Manage system extensions using the manual methods of deployment
This article describes the procedures involved when deploying Microsoft Defender for Endpoint manually.
Manual deployment
System Extensions
You might see the prompt that's shown in the following screenshot:
Select OK. You might get a second prompt as shown in the following screenshot:
From this second-prompt screen, select OK. You'll receive a notification message that reads Installation succeeded, as shown in the following screenshot:
On the screen displaying the Installation succeeded notification message, select OK. You'll return to the following screen:
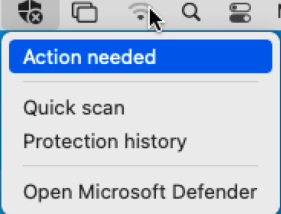
From the menu bar, click the x symbol on the shield. You'll get the options shown in the following screenshot:
Select Action needed. The following screen appears:
Click Fix on the top-right corner of this screen. You'll get a prompt, as shown in the following screenshot:
Enter your password and select OK.
-
The System Preferences screen appears.
Click Security & Privacy. The Security & Privacy screen appears.
Select Click the lock to make changes. You'll get a prompt as shown in the following screenshot:
Enter your password and click Unlock. The following screen appears:
Select Details, next to Some software system requires your attention before it can be used.
Check both the Microsoft Defender checkboxes, and select OK. You'll get two pop-up screens, as shown in the following screenshot:
On the "Microsoft Defender" Would like to Filter Network Content pop-up screen, click Allow.
On the Microsoft Defender wants to make changes pop-up screen, enter your password and select OK.
If you run systemextensionsctl list, the following screen appears:
Accessibility
On the Security & Privacy screen, select the Privacy tab.
Select Accessibility from the left navigation pane, and click +.
From the resultant screen, select Applications from the Favorites pane in the left-side of the screen; select Microsoft Defender; and then select Open at the bottom-right of the screen.
From the resultant screen, check the Microsoft Defender checkbox.
Full Disk Access
On the Security & Privacy screen, select the Privacy tab.
Select Full Disk Access from the left navigation pane, and then click the Lock icon.
Confirm that the Microsoft Defender extension has full disk access; if not, check the Microsoft Defender checkbox.
Notifications
From the System Preferences home screen, select Notifications.
The Notifications screen appears.
Select Microsoft Defender from the left navigation pane.
Enable the Allow Notifications option; select Alerts, and retain the default settings as is.
What a healthy system looks like
mdatp health output
Check the system extensions
In terminal, run the following command to check the system extensions:
systemextensionsctl list
The execution of this command is shown in the following screenshot: