SPLA Reporting - Adding virtualization hosts to SILA
In previous posts I've described the components of Microsoft SPLA Reporting toolset and provided a step-by-step guide how to install SILA Server in your production environment.
In this post I'll show how to add virtualization hosts to SILA. You can add Microsoft Hyper-V, VMWare vSphere (ESXi), Citrix XenServer, KVM and Xen virtualization hosts. I will provide step-by-step instructions for 2 most popular hypervisors among my partners - Hyper-V and vSphere, and a brief overview of XenKVM procedure. Nobody uses Citrix XenServer among my partners, so sorry, I have no details here.
To continue with a deployment, let's check that you're done with previous steps:
- SILA server is up and running
- SIL Certificate (pfx file) is issued and stored in a good location. You remember the PFX file password and certificate thumbprint.
Add Hyper-V hosts
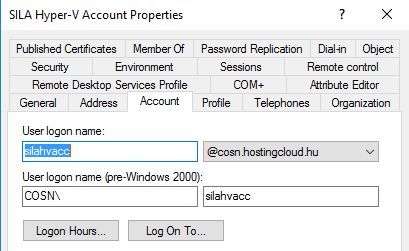
To create the most full inventory reports, you need to add all your Hyper-V hosts to SILA server. VMM is not required for this. I've tested SILA with Hyper-V based on Windows Server 2012 R2 and Windows Server 2016 Technical Preview 4. My Hyper-V hosts are joined to the Active Directory domain cosn.hostingcloud.hu and stored in the "Hyper-V Hosts" organizational unit. First of all, create SILA Hyper-V account in AD, which SILA will use to connect to Hyper-V hosts. In my case it is silahvacc@cosn.hostingcloud.hu.
We need to add this user account to local groups "Hyper-V Administrators" and "Remote Management Users" on every Hyper-V host. You can do it manually, but if you have a lot of Hyper-V hosts it is boring. To eliminate manual activities, I will use a domain Group Policy. Open Group Policy Management console using any Domain Admin user account. You can go to any domain controller and open it there, or you can install this console on SILA server.
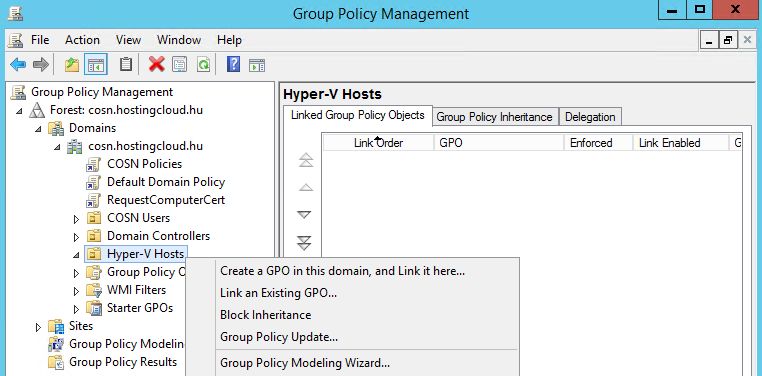
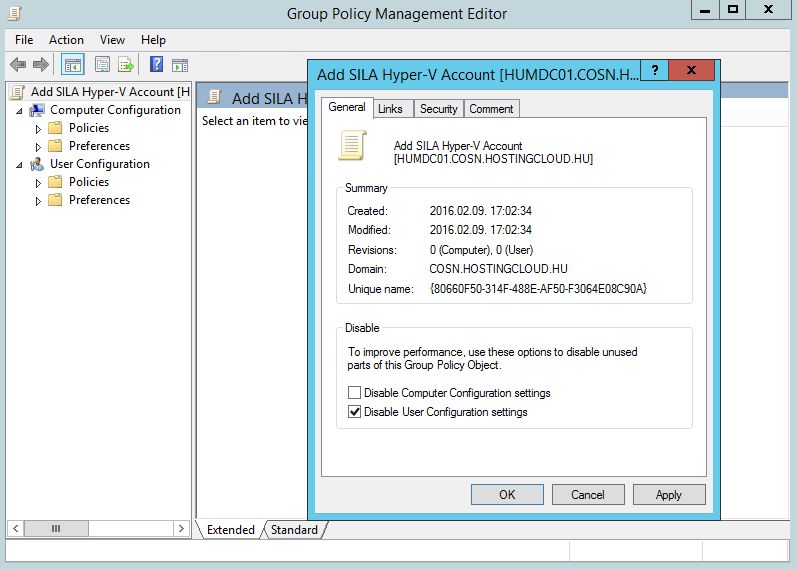
Click on the organizational unit with Hyper-V hosts and choose "Create a GPO in this domain and Link it here". I will call it "Add SILA Hyper-V Account".
Go to the GPO policies and choose "Disable User configuration policies", because this policy will be applied only on computer settings.
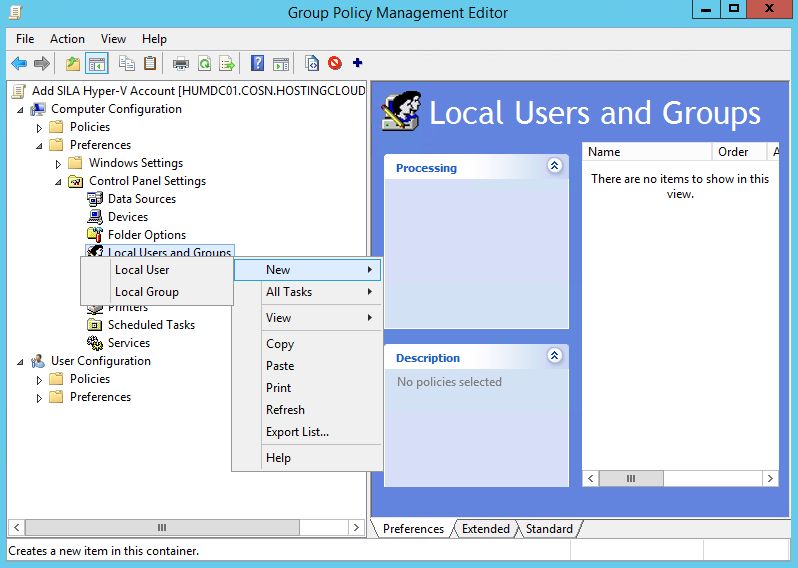
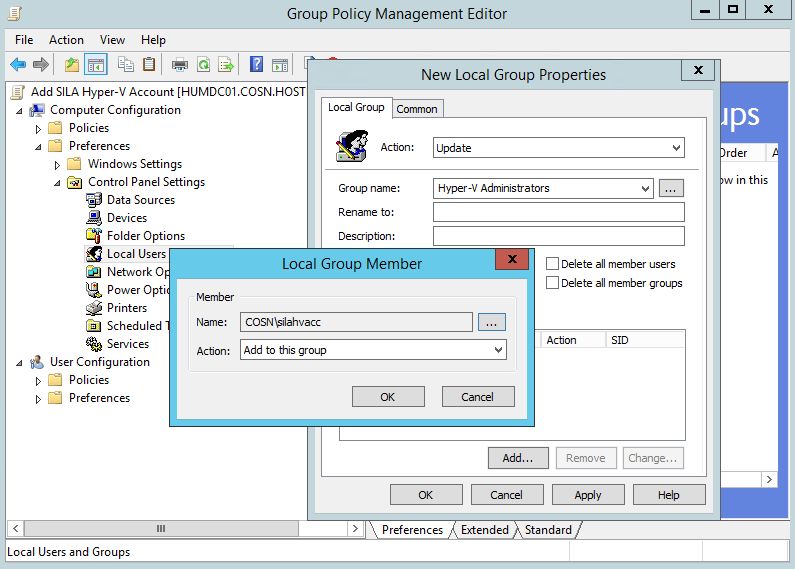
After that, go to Computer Configuration -> Control Panel Settings -> Local Users and Groups and click "Local Group".
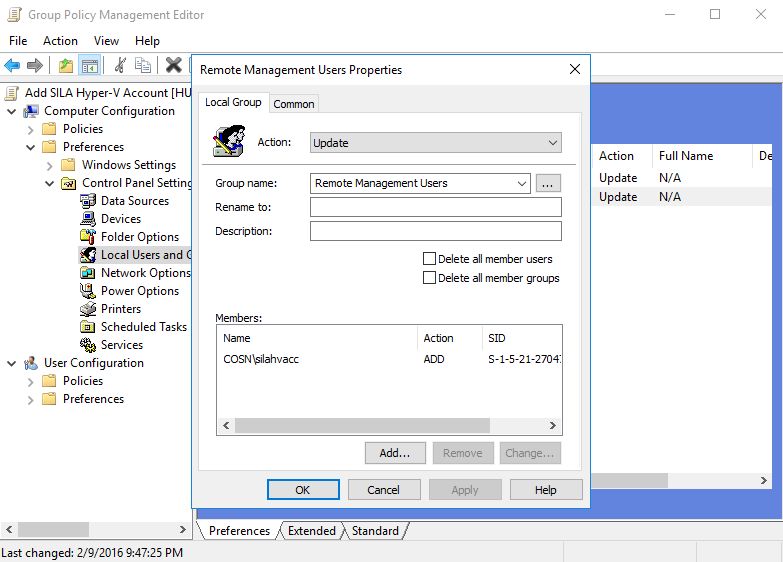
Choose Action = Update, in Group Name field type "Hyper-V Administrators". Click "Add" and choose the AD account that you've recently created. Repeat the same for "Remote Management Users" group.
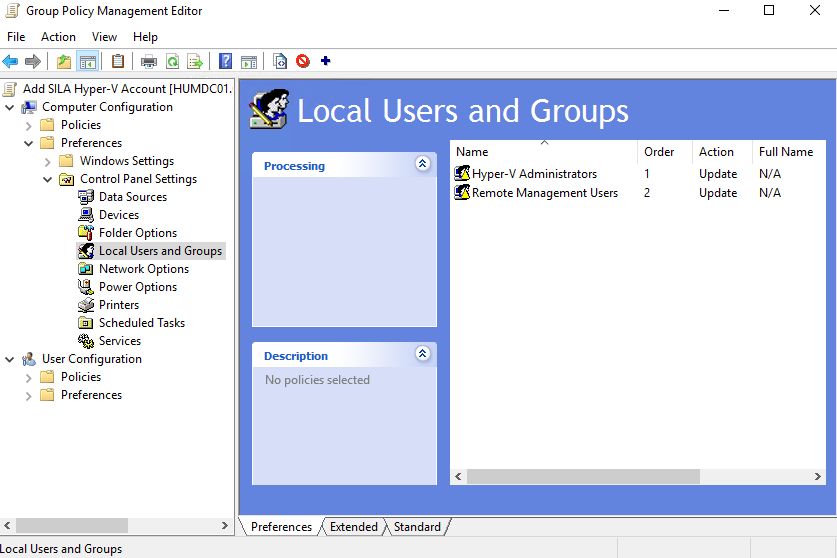
Click OK and wait for an hour - Hyper-V hosts need to update Group policies and in my case - add silahvacc@cosn.hostingcloud.hu account to local "Hyper-V Administrators" and "Remote Management Users" groups.
OK, we're all set to add Hyper-V hosts to SILA. Logon to SILA Server using SILA Service Account (in my case - silaacc).
To add Hyper-V hosts manually one by one, just run these commands in PowerShell and specify SILA Hyper-V Account credentials (in my case - silahvacc@cosn.hostingcloud.hu).
$Credentials = Get-Credential
$HostFQDN = " FQDNOFHYPERVHOST " Add-SILVMHost -VMHostname $HostFQDN -hostcredential $Credentials
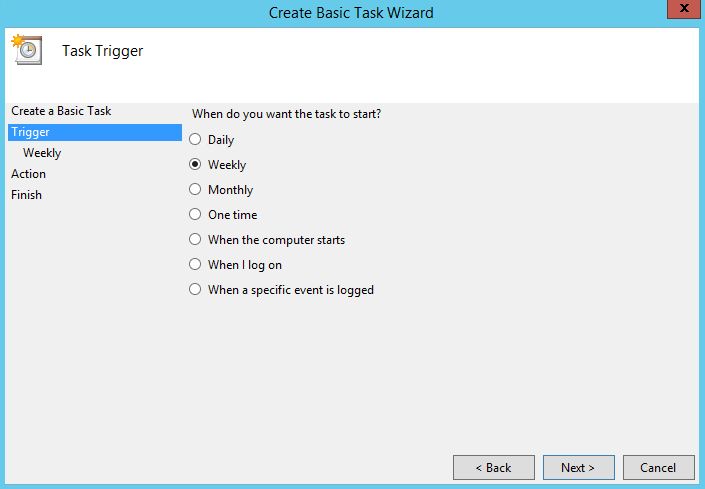
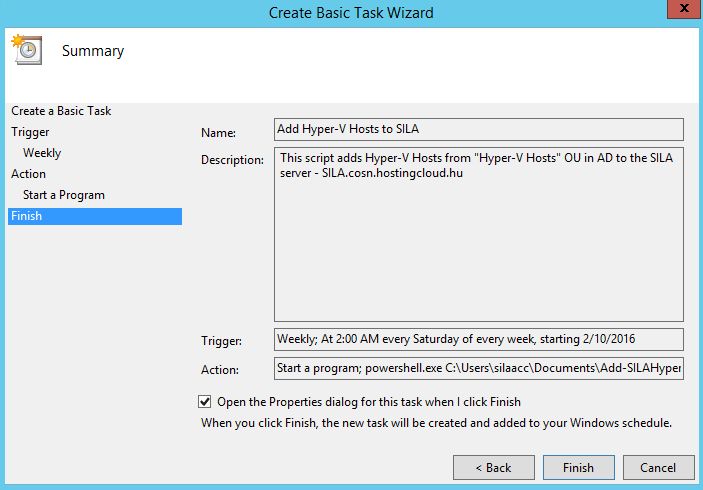
When you run this command, SILA service tries to connect to the remote host directly using the specified credentials and determine its hypervisor type. SILA automatically detects if it is a Hyper-V, ESXi, KVM of Xen host. But if you have a lot of Hyper-V hosts, I recommend you to automate this process with a scheduled PowerShell script. This script finds all computer accounts in the specified OU and adds them to SILA. You can schedule this script for a weekly basis using task scheduler.
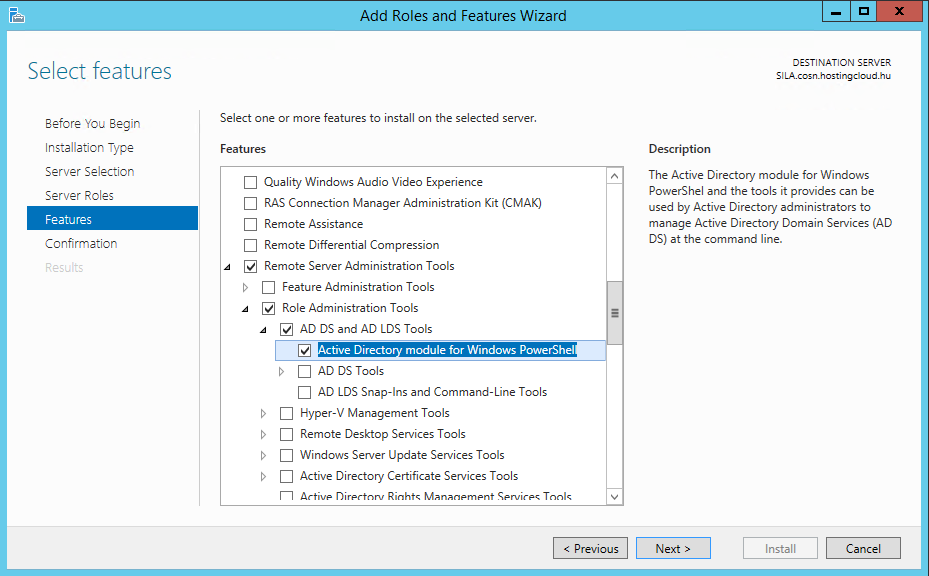
First of all, install Active Directory PowerShell extensions on the SILA server and check if it works:
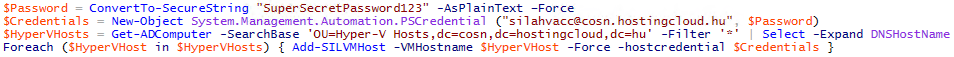
Here is the script:
$Password = ConvertTo-SecureString " SILAHyperVAccountPassword " -AsPlainText –Force
$Credentials = New-Object System.Management.Automation.PSCredential (" SILAHyperVAccountName@domain.com ", $Password)
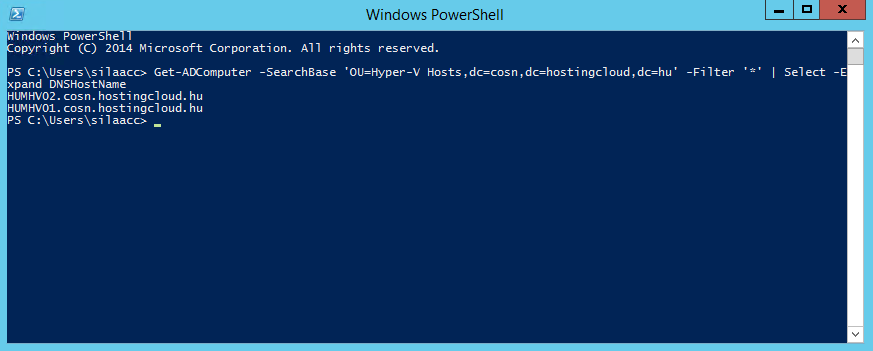
$HyperVHosts = Get-ADComputer -SearchBase 'OU= yourdomain,dc=domain,dc= com ' -Filter '*' | Select -Expand DNSHostName
Foreach ($HyperVHost in $HyperVHosts) { Add-SILVMHost -VMHostname -$HyperVHost -Force -Hostcredential $Credentials }
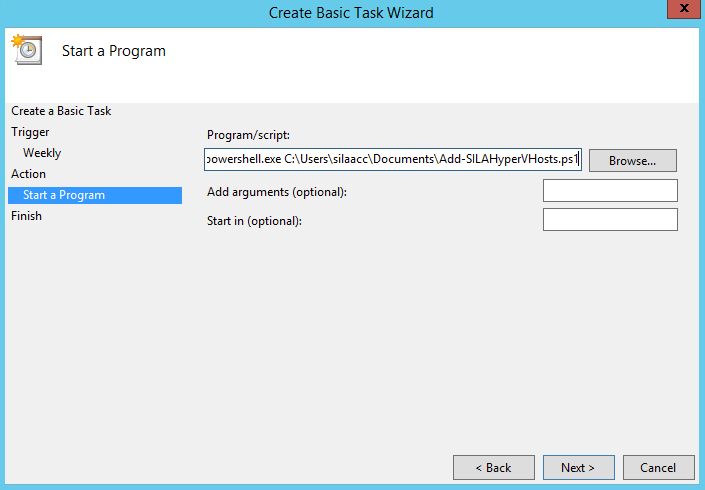
I saved this script to SILA Service Account "Documents" folder. I my case it is C:UserssilaaccDocumentsAdd-SILAHyperVHosts.ps1.
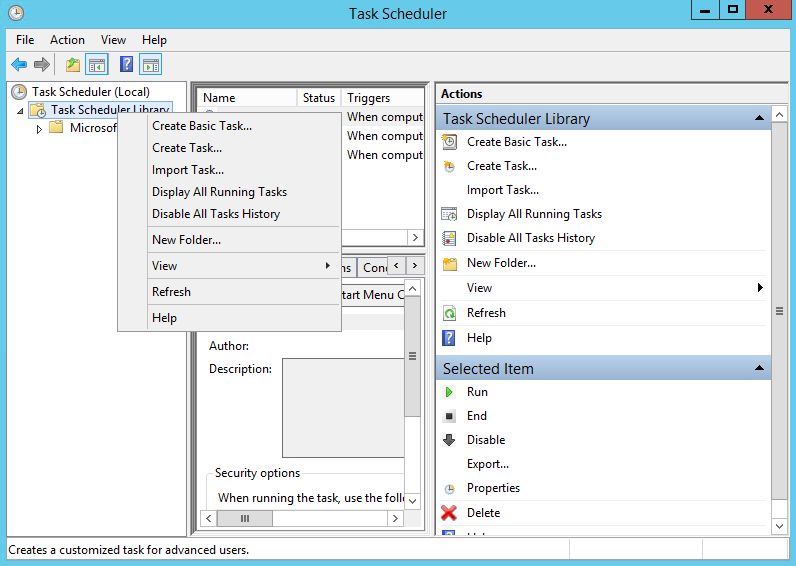
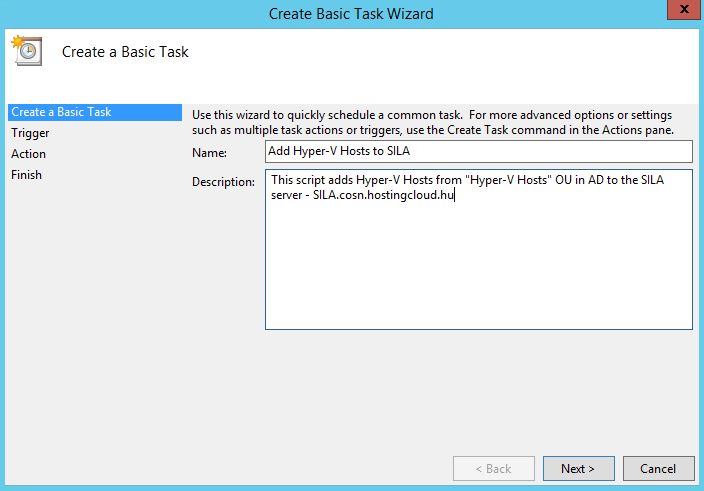
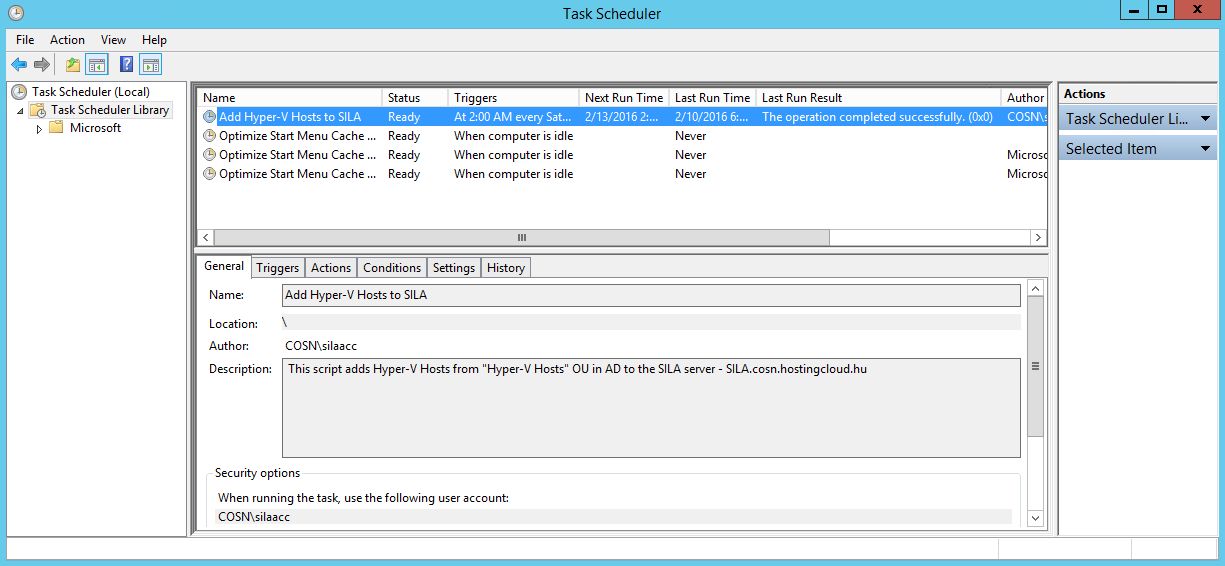
Open Task Scheduler to create a task to run this script once a week. Click "Create Basic Task".
Program to sun: powershell.exe C:SCRIPTLOCATIONSCRIPTFILENAME.ps1
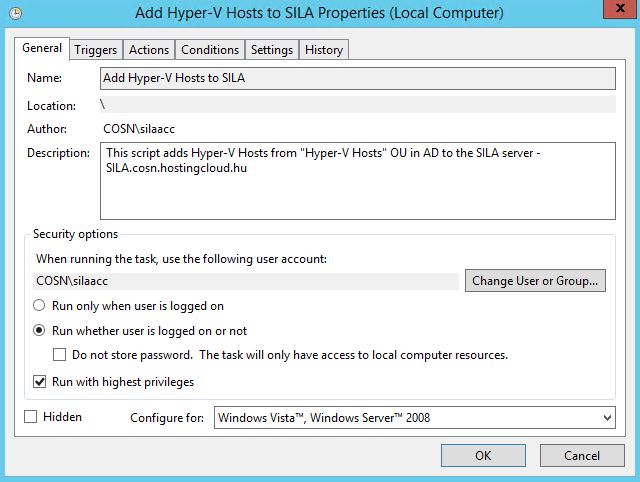
After creating the task, open its properties and select "Run whether user is logged on or not" and "Run with highest privileges".
Run the task and check that last run result is successful.
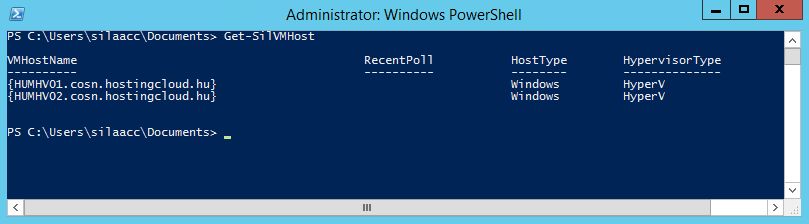
Check that all hosts in the specified OU were added to SILA. To do this, run "Get-SILVMHost" command.
Check that all needed hosts are present and HypervisorType is "HyperV". If it is "Unknown", then something is wrong here. Check that SILA can connect to the remote host using the specified credentials. Ping the remote host using the specified FQDN and check that the SILA Hyper-V Account you've used is added to "Hyper-V Administrators" and "Remote Management Users" local groups.
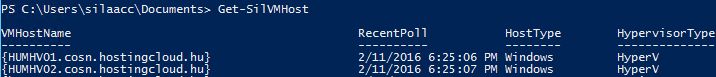
If you see that there were recent polls, then everything is OK:
There is an alternative way to add Hyper-V hosts if you have System Center Virtual Machine Manager (VMM) in your organization, and those Hyper-V hosts are managed by VMM. To do this you need to add SILA Hyper-V Account (silavmacc) to VMM group with Fabric Management permissions. This user account must be able to list all Hyper-V hosts in your environment and it must be added to "Hyper-V Administrators" and "Remote Management Users" local groups on every host you plan to add to SILA. After that, run these commands under SILA Service Account and specify SILA Hyper-V Account credentials when prompted.
$Credentials = Get-Credential
Add-SilVMHost -HostCredential $Credentials -SCVMMTargetName " FQDNOFVMMSERVER "
But remember - this command is only used to discover all available Hyper-V hosts. After that SILA will try to connect directly to every host as usual. To be honest - I don't see any additional value in this case. For my it is much simplier to add all Hyper-V hosts to the single OU and configure+add all of them using the scheduled script I've provided.
Add VMWare vSphere hosts
SILA polls data from vSphere hosts directly using PowerCLI. vCenter is not required for SILA. I've tested this solution with vSphere 5.5 and vSphere 6.0. Although v6.0 is not officially supported, it works without any issues.
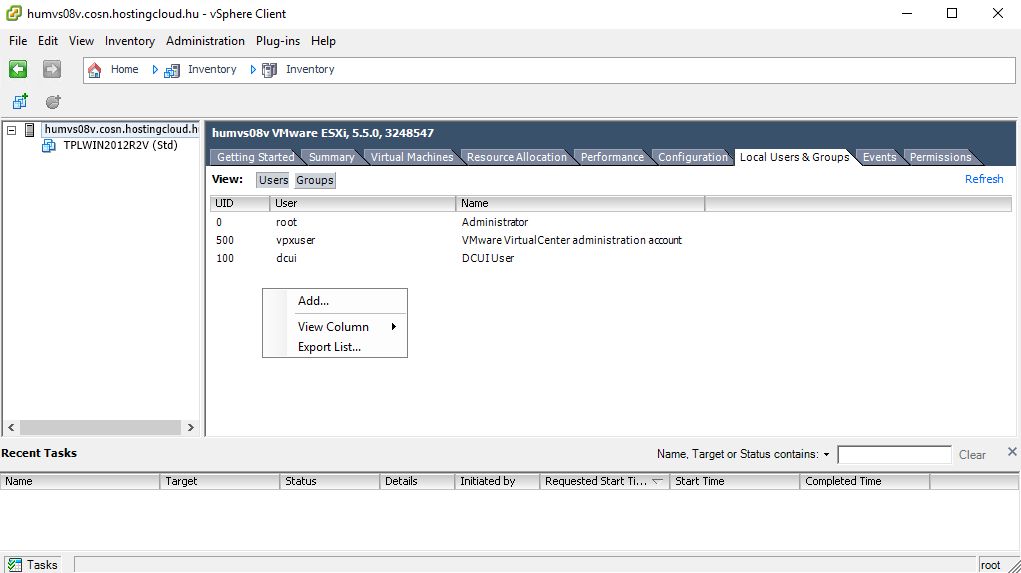
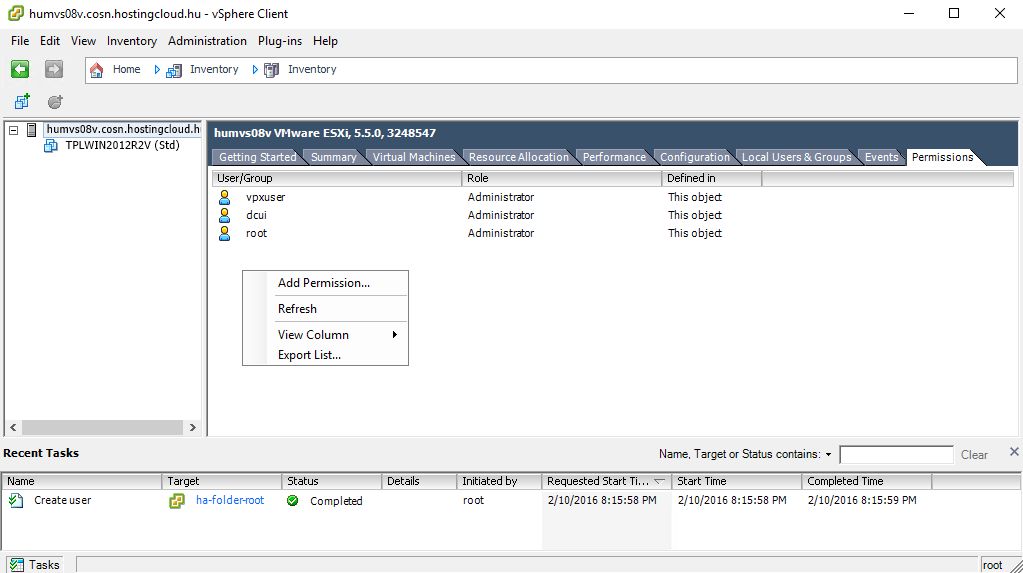
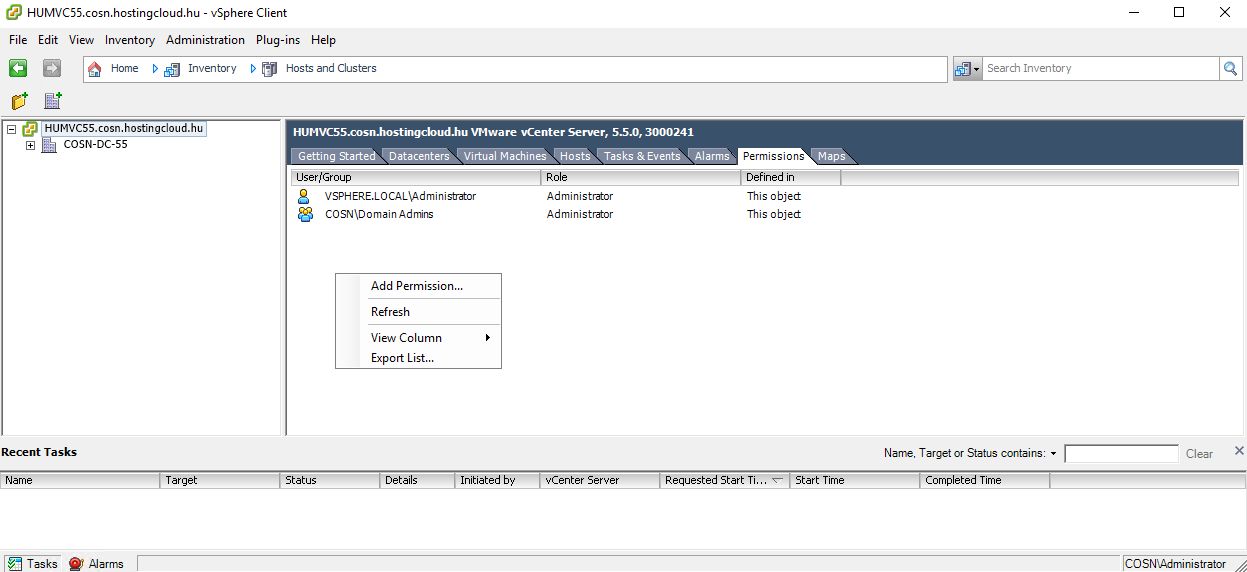
To configure vSphere host for SILA manually, connect to vSphere host directly using vSphere Client. Go to "Local Users & Groups" tab.
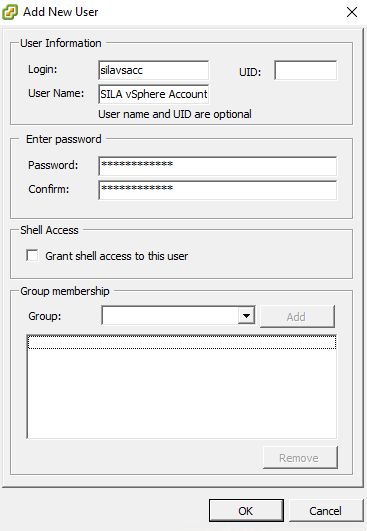
Create a new user, that will be used as SILA vSphere Account. In my case it is "silavsacc".
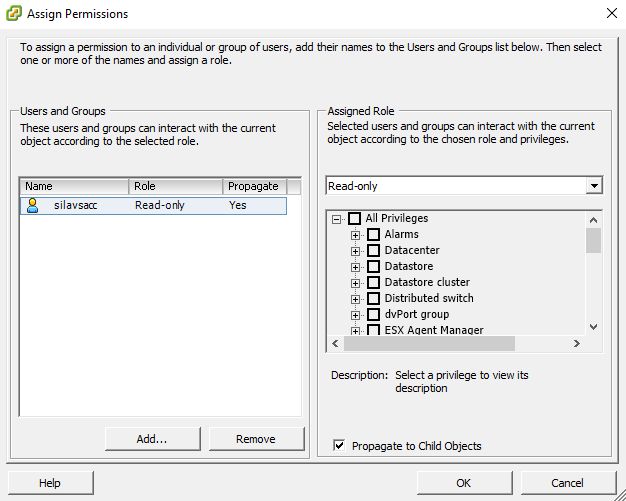
Go to "Permissions" tab and assign Read-only permissions for the user.
To automate the process of creating such local user on every vSphere host, use PowerCLI. Here is the example of the script:
$VMHostname=" FQDNofvSphereHost "
$rootpassword=" vspherehostrootpassword "
$accname=" silavsphereaccountname "
$accpass=" silavsphereaccountpassword "
Connect-VIServer -Protocol https -Server $VMHostname -User root -Password $rootpassword
New-VMHostAccount -Id $accname -Password $accpass -Description "SILA vSphere Account"
New-VIPermission -Entity $VMHostname -Principal $accname -Role ReadOnly -Propagate:$true
But I want to warn you - I receive an error on the last command with a description: "Local group accounts are not supported since ESX version 5.1". I couldn’t find a resolution of this problem, here is a thread on VMWare site. So this script creates a user, but it doesn't assign ReadOnly permissions, you need to do it manually via vSphere Client. If you'll solve this issue - tell me the solution, please.
After SILA vSphere account with ReadOnly permission is created on every vSphere host, you can just add them one by one. To do this, just run these commands in PowerShell under SILA Service Account and specify SILA vSphere Account credentials when prompted (in my case - silavsacc).
$Credentials = Get-Credential
$HostFQDN = " FQDNOFVSPHEREHOST " Add-SILVMHost -VMHostname $HostFQDN -hostcredential $Credentials
Run Get-SILVMHost command to check that the host was added. Check that the host HypervisorType is "ESXi". If it is "Unknown", then something is wrong here. Check that SILA can connect to the remote host using the specified credentials. Ping the remote host using the specified FQDN and check that the SILA vSphere Account you've used is created on a host and assigned ReadOnly permissions.
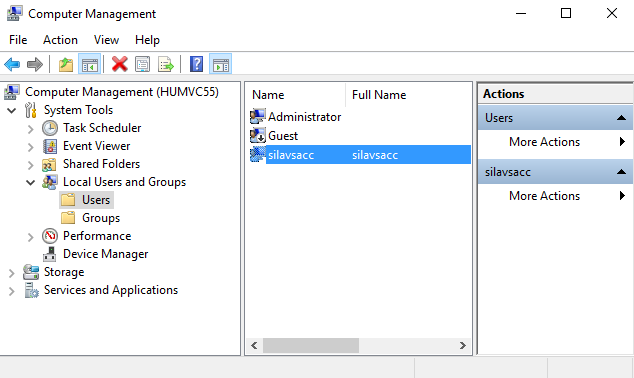
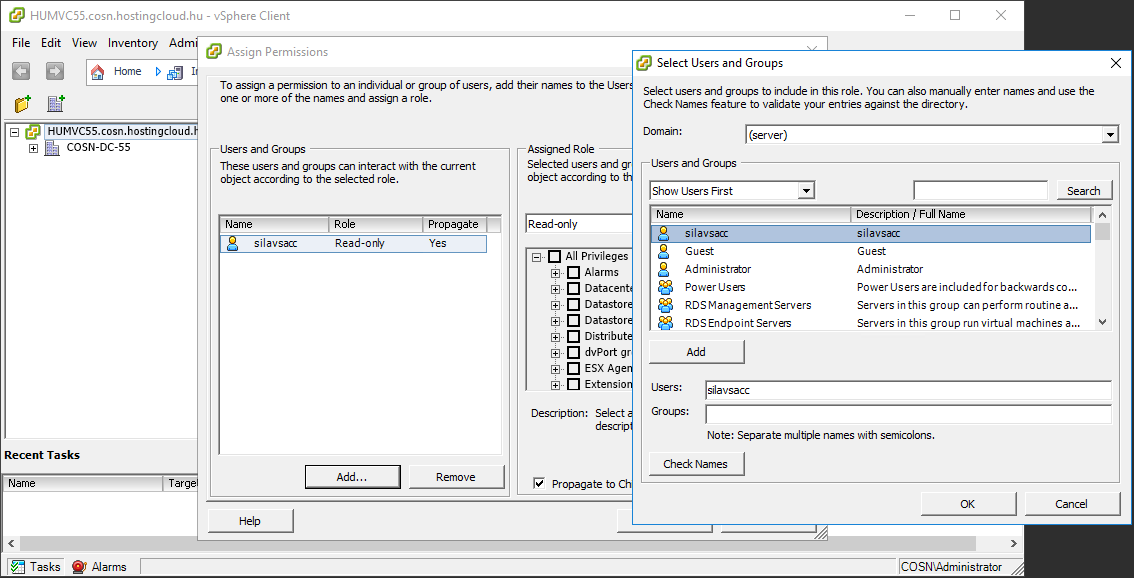
Also you can add all vSphere hosts, managed by vCenter. If your vCenter runs on a Windows Server, then go to Computer Management console of this server and create a local user with the same name as SILA vSphere Account. In my case it is silavsacc. Then connect to vCenter with vSphere client and assign this user ReadOnly rights:
Then run this script under SILA Service Account and specify SILA vSphere Account credentials when prompted (in my case - silavsacc):
$Credentials = Get-Credential
$vCenterFQDN=" FQDNOFVCENTER "
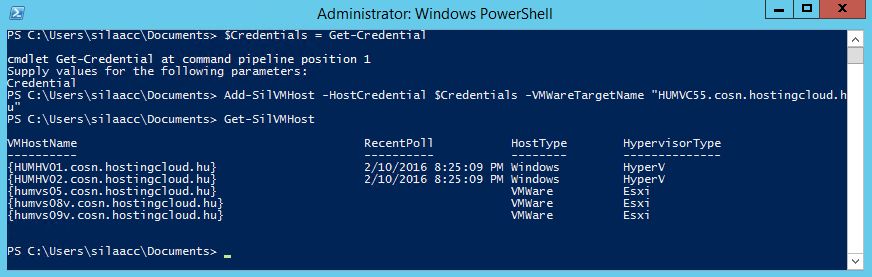
Add-SilVMHost -HostCredential $Credentials -VMWareTargetName $vCenterFQDN
This commands gets a list of all vSphere hosts, managed by the specified vCenter server. After that, SILA uses the specified SILA vSphere account to connect to every vSphere host directly, vCenter is not used any more. Check that all needed hosts were added with Get-SILVMHostcommand:
There can be a situation, when vSphere hosts are successfully added to the list, HypervisorType is "ESXi", but there are no successful polls during next several hours after adding. The most possible reason is that local SILA vSphere account is not created properly, of the account name and password that you used when you added hosts via vCenter was OK for vCenter, but it is not OK for vSphere hosts - different account name or password, for example.
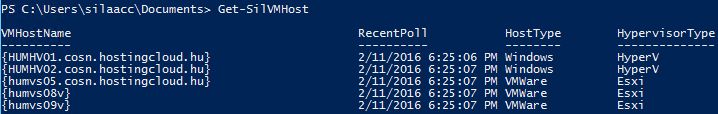
OK, when you've added all the hosts, check again after several hours - there must a timestamp of the last Recent Poll. If this field is not blank, then everything is OK:
Add KVM and Xen hosts
OK, now I will briefly describe how to add KVM and Xen hosts to SILA. First - you need to create local user account with appropriate rights on every Xen or KVM host. There are several ways to do that - from using root account (simple, but not recommended) to creating a Read-only user account with appropriate permission on KVMXen. SILA uses sshnet to communicate with Linux hosts.
To add a single KVM/Xen host, run this PowerShell script under SILA Service Account and specify credentials of a recently created local user:
$Credentials = Get-Credential
$HostFQDN = " FQDNOFTHEHOST " Add-SILVMHost -VMHostname $HostFQDN -hostcredential $Credentials
If you need, modify the script to get a list of all KVM/Xen hosts from a file and run Add-SILVMHost command for every host in the list. Then check that all the hosts are visible when you run Get-SILVMHost command and HypervisorType is "KVM" or "Xen".
OK, that's all for today. Try to add all the virtualization hosts that you have to SILA to get the most complete report, as you see - SILA is flexible and works with all popular virtualization platforms. In the next post I'll show how to configure Guest VM inventory using SIL.
This post is a part of a series about SPLA Reporting.
Part 1 - SPLA Reporting - Introduction
Part 2 - Installing SILA
Part 3 - Adding virtualization hosts to SILA (this post)
Part 4 - Configuring SIL
Part 5 - Creating and submitting inventory report
Comments
- Anonymous
February 17, 2016
The comment has been removed - Anonymous
February 17, 2016
Reporting of SPLA licenses usually was a challenge for big service providers. Some service providers collect the list of needed SPLA licenses manually every month, others use 3rd-party tools like Odin Service Automation to automate this task. But recently - Anonymous
February 17, 2016
The comment has been removed - Anonymous
February 17, 2016
The comment has been removed - Anonymous
February 22, 2017
Hi, I am trying to add my ESXi hosts to SILA, but they are added as "unknown". I checked the local ESXi account and the ReadOnly rights, and this is all OK. I also tried with ESXi root credentials, but with no luck unfortunately. With some help from our firewall guys we checked the network traffic between the SILA server and the ESXi servers, and we can see that SILA tries to SSH into the ESXi servers, is this correct ? If I try to SSH manually into the ESXi servers using a tool like PuTTY, I first have to accept the SSH Key (since the ESXi server is using a certificate generated by the VMware installer), before I can successfully start the SSH session. Could it be that SILA is facing the same issue ? How can I get SILA to accept the certificate / SSH key of my ESXi servers ? Thanks. - Anonymous
December 26, 2018
will this tool be upgraded to support vSphere 6?