Essential Eight multifactor authentication
This article details methods for achieving the Australian Cyber Security Centre (ACSC) Essential Eight Maturity Model for multifactor authentication using the Microsoft identity platform.
Why pursue the ACSC Essential Eight multifactor authentication guidelines?
MFA is one of the most effective controls an organization can implement to prevent an adversary from gaining access to a device or network and accessing sensitive information. When implemented correctly, MFA can make it more difficult for an adversary to steal legitimate credentials to undertake further malicious activities on a network. Due to its effectiveness, MFA is one of the Essential Eight from the ACSC’s Strategies to Mitigate Cyber Security Incidents Strategies to Mitigate Cyber Security Incidents.
Adversaries frequently attempt to steal legitimate user or administrative credentials when they compromise a network. These credentials allow them to easily propagate on a network and conduct malicious activities without other exploits, reducing the likelihood of detection. Adversaries also try to gain credentials for remote access solutions, including Virtual Private Networks (VPNs), as these accesses can further mask their activities and reduce the likelihood of being detected.
When MFA is implemented correctly, it's more difficult for an adversary to steal a complete set of credentials. Multifactor authentication requires the user to prove they have physical access to a second factor. Something that either they have (a physical token, smartcard, phone, or software certificate) or are (biometrics such as a fingerprint or iris scan).
Authentication basics
The ACSC Essential Eight Maturity Model for multifactor authentication is based on the National Institute of Standards and Technology (NIST) Special Publication 800-63 B Digital Identity Guidelines: Authentication and Lifecycle Management publication.
The following articles explain the concepts of multifactor authentication and how the NIST authenticator types map to Microsoft Entra authentication methods.
- NIST authentication basics
- NIST authenticator types and aligned Microsoft Entra authentication methods
Authenticator types
The ACSC addresses authenticator types in the Essential Eight Maturity Model FAQ common implementation questions regarding multifactor authentication (MFA).
- Windows Hello for Business uses biometrics (something users are) or a PIN (something users know). To unlock a key or certificate that is tied to a device’s Trusted Platform Module (something users have). To learn more, see Windows Hello for Business Overview.
Additional references regarding MFA by ACSC are the Essential Eight Maturity Model FAQ to refer to Section 5.1.1 – 5.1.9 in the NIST SP800-63 B Digital Identity Guidelines: Authentication and Lifecycle Management publication. These sections provide further information on the authenticator types. These types can be used for something users know, something users have, and something users are, that can be unlocked with something users know or are. The ACSC has further advice at Implementing multifactor authentication.
Phishing resistance
All Microsoft Entra authentication methods that meet maturity levels 2 and 3 use cryptographic authenticators that bind the authenticator output to the specific session being authenticated. They do this binding by using a private key controlled by the claimant for which the public key is known to the verifier. This satisfies the phishing resistance requirements for maturity levels 2 and 3.
According to the NIST, authenticators that involve the manual entry of an authenticator output, such as out-of-band and OTP (one-time pin) authenticators, SHALL NOT be considered verifier impersonation-resistant. The reason is because the manual entry doesn't bind the authenticator output to the specific session being authenticated. In a man-in-the-middle attack, an impostor verifier could replay the OTP authenticator output to the verifier and successfully authenticate.
The result is that any authenticator that doesn’t cryptographically verify that the sign in server is who it says it is, can be phished.
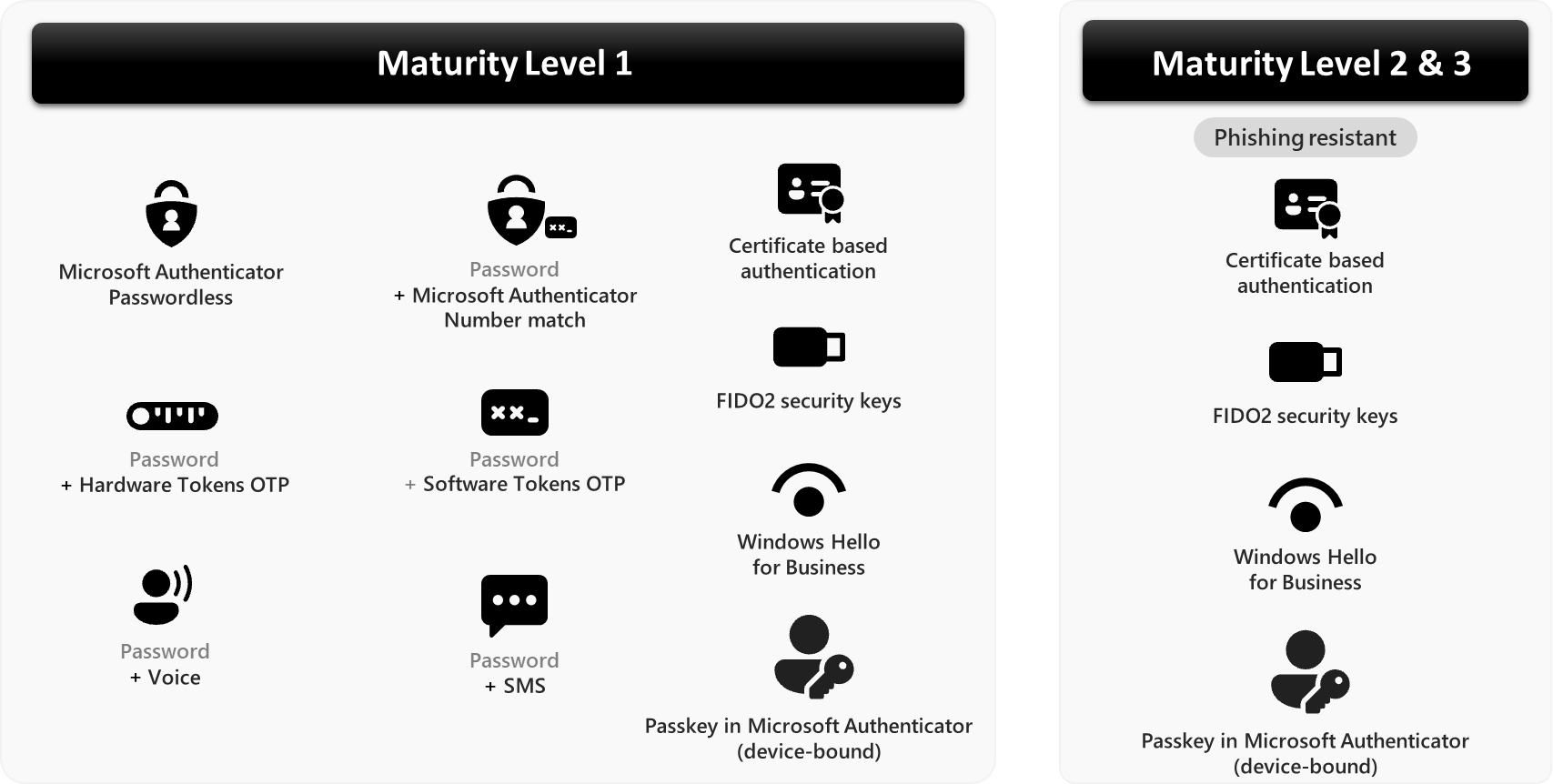
Permitted authenticator types
A summary of the key authenticator types that are permitted at each maturity level.
Next steps
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for