Vulnerabilities in my organization
The Weaknesses page in Microsoft Defender Vulnerability Management lists known Common Vulnerabilities and Exposures (CVE) by their CVE ID.
CVE IDs are unique IDs assigned to publicly disclosed cybersecurity vulnerabilities that affect software, hardware and firmware. They provide organizations with a standard way to identify and track vulnerabilities, and helps them understand, prioritize, and address these vulnerabilities in their organization. CVEs are tracked in a public registry accessed from https://www.cve.org/.
Defender Vulnerability Management uses endpoint sensors to scan and detect for these and other vulnerabilities in an organization.
Applies to:
- Microsoft Defender Vulnerability Management
- Microsoft Defender for Endpoint Plan 2
- Microsoft Defender XDR
- Microsoft Defender for Servers Plan 1 & 2
Important
Defender Vulnerability Management can help identify Log4j vulnerabilities in applications and components. Learn more.
Tip
Did you know you can try all the features in Microsoft Defender Vulnerability Management for free? Find out how to sign up for a free trial.
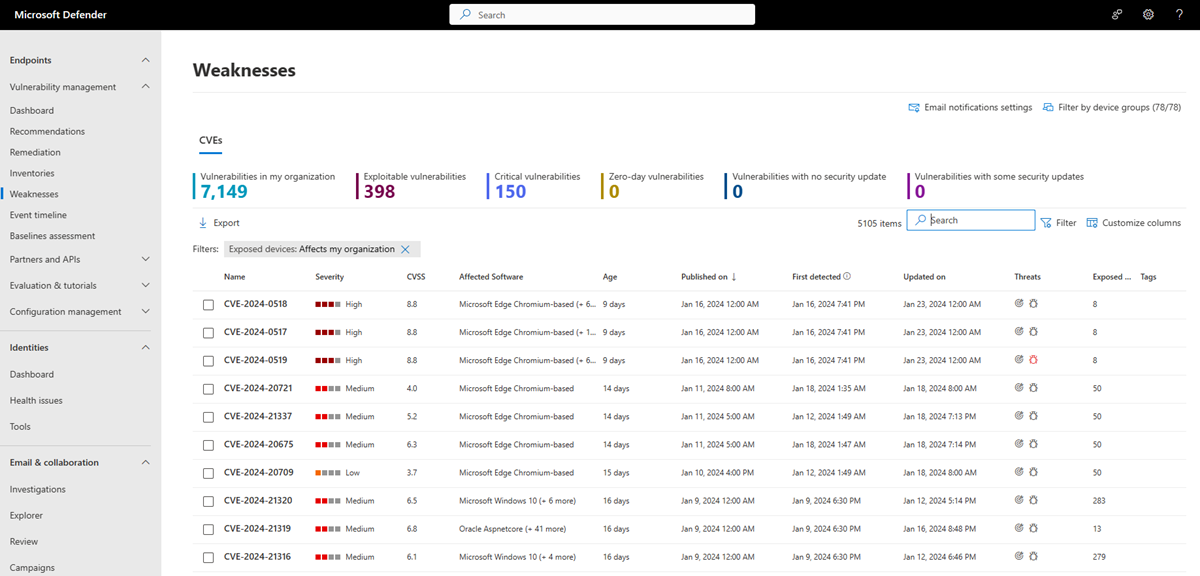
Weaknesses overview page
To access the Weaknesses page, select Weaknesses from the Vulnerability management navigation menu in the Microsoft Defender portal
The Weaknesses page opens with a list of the CVEs your devices are exposed to. You can view the severity, Common Vulnerability Scoring System (CVSS) rating, corresponding breach and threat insights, and more.
Note
If there is no official CVE-ID assigned to a vulnerability, the vulnerability name is assigned by Microsoft Defender Vulnerability Management and will be the format TVM-2020-002.
Note
The maximum number of records you can export from the weaknesses page to a CSV file is 8,000 and the export must not exceed 64KB. If you receive a message stating the results are too large to export, refine your query to include less records.
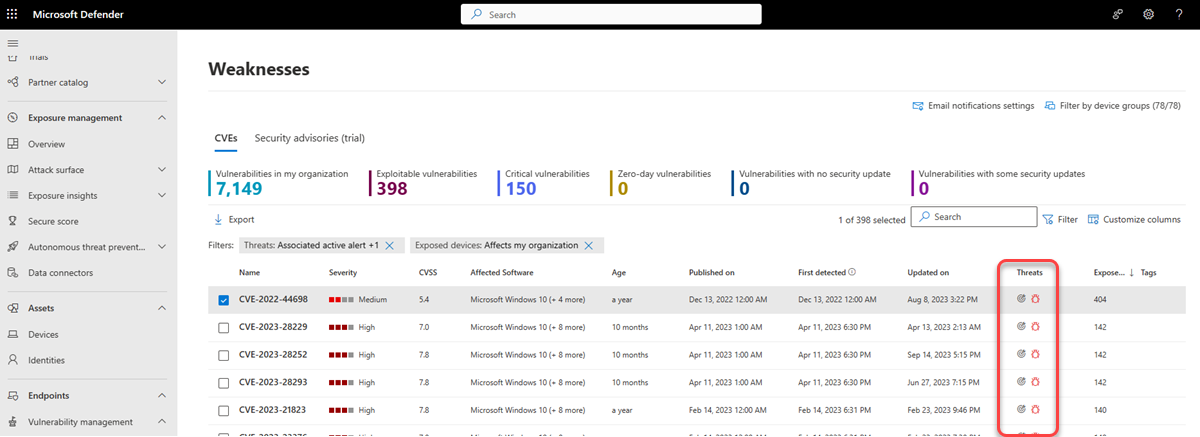
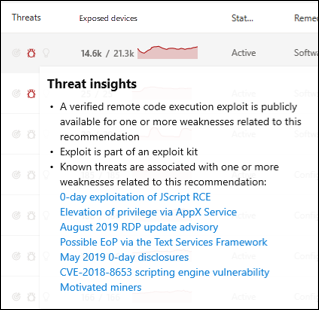
Breach and threat insights
It's important to prioritize recommendations that are associated with ongoing threats. You can use the information available in the Threats column to help you prioritize vulnerabilities. To see vulnerabilities with ongoing threats, filter the Threats column by:
- Associated active alert
- Exploit is available
- Exploit is Verified
- This exploit is part of an exploit kit
The threat insights icon ![]() is highlighted in the Threats column if there are associated exploits in a vulnerability.
is highlighted in the Threats column if there are associated exploits in a vulnerability.
Hovering over the icon shows whether the threat is a part of an exploit kit or connected to specific advanced persistent campaigns or activity groups. When available, there's a link to a Threat Analytics report with zero-day exploitation news, disclosures, or related security advisories.
The breach insights icon is highlighted if there's a vulnerability found in your organization. ![]() .
.
The Exposed Devices column shows how many devices are currently exposed to a vulnerability. If the column shows 0, that means you aren't at risk.
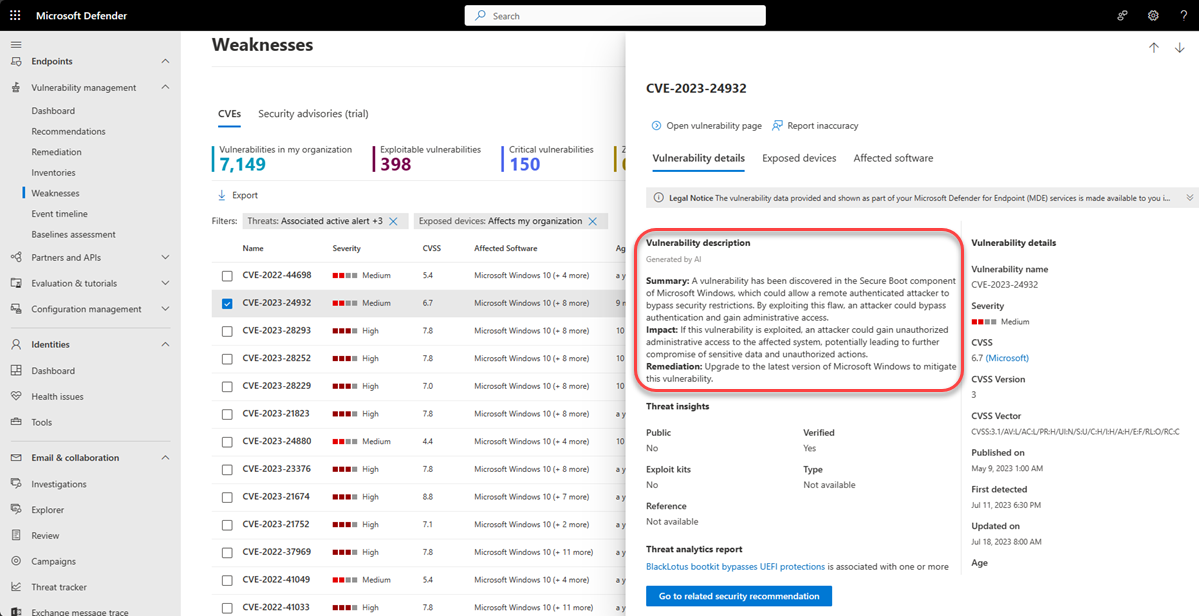
Gain vulnerability insights
If you select a CVE from the weaknesses page, a flyout panel opens with more information such as the vulnerability description, details, and threat insights. The AI generated vulnerability description provides detailed information on the vulnerability, its effect, recommended remediation steps, and any additional information, if available.
For each CVE, you can see a list of the exposed devices and the affected software.
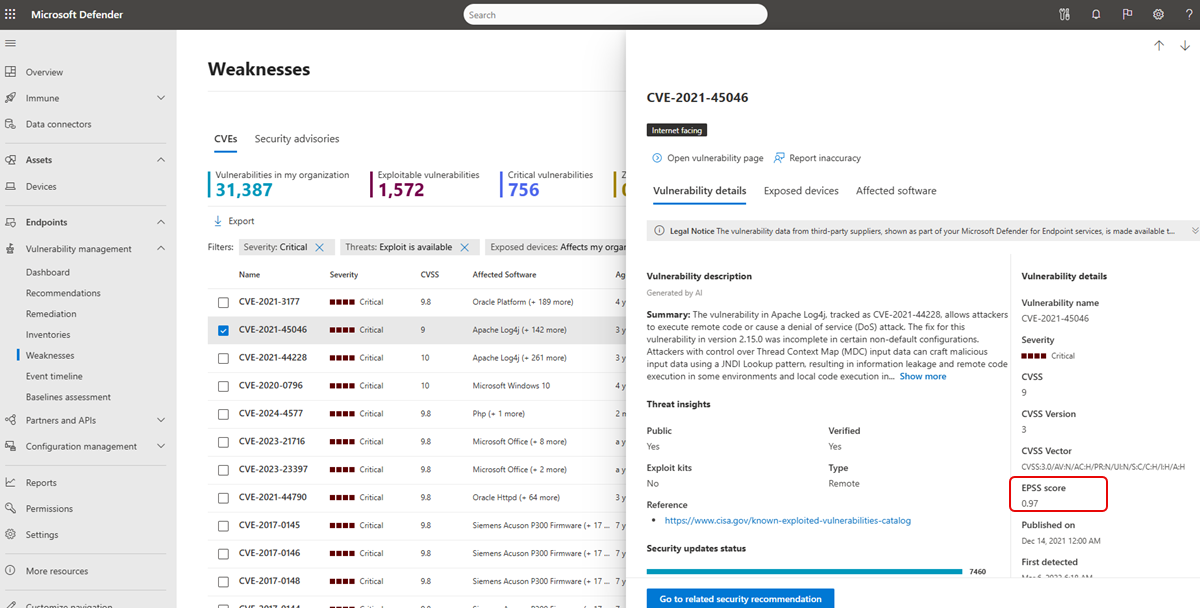
Exploit Prediction Scoring System (EPSS)
The Exploit Prediction Scoring System (EPSS) generates a data-driven score for the probability of a known software vulnerability being exploited in the wild. EPSS uses current threat information from the CVE and real-world exploit data. For each CVE, the EPSS model produces a probability score between 0 and 1 (0% and 100%). The higher the score, the greater the probability that a vulnerability will be exploited. Learn more about EPSS.
EPSS is designed to help enrich your knowledge of weaknesses and their exploit probability, and enable you to prioritize accordingly.
To see the EPSS score select a CVE from the Weaknesses page in the Microsoft Defender portal:
When the EPSS is greater than 0.9, the Threats column tooltip is updated with the value to convey the urgency of mitigation:
Note
Note that if the EPSS score is smaller than 0.001, it’s considered to be 0.
You can use the Vulnerability API to see the EPSS score.
Related security recommendations
Use security recommendations to remediate the vulnerabilities in exposed devices and to reduce the risk to your assets and organization. When a security recommendation is available, you can select Go to the related security recommendation for details on how to remediate the vulnerability.
Recommendations for a CVE are often to remediate the vulnerability through a security update for the related software. However, Some CVEs won't have a security update available. This might apply to all the related software for a CVE or just a subset, for example, a software vendor might decide not to fix the issue on a particular vulnerable version.
When a security update is only available for some of the related software, the CVE will have the tag 'Some updates available' under the CVE name. Once there is at least one update available, you have the option to go to the related security recommendation.
If there's no security update available, the CVE will have the tag 'No security update' under the CVE name. There will be no option to go to the related security recommendation as software that doesn't have a security update available is excluded from the Security recommendations page.
Note
Security recommendations only include devices and software packages that have security updates available.
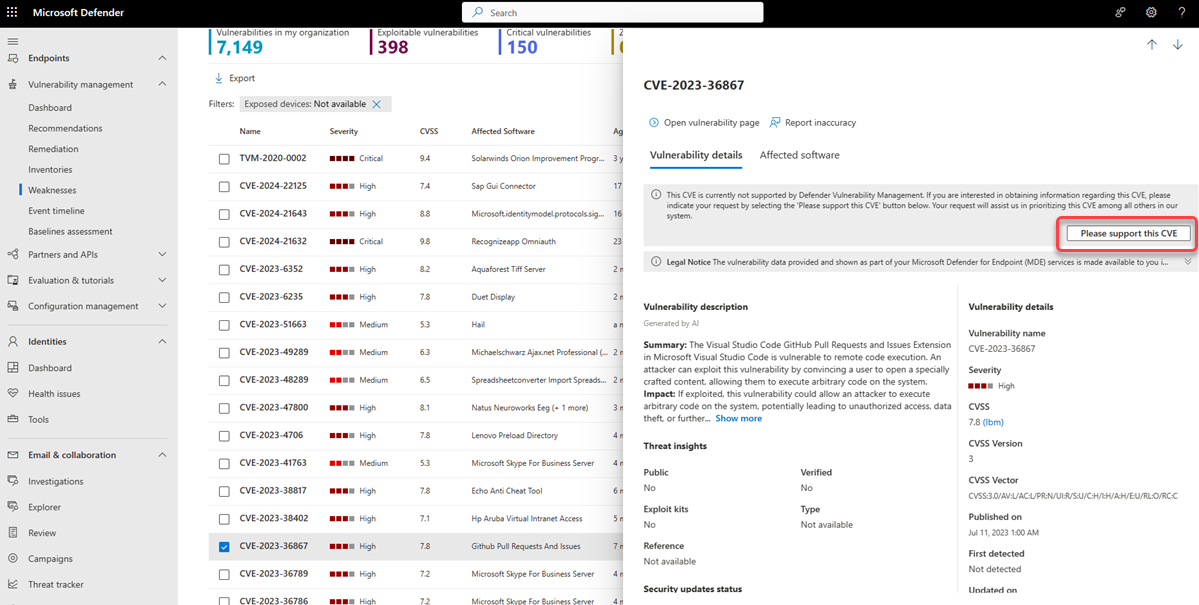
Request CVE support
A CVE for software that isn't currently supported by vulnerability management still appears in the Weaknesses page. Because the software is not supported, only limited data is available. Exposed device information won't be available for CVEs with unsupported software.
To view a list of unsupported software, filter the weaknesses page by the "Not available" option in the "Exposed devices" section.
You can request for support to be added to Defender Vulnerability Management for a particular CVE. To request support:
Select the CVE from the Weaknesses page in the Microsoft Defender portal
Select Please support this CVE from the Vulnerability details tab
The request is sent to Microsoft and will assist us in prioritizing this CVE among others in our system.
Note
Request CVE support functionality is not available for GCC, GCC High and DoD customers.
View Common Vulnerabilities and Exposures (CVE) entries in other places
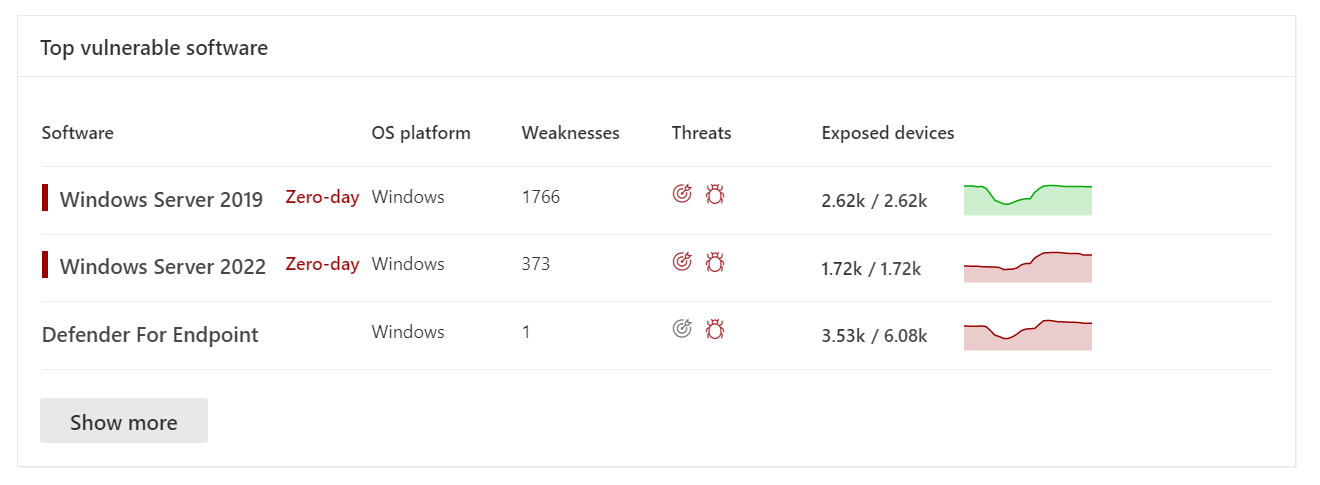
Top vulnerable software in the dashboard
Go to the Defender Vulnerability Management dashboard and scroll down to the Top vulnerable software widget. You'll see the number of vulnerabilities found in each software, along with threat information and a high-level view of device exposure over time.
Select the software you want to investigate.
Select the Discovered vulnerabilities tab.
Select the vulnerability that you want to investigate to open up a flyout panel with the CVE details.
Discover vulnerabilities in the device page
View related weaknesses information in the device page.
- Select Devices from the Assets navigation menu in the Microsoft Defender portal.
- In the Device inventory page, select the device name that you want to investigate.
- Select Open device page and select Discovered vulnerabilities from the device page.
- Select the vulnerability that you want to investigate to open up a flyout panel with the CVE details.
CVE Detection logic
Similar to the software evidence, we show the detection logic we applied on a device in order to state that it's vulnerable.
To see the detection logic:
Select a device from the Device inventory page.
Select Open device page and select Discovered vulnerabilities from the device page.
Select the vulnerability you want to investigate.
A flyout opens and the Detection logic section shows the detection logic and source.
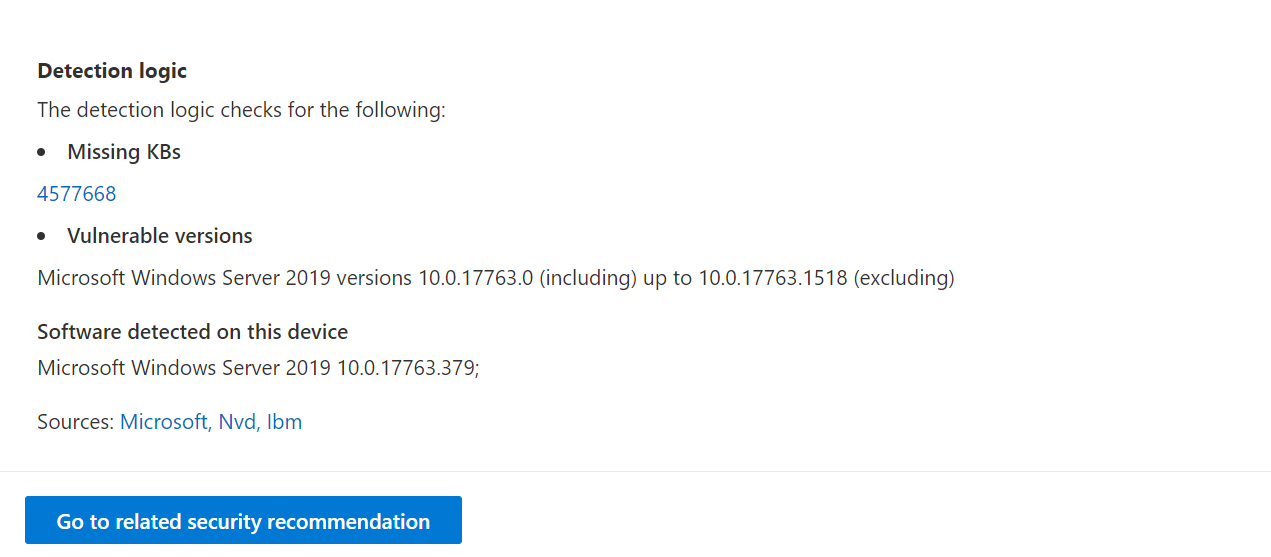
The "OS Feature" category is also shown in relevant scenarios. This is when a CVE would affect devices that run a vulnerable OS if a specific OS component is enabled. For example, if Windows Server 2019 or Windows Server 2022 has vulnerability in its DNS component we only attach this CVE to the Windows Server 2019 and Windows Server 2022 devices with the DNS capability enabled in their OS.
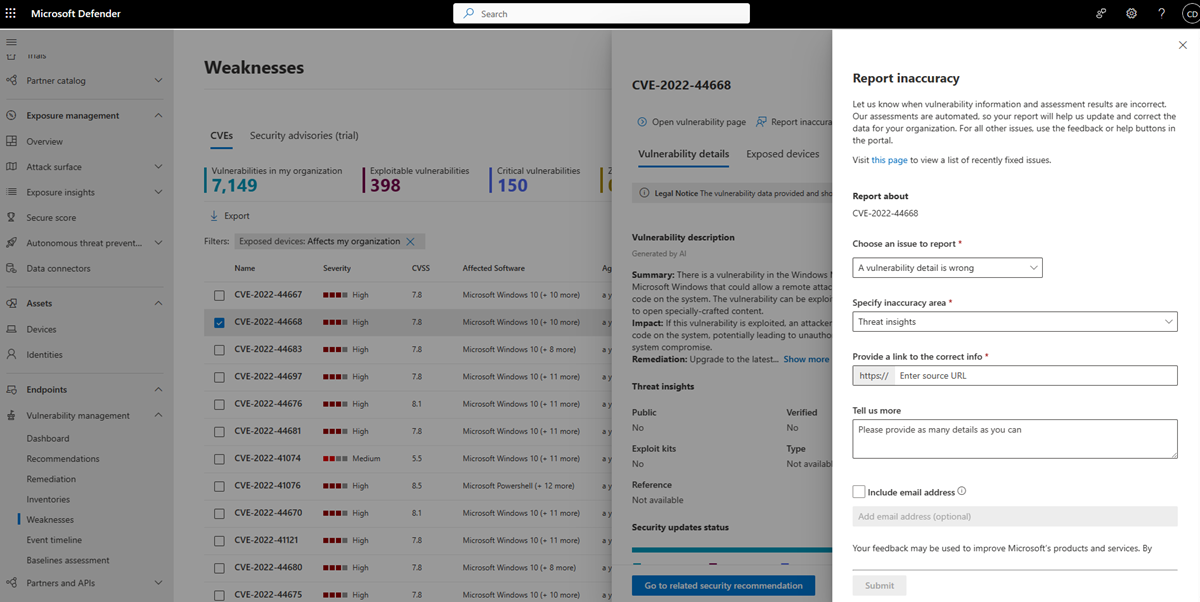
Report inaccuracy
Report a false positive when you see any vague, inaccurate, or incomplete information. You can also report on security recommendations that are already been remediated.
Open the CVE on the Weaknesses page.
Select Report inaccuracy.
From the flyout pane, choose an issue to report.
Fill in the requested details about the inaccuracy. This varies depending on the issue you're reporting.
Select Submit. Your feedback is immediately sent to the Microsoft Defender Vulnerability Management experts.