Microsoft Network Access Protection (Simple setup)
Protecting the Network from consumer devices, Microsoft Network Access Protection (NAP) simple setup.
This is a blog post from the work that Kevin Saye completed...
Summary:
With the proliferation of consumer and non-enterprise devices on the corporate network, security and health of these devices is top of mind for security officers.
While there are many vendors out there who offer agent and appliance solutions, Microsoft has provided Network Access Protection (aka NAP) since Windows Server 2008. With NAP, you can provide device level health for devices using the proven capability of: 802.1x (port level authentication), VLAN (network level segmentation) and client posture assessment for client devices.
This document outlines how to setup NAP for enterprise and consumer devices, allowing corporate and non-corporate access secure access.
Overview of Solution:
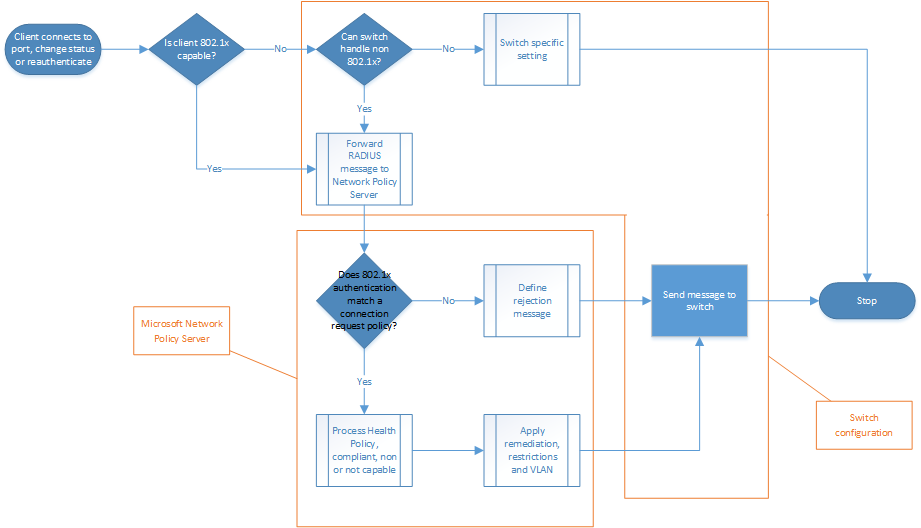
One of the most secure implementations of network protection is via 802.1x, which is a capability of most if not all enterprise level network gear (both wired and wireless). NAP can use 802.1x as an enforcement point, providing end users ease of access and policy compliance with both enterprise and consumer devices. This is where policy meets enforcement, and the end users just plug in a device (or connect via wireless) and magically it gets to the correct network.
For my demonstration, I used HP Procurve switches with the latest firmware. With this firmware, the commands changed just a bit from Jeff’s 2008 blog post here (https://blogs.technet.com/b/nap/archive/2008/06/19/nap-802-1x-configuration-walkthrough.aspx).
For this solution, there are 3 types of devices: enterprise managed, 802.1x capable and other (insert your favorite device here).
For enterprise managed (joined to the domain), they have the correct configuration, client certificate and policy compliance that enables it to be on the corporate network. For the other 2, they are “restricted” to the guest network protecting sensitive data / systems from insecure systems.
To outline the solution, consider the diagram below, showing the logical flow and dependencies of a NAP solution using 802.1x.
Setting it all Up:
HP Switch:
The following settings are for an HP Procurve switch with a F.05.77 firmware.
vlan 1
; this VLAN is not used
name "DEFAULT_VLAN"
ip address dhcp-bootp
exit
vlan 243
; this VLAN is my internet only VLAN
name "243"
; Port 1 is my uplink port
tagged 1
exit
vlan 184
; this VLAN is my corporate VLAN
name "184"
; Port 1 is my uplink port, port 2 is my non NAP port.
tagged 1
ip address 10.7.184.250 255.255.255.0
exit
; This enables EAP, sets the NPS server and the shared secret, sets ports 2-24 to use 802.1x and activates it
aaa authentication port-access eap-radius
radius-server host 10.7.184.200 key secret
aaa port-access authenticator 2-24
aaa port-access authenticator 2-24 unauth-vid 243
aaa port-access authenticator active
This configuration uses port 1 as my uplinked, which is VLAN tagged for both VLAN 184 (corporate VLAN) and VLAN 243 (internet / Guest VLAN).
I am also using EAP authentication, as this is the most secure this switch provides.
The IP address of my NPS is 10.7.184.200 and the shared secret is “secret”. The HP switch does not forward request for non 802.1x capable devices, but instead it uses the “unauth-vid” setting to define VLAN 243 for them.
I am also using EAP authentication, as this is the most secure this switch provides.
NPS Server:
For the NPS server, I followed these summarized steps.
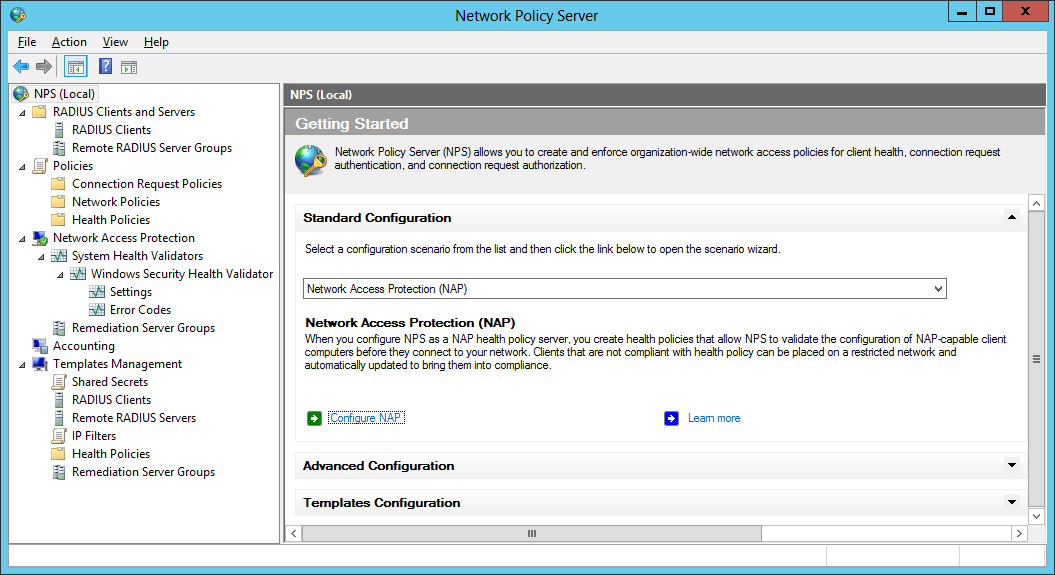
Step 1: After installing the Network Policy Server, select NPS (Local) and click “Configure NAP”.
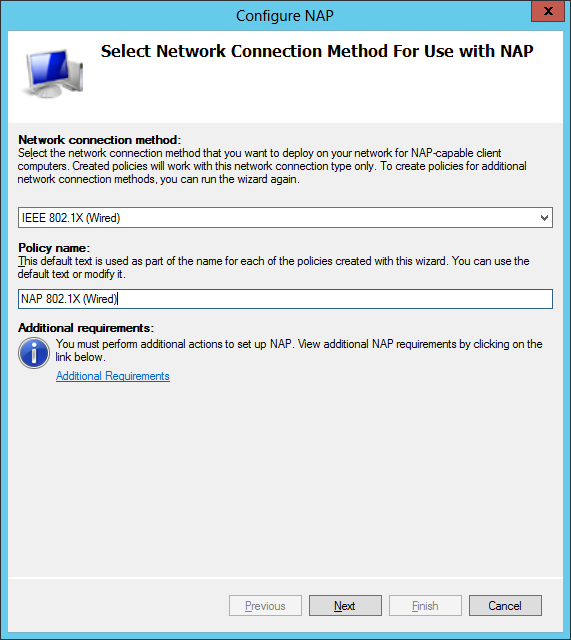
Step 2: Select the connection method to be 802.1x wired.
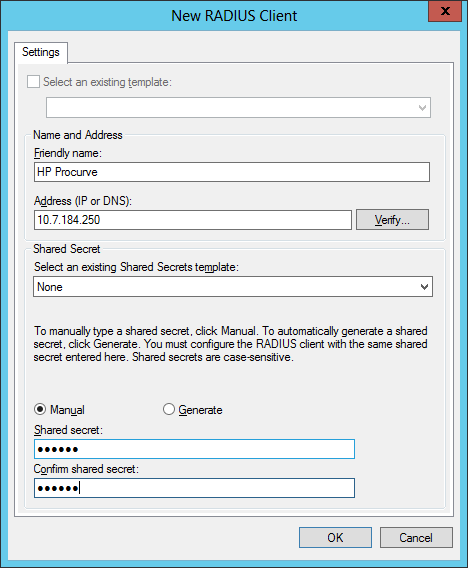
Step 3: Add one or more of your switches (HP in my case).
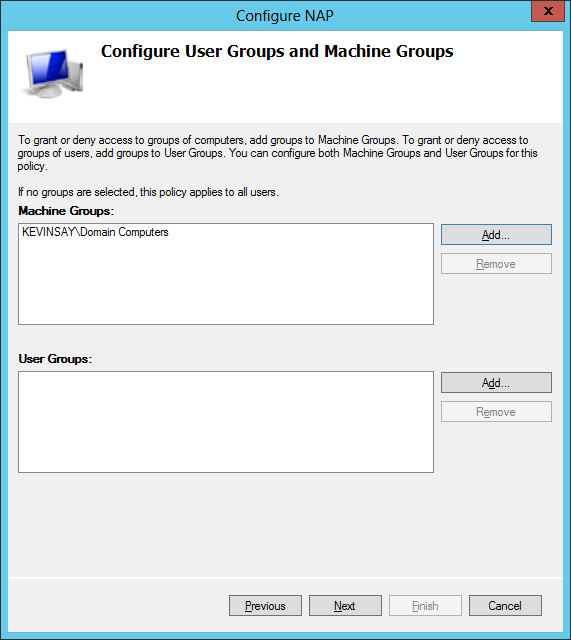
Step 4: Determine what users or machine groups you want to allow connections to the corporate VLAN.
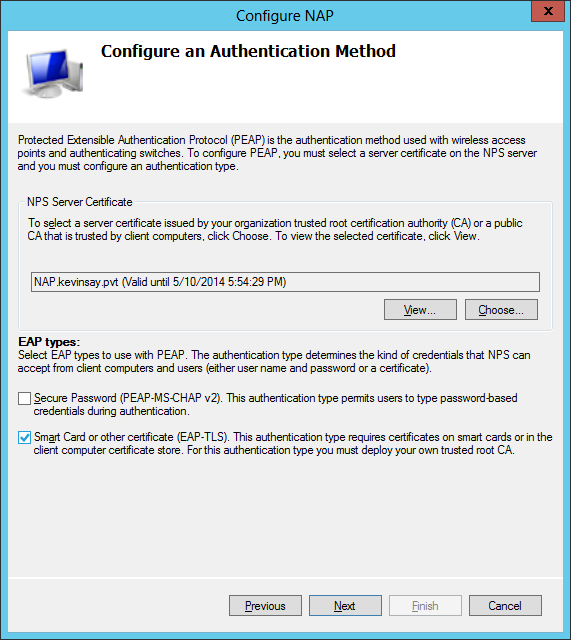
Step 5: Select the NAP Server certificate (if allowing non domain machine, it should be a public PKI cert), and the EAP type. For my environment, I wanted machine certs, so I used EAP-TLS. You could have had the users type in a password (PEAP), but that is not the experience I wanted.
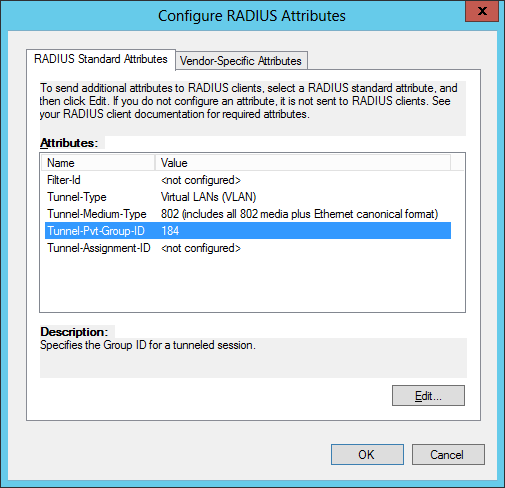
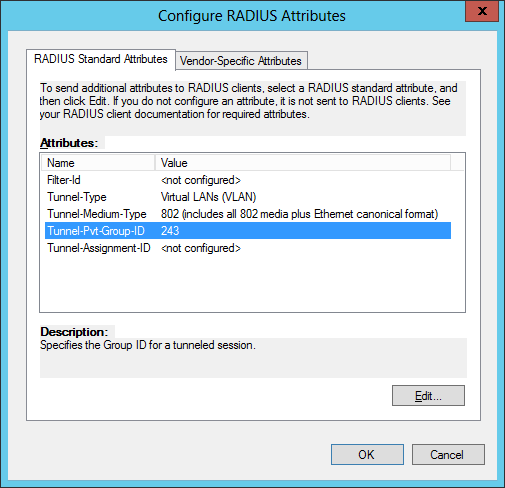
Step 6: Define the VLAN attributes for the corporate VLAN (aka the compliant network / full access network)
Step 7: Define the VLAN settings for the guest VLAN (aka the non-compliant / restricted network)
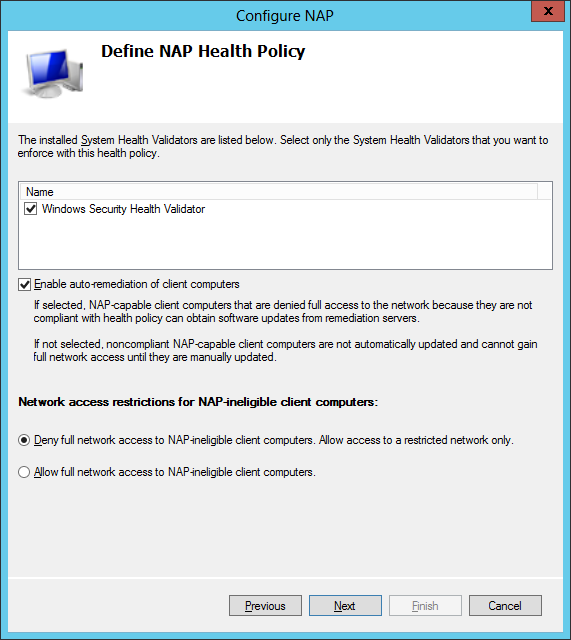
Step 8: Define which validators you will use, if remediation is enabled and what to do with non-NAP computers.
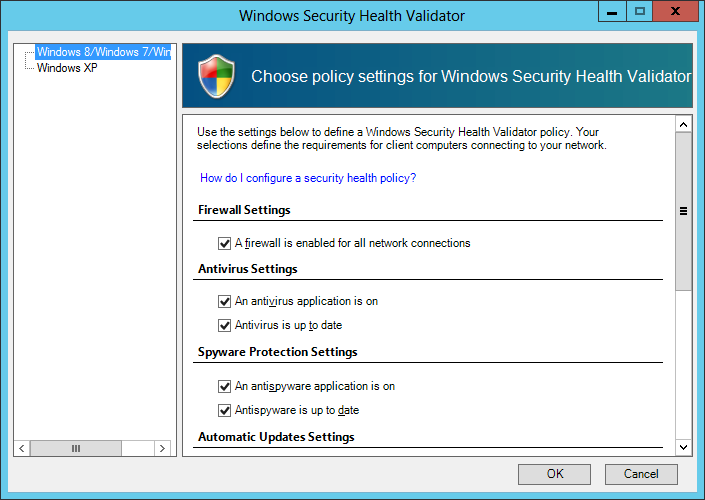
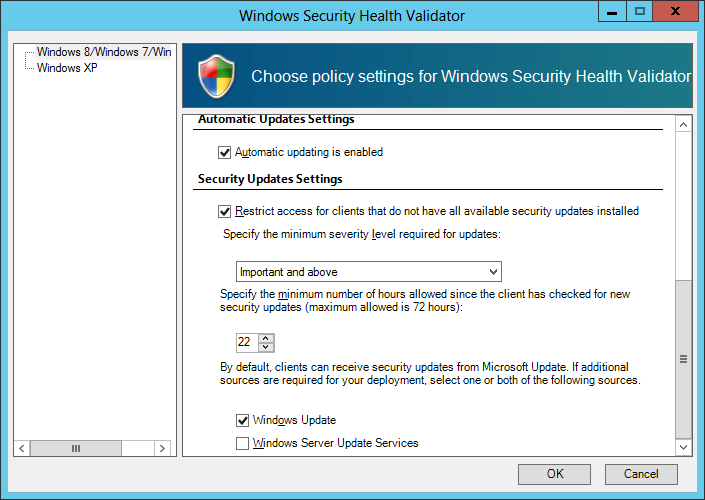
Step 9: Lastly, I setup my Windows Security Health Validator to match my policy.
Client Device – Enterprise Managed:
On enterprise managed devices, you need to set at least 4 settings. These can all be set via GPO, but I wanted to show the exact settings here so you can fully understand what has to be set.
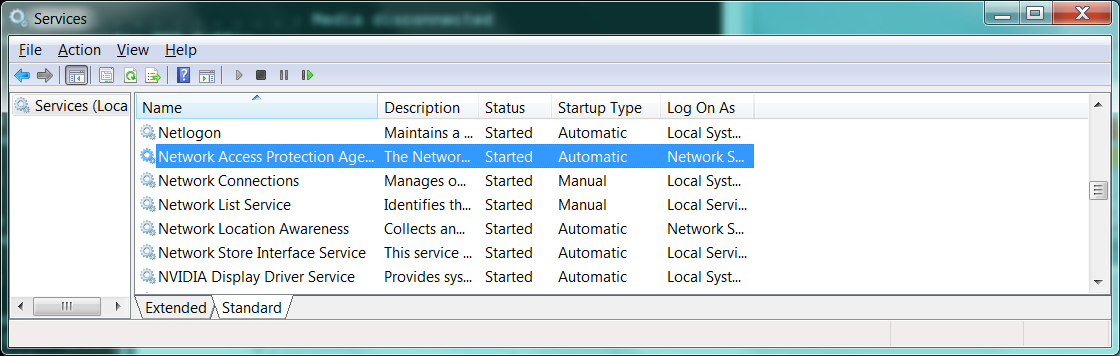
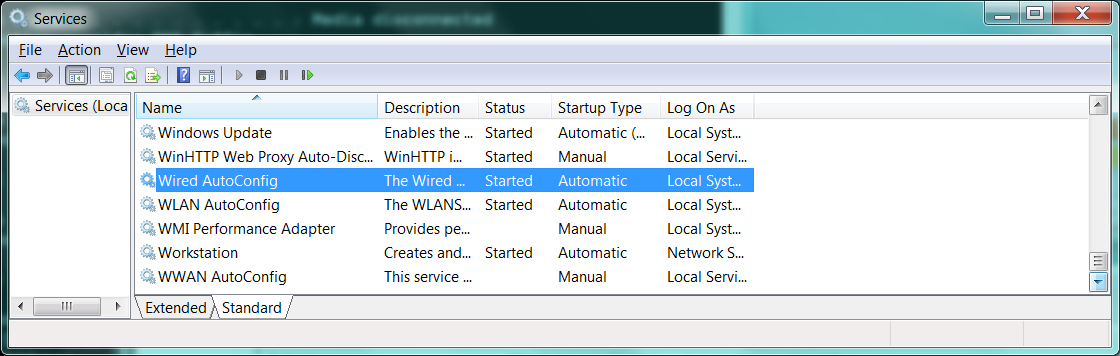
Step 1: Set both the “Network Access Protection” and the “Wired AutoConfig” service as automatic and start them.
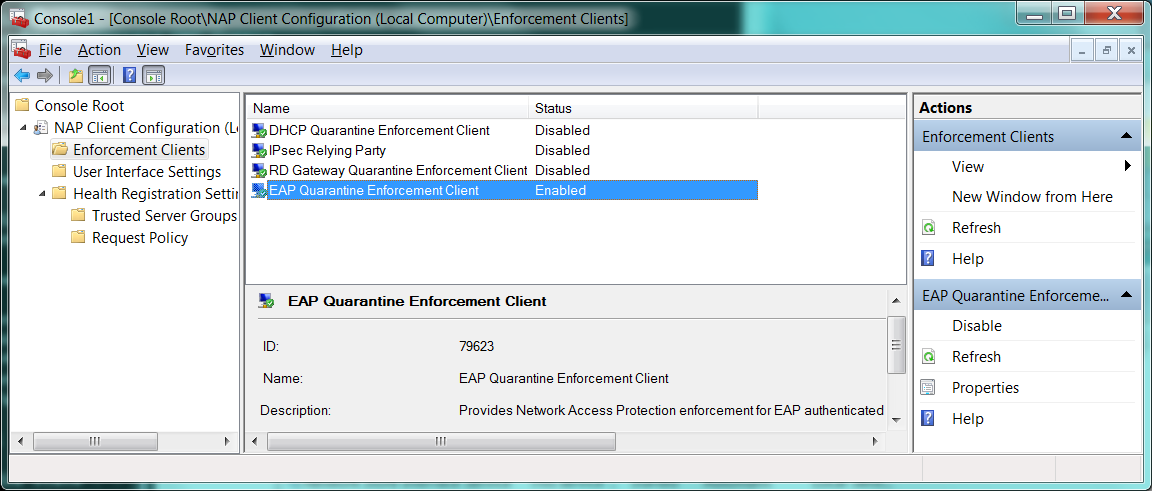
Step 2: Open up an MMC, add the “NAP Client Configuration” and enable the EAP Quarantine Enforcement Client.
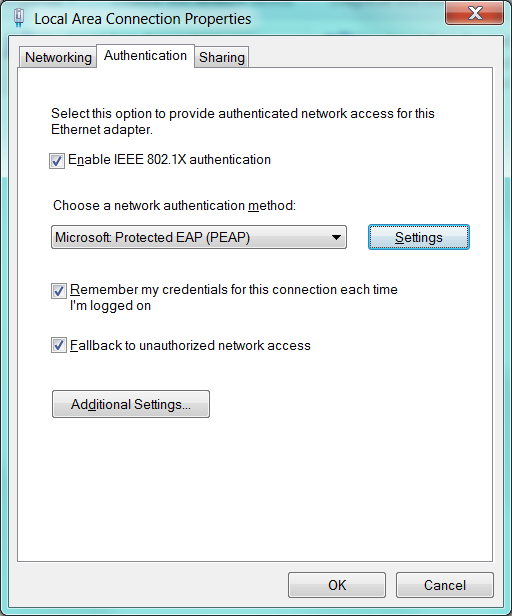
Step 3: Once the “Wired AutoConfig” service is started, in network connections right click on the Ethernet interface and select Authentication. Enable 802.1X and select PEAP.
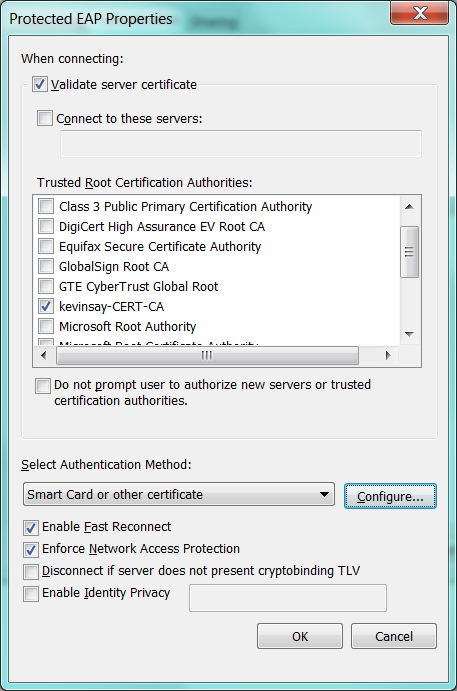
Step 4: Click Settings of EAP, select “Validate server cert” and select your CA. Next set the Authentication method to “other certificate”.
Client Device – 802.1x capable not Enterprise Managed:
An 802.1x client, not completely configured, including not having a valid certificate, it automatically placed on the guest network.
Client Device – non 802.1x capable:
Non 802.1x capable devices are placed on the guest network.
Seeing it in Action:
Enterprise Managed:
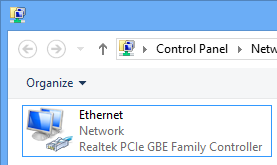
Enterprise Managed Devices just connect as expected and without any noticeable change.
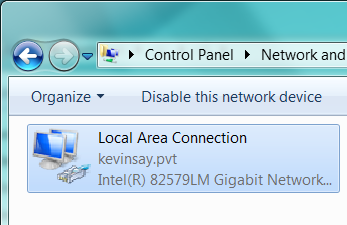
The network card looks normal (as a point of reference)
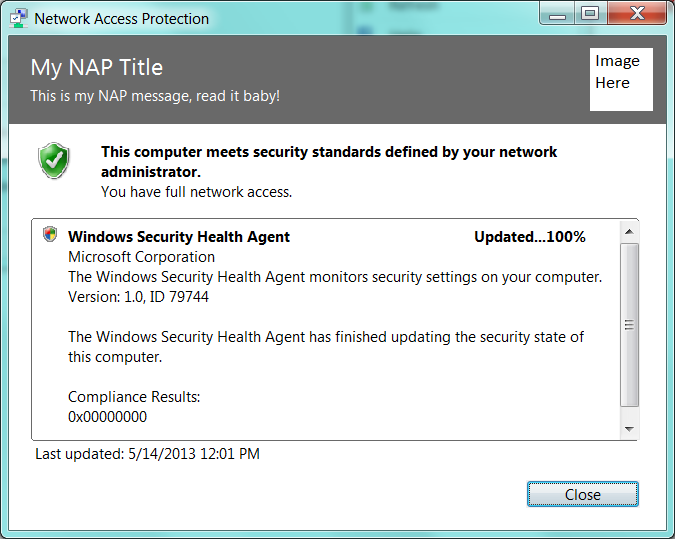
And if you run napstat.exe, you see the status of the machine. Notice how I changed the title, description and the image, you can too!
Other – 802.1x not configured:
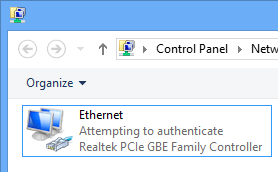
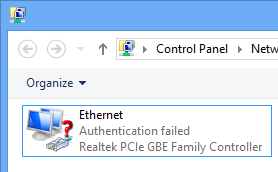
On devices with 802.1x but misconfigured you will see the network card attempt to authenticate, but eventually fail. In the failed state, the will be on the guest network. If you change the NPS authentication from EAP certificate only, to something else, the use can get an authentication prompt and attempt to authenticate as the user. Not the experience I wanted, from a usability perspective.
Other – non 802.1x:
On devices without 802.1x, they will remain in a failed state, but the UI does not show this status. This device will be on the guest network.
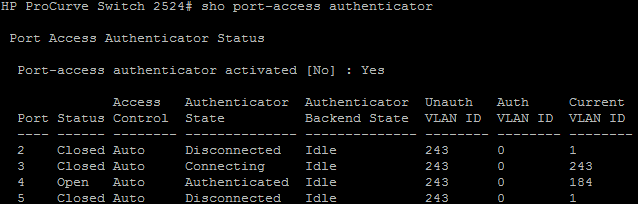
HP Switch:
From the switch console, you will see that I have a device on port 4 that is nap capable and is on the VLAN 184. The device on port 3 is either not nap capable or not compliant and as such is on VLAN 243.
Auditing the Events:
You will see one of two type of audit logs, by default.
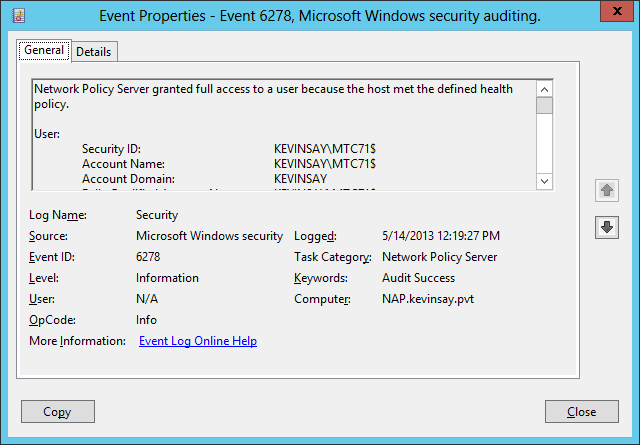
Success:
In the security log on the NAP server, you will see event 6278 with a success code as shown below:
Actual content:
Network Policy Server granted full access to a user because the host met the defined health policy.
User:
Security ID: KEVINSAY\MTC71$
Account Name: KEVINSAY\MTC71$
Account Domain: KEVINSAY
Fully Qualified Account Name: KEVINSAY\MTC71$
Client Machine:
Security ID: NULL SID
Account Name: mtc71.kevinsay.pvt
Fully Qualified Account Name: KEVINSAY\MTC71$
OS-Version: 6.1.7601 1.0 x64 Workstation
Called Station Identifier: 00-30-c1-a9-d7-a4
Calling Station Identifier: 88-51-fb-c9-36-fa
NAS:
NAS IPv4 Address: 10.7.184.250
NAS IPv6 Address: -
NAS Identifier: HP ProCurve Switch 2524
NAS Port-Type: Ethernet
NAS Port: 4
RADIUS Client:
Client Friendly Name: HP Procurve
Client IP Address: 10.7.184.250
Authentication Details:
Connection Request Policy Name: NAP 802.1X (Wired)
Network Policy Name: NAP 802.1X (Wired) Compliant
Authentication Provider: Windows
Authentication Server: NAP.kevinsay.pvt
Authentication Type: PEAP
EAP Type: Microsoft: Smart Card or other certificate
Account Session Identifier: -
Quarantine Information:
Result: Full Access
Extended-Result: -
Session Identifier: {DDA6D86C-E54C-4913-9E74-4E00B95F54FA} - 2013-05-14 17:19:27.053Z
Help URL: -
System Health Validator Result(s):
Windows Security Health Validator
0
Compliant
No Data
None[]
(0x0 - )
(0x0 - )
(0x0 - )
(0x0 - )
(0x0 - )
(0x0 - )
(0x0 - )
(0x0 - )
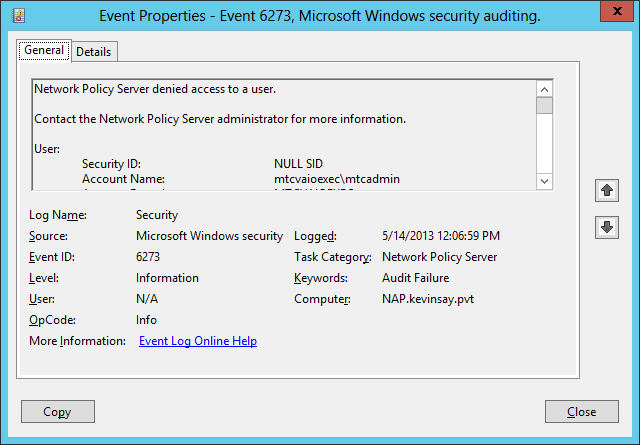
Failure:
In the security log on the NAP server, you will see event 6273 with a failure code as shown below:
Network Policy Server denied access to a user.
Contact the Network Policy Server administrator for more information.
User:
Security ID: NULL SID
Account Name: mtcvaioexec\mtcadmin
Account Domain: MTCVAIOEXEC
Fully Qualified Account Name: MTCVAIOEXEC\mtcadmin
Client Machine:
Security ID: NULL SID
Account Name: -
Fully Qualified Account Name: -
OS-Version: -
Called Station Identifier: 00-30-c1-a9-d7-b0
Calling Station Identifier: 54-42-49-97-42-8d
NAS:
NAS IPv4 Address: 10.7.184.250
NAS IPv6 Address: -
NAS Identifier: HP ProCurve Switch 2524
NAS Port-Type: Ethernet
NAS Port: 3
RADIUS Client:
Client Friendly Name: HP Procurve
Client IP Address: 10.7.184.250
Authentication Details:
Connection Request Policy Name: NAP 802.1X (Wired)
Network Policy Name: -
Authentication Provider: Windows
Authentication Server: NAP.kevinsay.pvt
Authentication Type: PEAP
EAP Type: Microsoft: Smart Card or other certificate
Account Session Identifier: -
Logging Results: Accounting information was written to the local log file.
Reason Code: 7
Reason: The specified domain does not exist.