Hybrid Cloud Identity Part 4: Monitoring
At this step we have On-Premise Active Directory, integrated and federated with Azure AD using AD Connect and ADFS. We have an Exchange environment, integrated with Exchange Online. We have Multi-factor authentication for stronger security in place. What else do we need? Of course, we need to have a way to monitor that hybrid identity solution and react if something goes wrong. The best solution for that purpose is Azure AD Connect Health, which is included in Azure AD Premium. If can show the status of ADFS environment, On-Premise AD, Azure AD sync status and send notifications to administrators if alerts appear.
Deployment of Azure AD Connect Health
To deploy and configure Azure AD Connect Health, I will use the following:
- Azure AD Premium license-based subscription (or EMS Bundle), purchased from CSP Partner
- Azure Active Directory - kotlyarenko.onmicrosoft.com, synced and federated with On-Premise Active Directory corp.kotlyarenko.com
- On-Premise AD has 2 sites - Spb (on-premise, with DC01) and Moscow (hosted in service provider DC, with DC02).
- AD FS environment includes ADFS Server (ADFS01) and ADFS Proxy (ADFSGW)
- Azure AD Connect is deployed on the dedicated server - ADCON01.
Check the official installation manual.
Add Azure AD Connect Health
Login to Azure Portal and click New -> Security and Identity -> Azure AD Connect Health 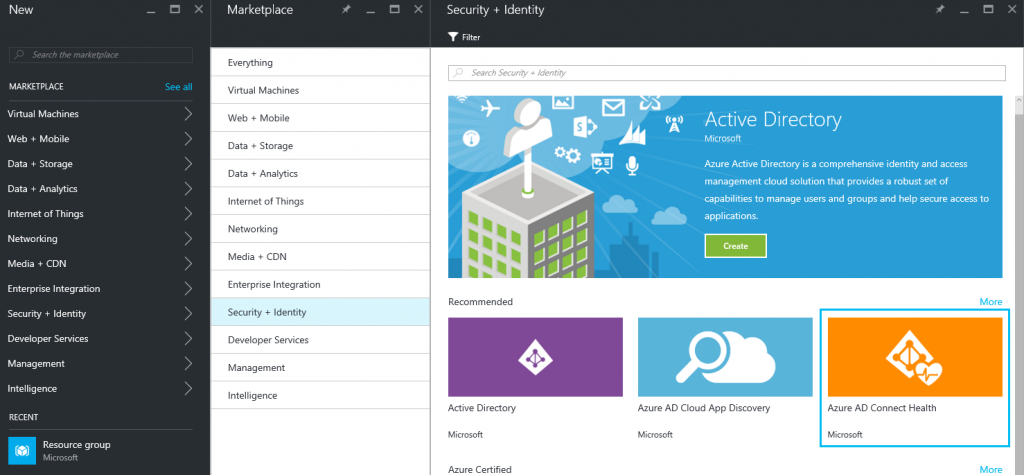
You will see the directory, where you have Global Administrator rights and Azure AD Premium mode activated, click Create.
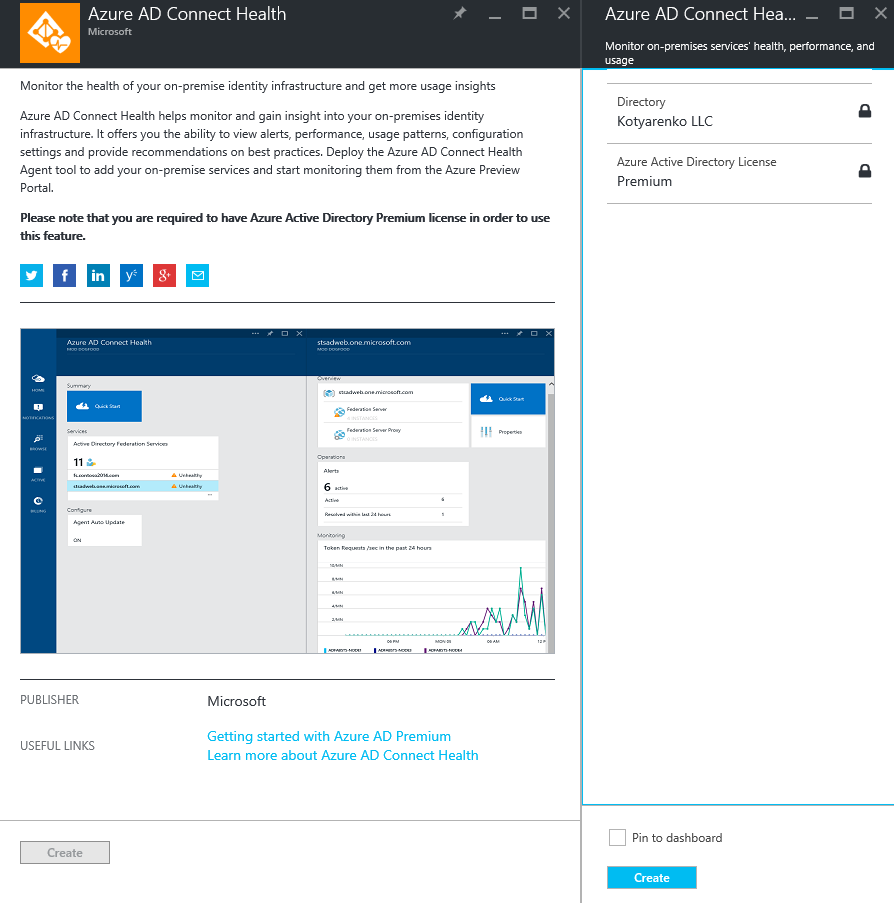
Then click More Services -> Azure AD Connect Health to open Azure AD Connect Health menu. Click Quick Start and download 3 installers:
- Azure AD Connect Health agent for ADDS
- Azure AD Connect Health agent for ADFS
- The latest version of Azure AD Connect.
Install agent on DCs
Next step - you need to install Azure AD Connect Health agent for ADDS on every domain controller in your On-Premise AD.

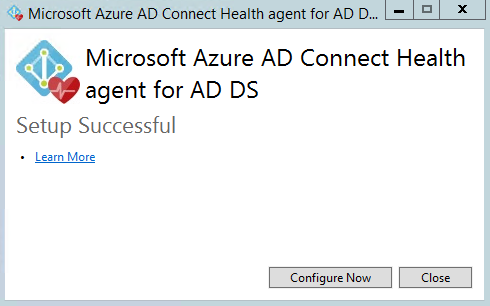 Configuration script will be launched after the installation. You will need to provide Azure AD Global Administrator credentials.
Configuration script will be launched after the installation. You will need to provide Azure AD Global Administrator credentials.
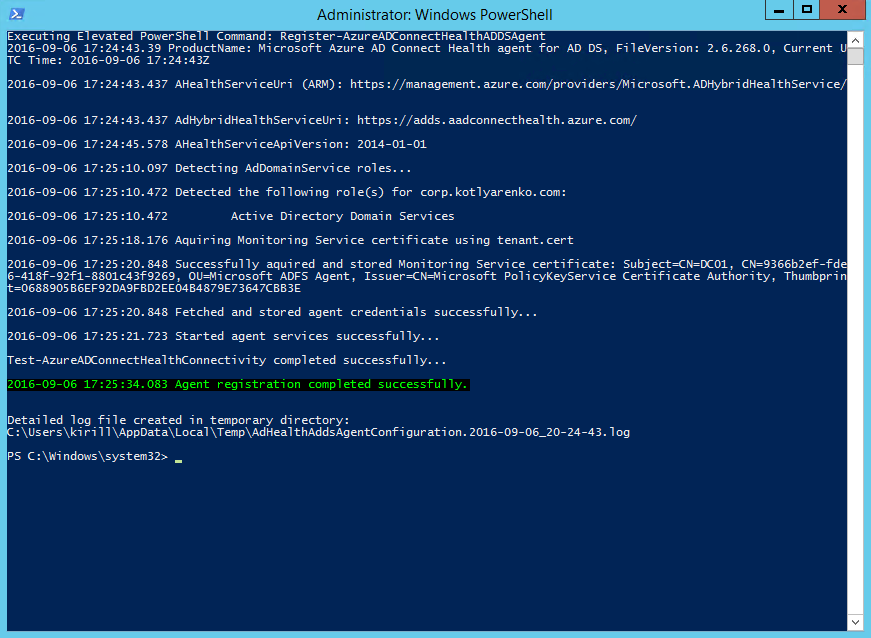 Repeat this procedure on every domain controller.
Repeat this procedure on every domain controller.
Install agent on ADFS
Now you need to install Azure AD Connect Health agent for ADFS on every ADFS Server and ADFS Proxy.
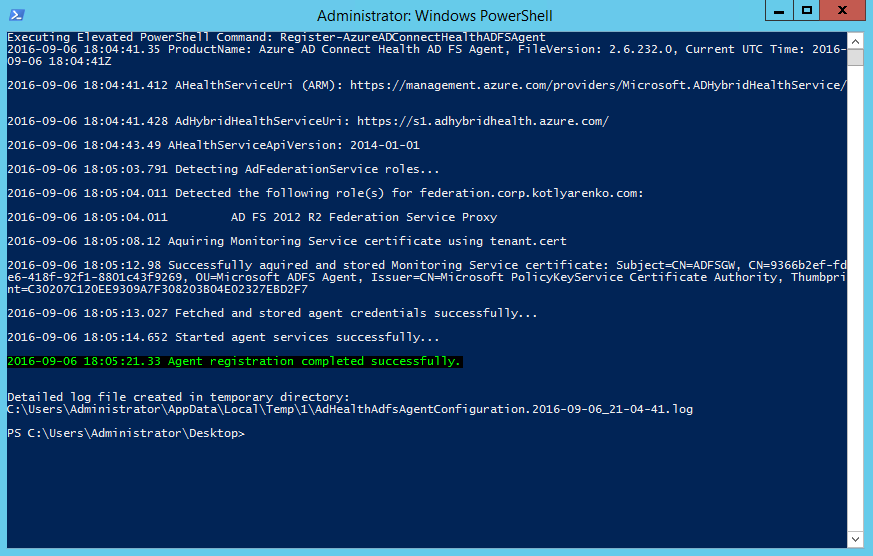
 On ADFS Gateway you shouldn't see any errors or warning:
On ADFS Gateway you shouldn't see any errors or warning:
But on ADFS Servers you probably will see a warning that ADFS Auditing is not enabled correctly: 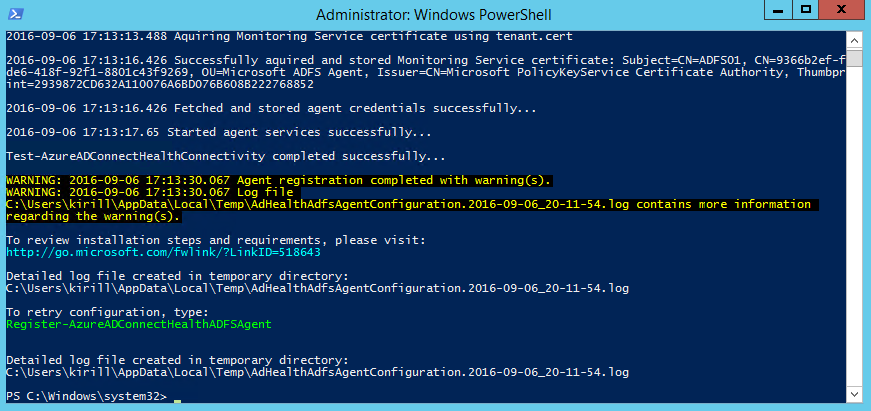
To fix that, run this command on every ADFS Server with elevated admin credentials:
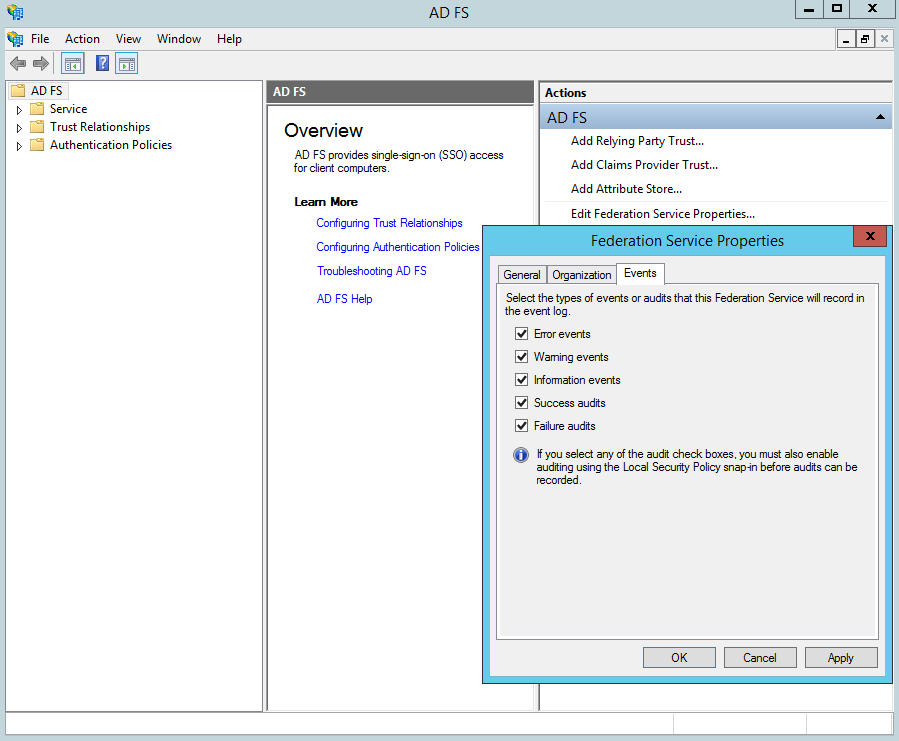
auditpol.exe /set /subcategory:"Application Generated" /failure:enable /success:enable 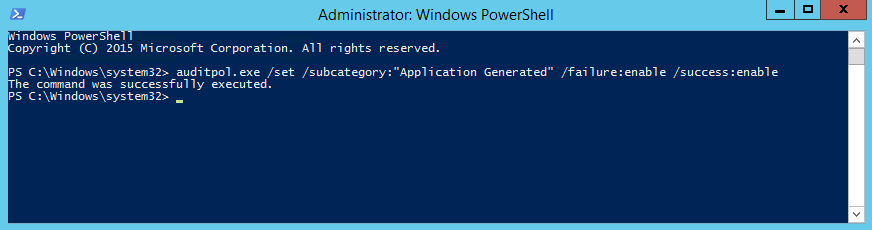 And then open ADFS Management Console, click Edit Federation Service Properties and check Success Audits and Failure Audits.
And then open ADFS Management Console, click Edit Federation Service Properties and check Success Audits and Failure Audits.
 Enable Health Agents on AD Connect server
Enable Health Agents on AD Connect server
Next step maybe not required in your case. Open services.msc on your Azure AD Connect server and check if Azure AD Connect Health Sync Insights Service and Azure AD Connect Health Sync Monitoring Service presented there:
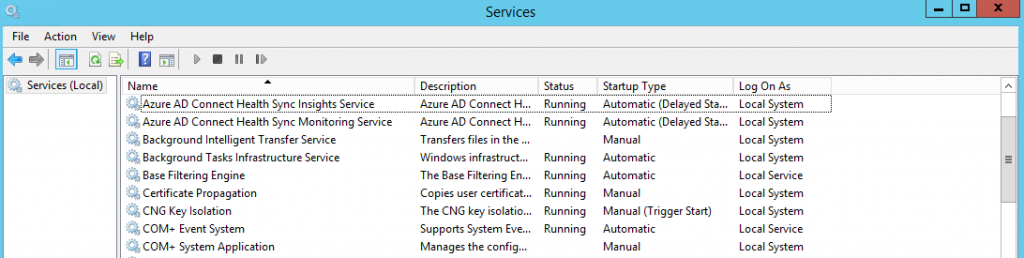 If they are missing, then it means that Azure AD Connect Health Sync agent wasn't available in Azure AD Connect yet when you've installed it. To solve this, download the latest installer of Azure AD Connect and run the installer. Choose Repair:
If they are missing, then it means that Azure AD Connect Health Sync agent wasn't available in Azure AD Connect yet when you've installed it. To solve this, download the latest installer of Azure AD Connect and run the installer. Choose Repair: 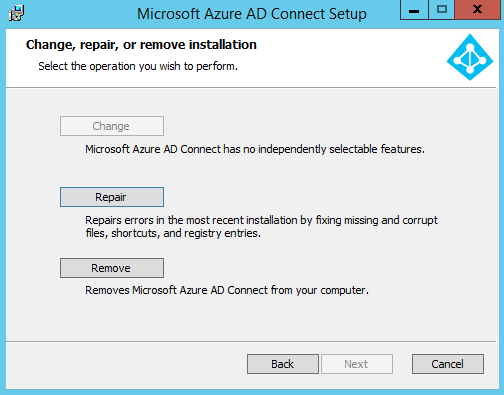 After the installer will complete, choose Customize synchronisation options:
After the installer will complete, choose Customize synchronisation options: 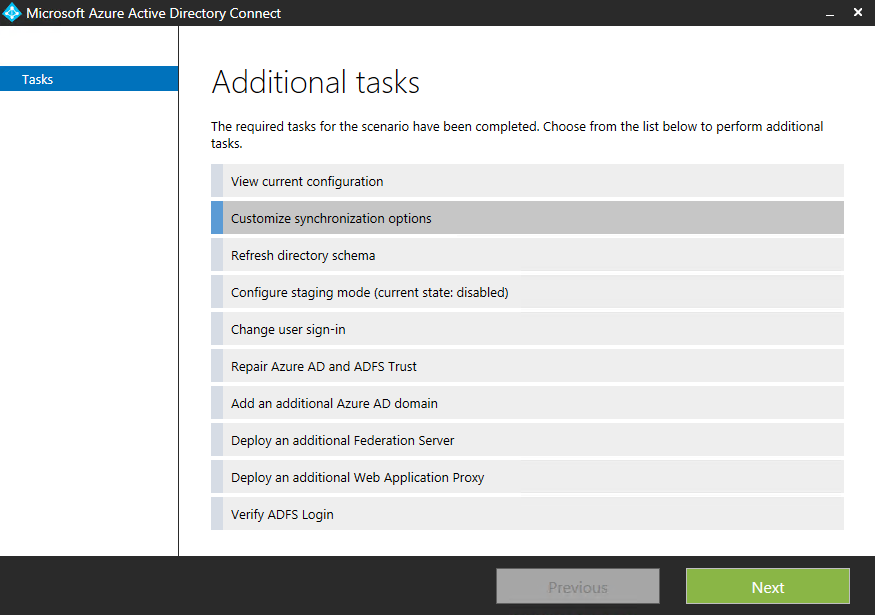
Provide Global Admin credentials and click Next next next, we don't need to change anything here. You will see that Azure AD Connect Health agent for sync is being installed:
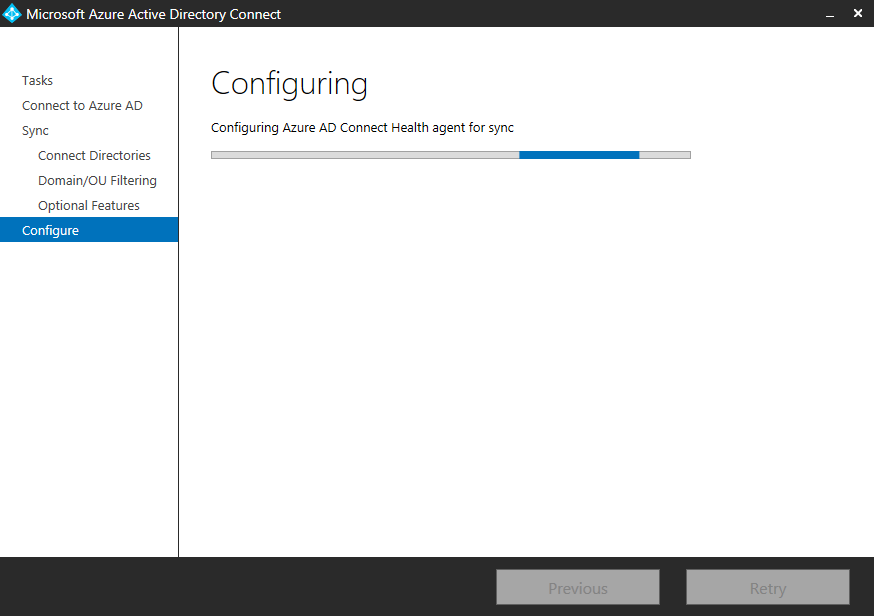
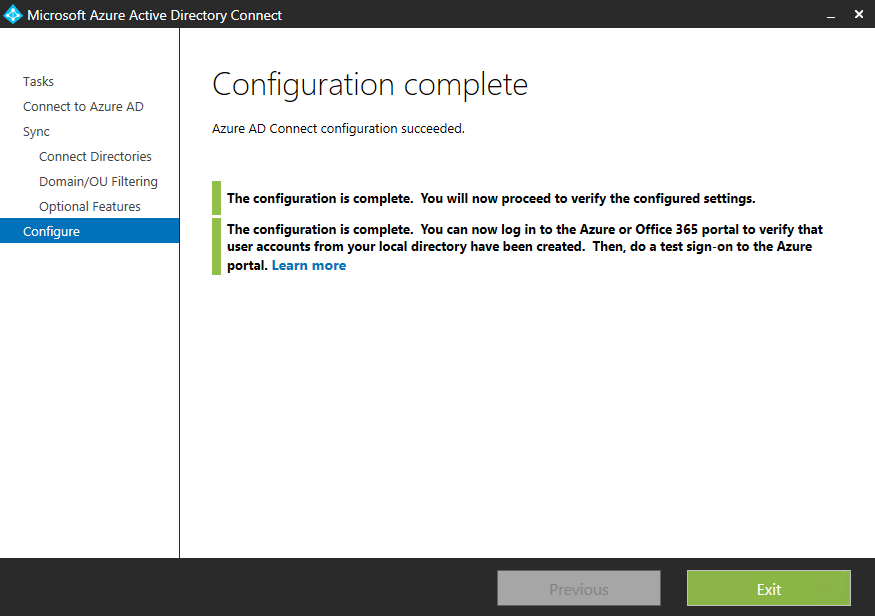 Installation complete!
Installation complete!
Configure Azure AD Connect Health
Return back to Azure Portal and open Azure AD Connect Health menu. You should see 3 panes - Active Directory Federation Services, Azure Active Directory Connect and Azure Active Directory Domain Services. 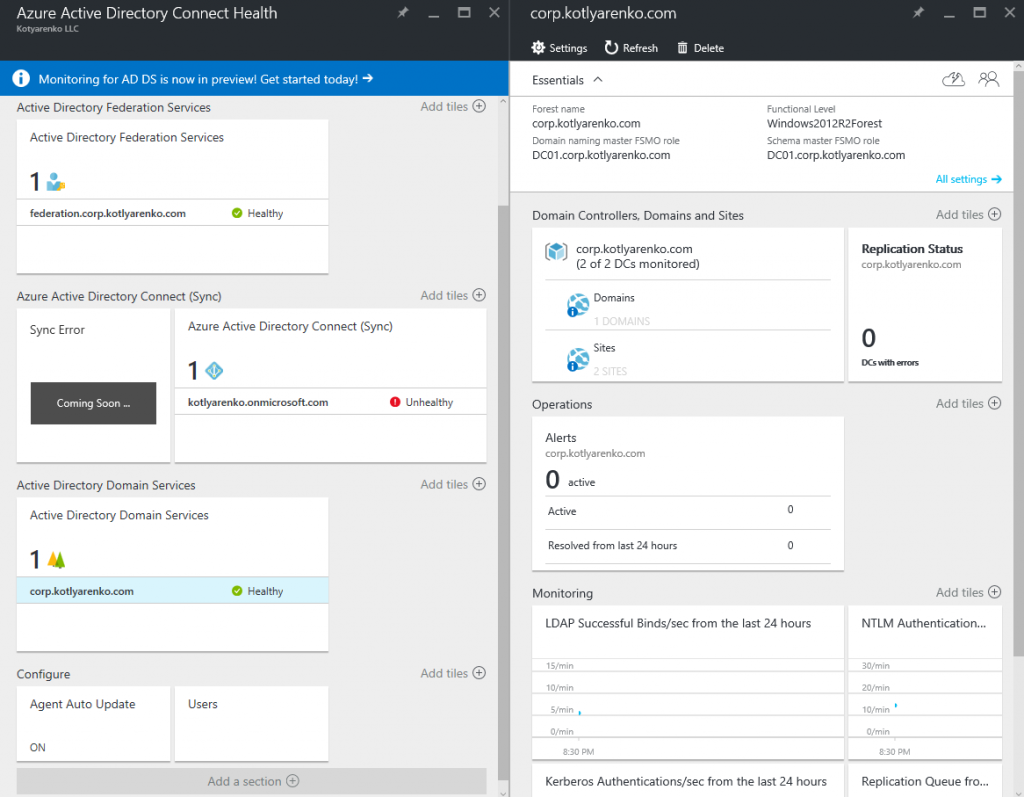 Click Azure Active Directory Connect -> Settings and change the switch to "On" to enable to evaluate all alerts.
Click Azure Active Directory Connect -> Settings and change the switch to "On" to enable to evaluate all alerts.
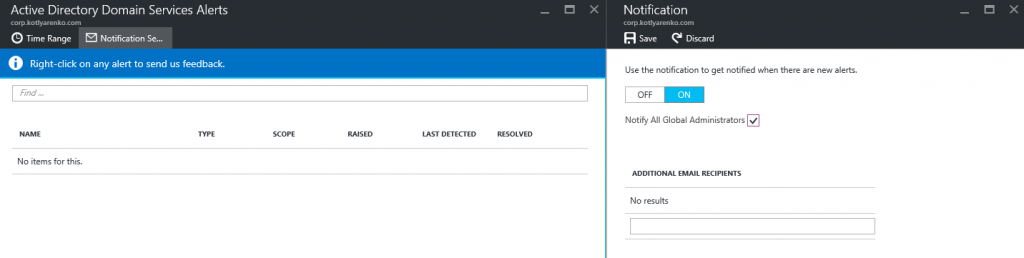
In Alert menu you can configure e-mail notifications:
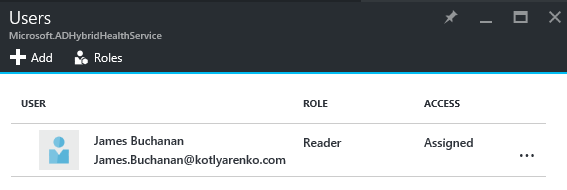
 You can also assign access (including Read-only) to Azure AD Connect Health for other users in the current Azure AD:
You can also assign access (including Read-only) to Azure AD Connect Health for other users in the current Azure AD:
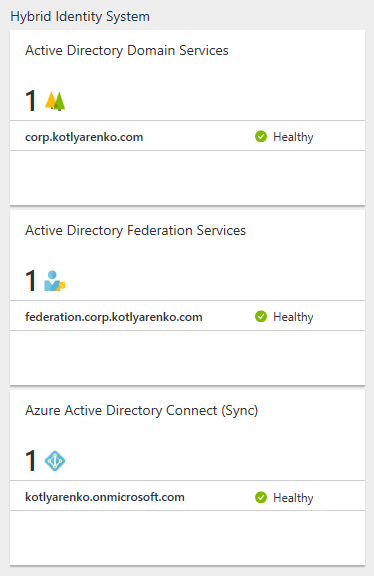
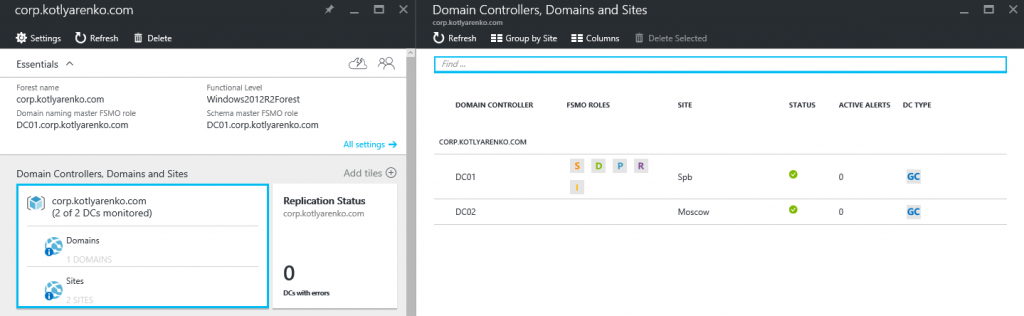
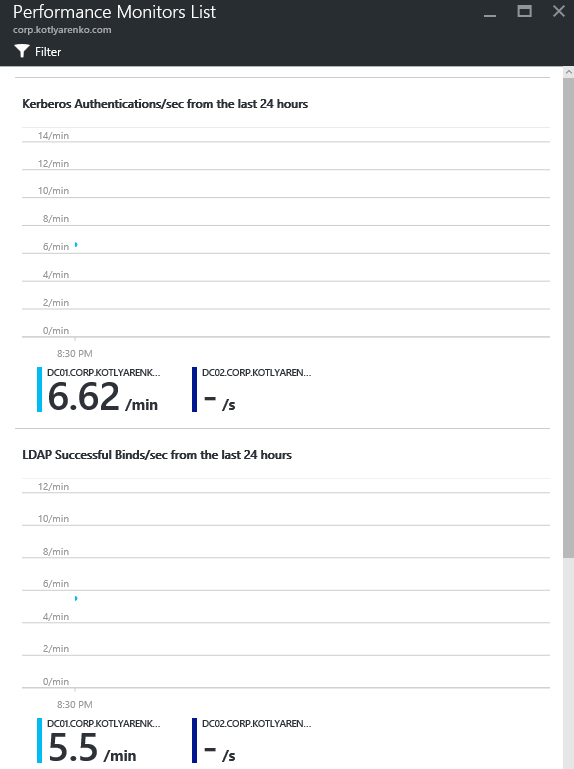
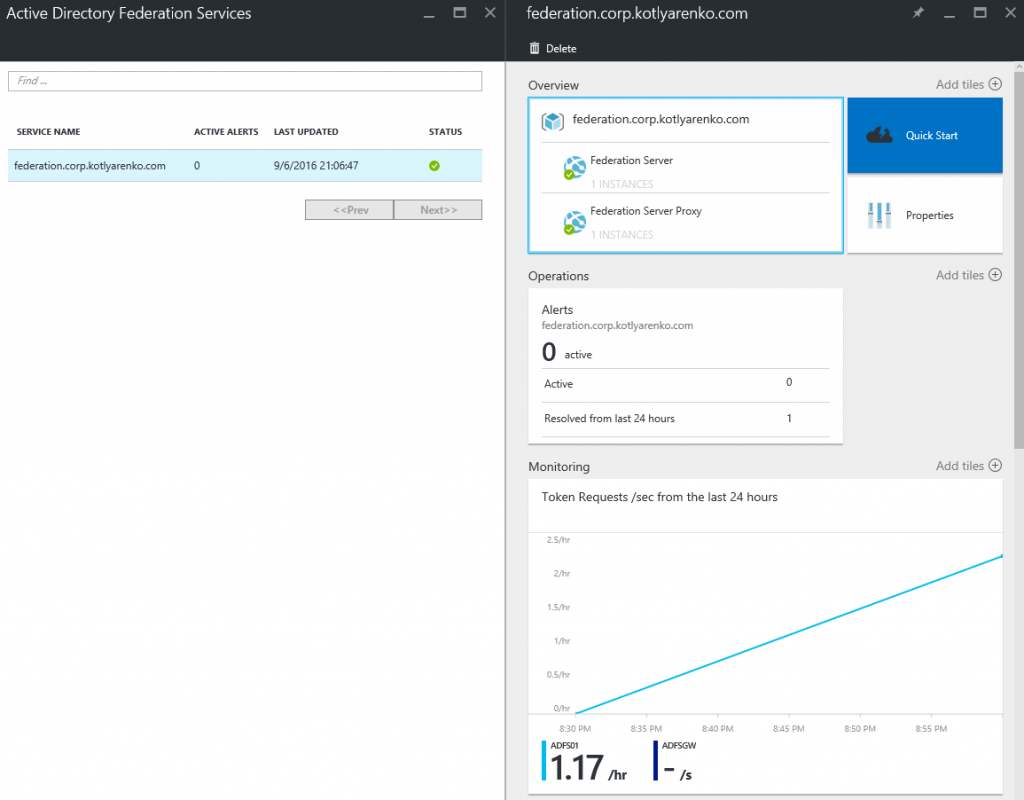
 That's all. Enjoy the statuses of your On-Premise AD, Azure AD and ADFS and click any status if you need more details.
That's all. Enjoy the statuses of your On-Premise AD, Azure AD and ADFS and click any status if you need more details.
This post is a part of the Hybrid Cloud Identity series:
Part 1 - Integration of On-Premise AD and Azure AD using Azure AD Connect and ADFS Part 2 - Hybrid Exchange Part 3 - Azure Multi-factor Authentication
Part 4 - Azure AD Connect Health (you are here).
Comments
- Anonymous
September 10, 2016
Hi Thanks for another Excellent contribution.