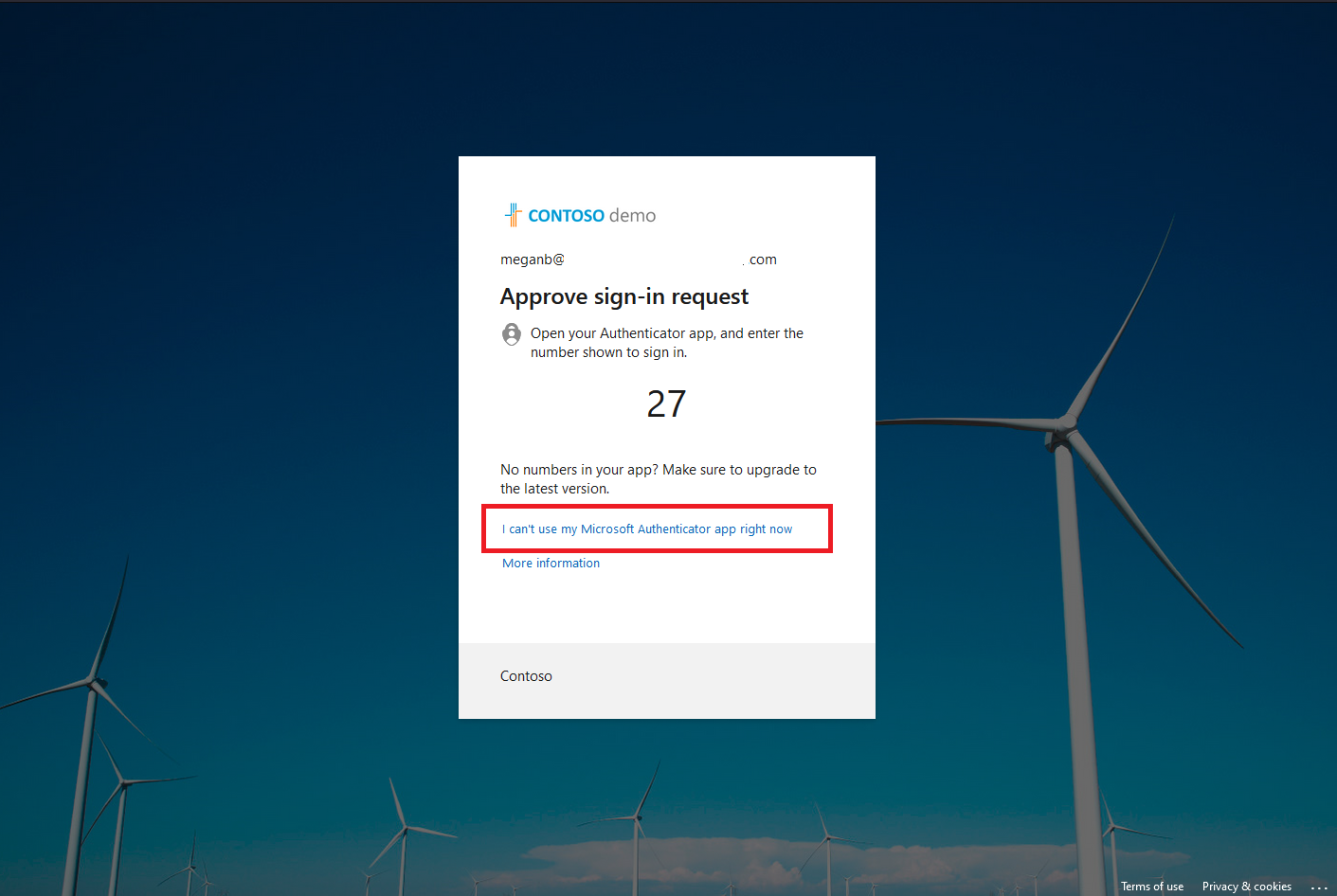
If the user has no other methods enabled, they can just choose the EAM. They're redirected to the external authentication provider to complete authentication.
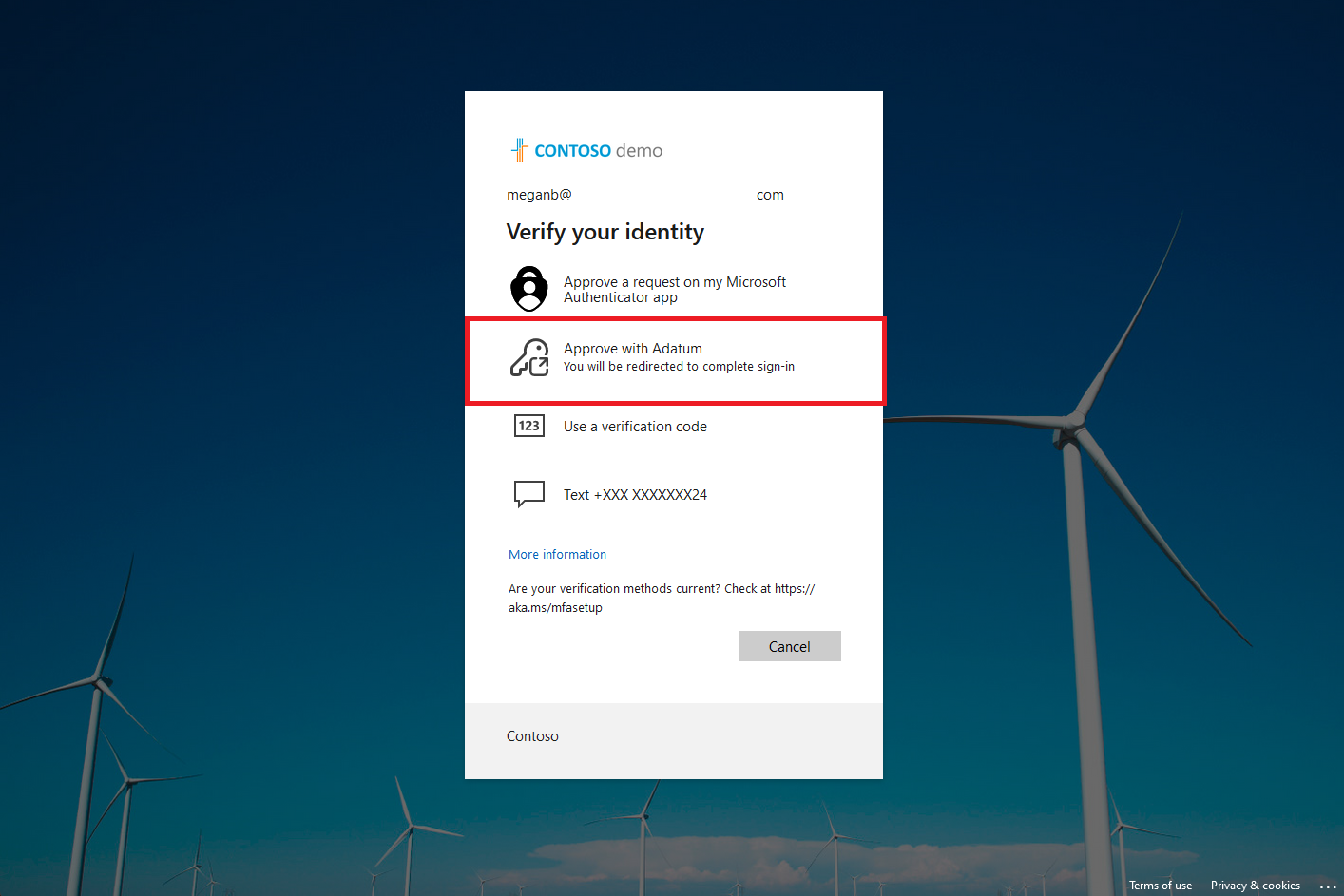
In the preview, all users in an include group for the EAM are considered MFA capable and can use the external authentication method for satisfying MFA. Users that are MFA-capable due to being an include target for an EAM are not included in reports on authentication method registration.
Бележка
We're actively working on adding registration capability for EAMs. Once registration is added, users that were previously using an EAM will need to have the EAM registered with Entra ID before they will be prompted to use it to satisfy MFA.
EAMs and custom controls can operate in parallel. Microsoft recommends that admins configure two Conditional Access policies:
Include a test group of users for each policy, but not both. If a user is included in both policies, or any policy with both conditions, the user has to satisfy MFA during sign-in. They also have to satisfy the custom control, which makes them redirected to the external provider a second time.
For more information about how to manage authentication methods, see Manage authentication methods for Microsoft Entra ID.
For EAM provider reference, see Microsoft Entra multifactor authentication external method provider reference (Preview).
Събитие
9.04, 15 ч. - 10.04, 12 ч.
Програмирайте бъдещето с AI и се свържете с Java колеги и експерти на JDConf 2025.
Регистрирайте се сегаОбучение
Модул
Manage authentication by using Microsoft Entra ID - Training
This module is designed to provide administrators with the knowledge and skills needed to manage authentication effectively using Microsoft Entra ID, ensuring secure access to resources and enhancing user experience.
Сертифициране
Microsoft Certified: Identity and Access Administrator Associate - Certifications
Demonstrate the features of Microsoft Entra ID to modernize identity solutions, implement hybrid solutions, and implement identity governance.
Документация
Learn how to configure an external authentication method (EAM) provider for Microsoft Entra multifactor authentication
Explains Microsoft Entra ID multifactor authentication (MFA) SAML/WSFed assertions.
Authentication methods and features - Microsoft Entra ID
Learn about the different authentication methods and features available in Microsoft Entra ID that help improve and secure sign-in events