Review remediation actions following an automated investigation
Applies to:
Remediation actions
When an automated investigation runs, a verdict is generated for each piece of evidence investigated. Verdicts can be Malicious, Suspicious, or No threats found.
Depending on
- the type of threat,
- the resulting verdict, and
- how your organization's device groups are configured,
remediation actions can occur automatically or only upon approval by your organization's security operations team.
Note
Device group creation is supported in Defender for Endpoint Plan 1 and Plan 2.
Here are a few examples:
Example 1: Fabrikam's device groups are set to Full - remediate threats automatically (the recommended setting). In this case, remediation actions are taken automatically for artifacts that are considered to be malicious following an automated investigation (see Review completed actions).
Example 2: Contoso's devices are included in a device group that is set for Semi - require approval for any remediation. In this case, Contoso's security operations team must review and approve all remediation actions following an automated investigation (see Review pending actions).
Example 3: Tailspin Toys has their device groups set to No automated response (not recommended). In this case, automated investigations do not occur. No remediation actions are taken or pending, and no actions are logged in the Action center for their devices (see Manage device groups).
Whether taken automatically or upon approval, an automated investigation and remediation can result in one or more of the remediation actions:
- Quarantine a file
- Remove a registry key
- Kill a process
- Stop a service
- Disable a driver
- Remove a scheduled task
Review pending actions
Go to the Microsoft Defender portal and sign in.
In the navigation pane, choose Action center.
Review the items on the Pending tab.
Select an action to open its flyout pane.
In the flyout pane, review the information, and then take one of the following steps:
- Select Open investigation page to view more details about the investigation.
- Select Approve to initiate a pending action.
- Select Reject to prevent a pending action from being taken.
- Select Go hunt to go into Advanced hunting.
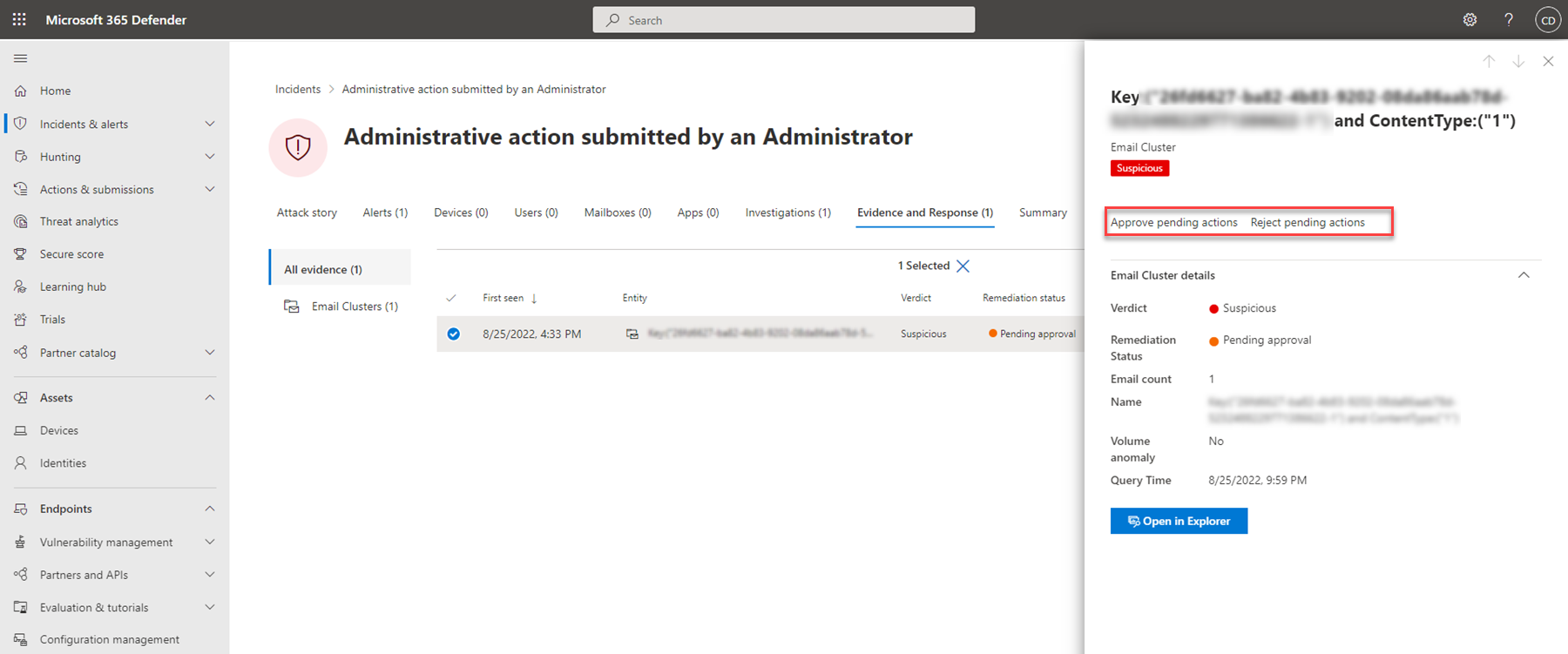
Approve or reject remediation actions
For incidents with a remediation status of Pending approval, you can also approve or reject a remediation action from within the incident.
- In the navigation pane, go to Incidents & alerts > Incidents.
- Filter on Pending action for the Automated investigation state (optional).
- Select an incident name to open its summary page.
- Select the Evidence and Response tab.
- Select an item in the list to open its flyout pane.
- Review the information, and then take one of the following steps:
- Select the Approve pending action option to initiate a pending action.
- Select the Reject pending action option to prevent a pending action from being taken.
Review completed actions
Go to the Microsoft Defender portal and sign in.
In the navigation pane, choose Action center.
Review the items on the History tab.
Select an item to view more details about that remediation action.
Undo completed actions
If you've determined that a device or a file is not a threat, you can undo remediation actions that were taken, whether those actions were taken automatically or manually. In the Action center, on the History tab, you can undo any of the following actions:
| Action source | Supported Actions |
|---|---|
|
|
Note
Defender for Endpoint Plan 1 and Microsoft Defender for Business include only the following manual response actions:
- Run antivirus scan
- Isolate device
- Stop and quarantine a file
- Add an indicator to block or allow a file
To undo multiple actions at one time
Go to the Action center (https://security.microsoft.com/action-center) and sign in.
On the History tab, select the actions that you want to undo. Make sure to select items that have the same Action type. A flyout pane opens.
In the flyout pane, select Undo.
To remove a file from quarantine across multiple devices
Go to the Action center (https://security.microsoft.com/action-center) and sign in.
On the History tab, select an item that has the Action type Quarantine file.
In the flyout pane, select Apply to X more instances of this file, and then select Undo.
Automation levels, automated investigation results, and resulting actions
Automation levels affect whether certain remediation actions are taken automatically or only upon approval. Sometimes your security operations team has more steps to take, depending on the results of an automated investigation. The following table summarizes automation levels, results of automated investigations, and what to do in each case.
| Device group setting | Automated investigation results | What to do |
|---|---|---|
| Full - remediate threats automatically (recommended) |
A verdict of Malicious is reached for a piece of evidence. Appropriate remediation actions are taken automatically. |
Review completed actions |
| Semi - require approval for any remediation | A verdict of either Malicious or Suspicious is reached for a piece of evidence. Remediation actions are pending approval to proceed. |
Approve (or reject) pending actions |
| Semi - require approval for core folders remediation | A verdict of Malicious is reached for a piece of evidence. If the artifact is a file or executable and is in an operating system directory, such as the Windows folder or the Program files folder, then remediation actions are pending approval. If the artifact is not in an operating system directory, remediation actions are taken automatically. |
|
| Semi - require approval for core folders remediation | A verdict of Suspicious is reached for a piece of evidence. Remediation actions are pending approval. |
Approve (or reject) pending actions. |
| Semi - require approval for non-temp folders remediation | A verdict of Malicious is reached for a piece of evidence. If the artifact is a file or executable that is not in a temporary folder, such as the user's downloads folder or temp folder, remediation actions are pending approval. If the artifact is a file or executable that is in a temporary folder, remediation actions are taken automatically. |
|
| Semi - require approval for non-temp folders remediation | A verdict of Suspicious is reached for a piece of evidence. Remediation actions are pending approval. |
Approve (or reject) pending actions |
| Any of the Full or Semi automation levels | A verdict of No threats found is reached for a piece of evidence. No remediation actions are taken, and no actions are pending approval. |
View details and results of automated investigations |
| No automated response (not recommended) | No automated investigations run, so no verdicts are reached, and no remediation actions are taken or awaiting approval. | Consider setting up or changing your device groups to use Full or Semi automation |
All verdicts are tracked in the Action center.
Note
In Defender for Business, automated investigation and remediation capabilities are preset to use Full - remediate threats automatically. These capabilities are applied to all devices by default.
Next steps
- Learn about live response capabilities
- Proactively hunt for threats with advanced hunting
- Address false positives/negatives in Microsoft Defender for Endpoint
See also
Tip
Do you want to learn more? Engage with the Microsoft Security community in our Tech Community: Microsoft Defender for Endpoint Tech Community.
Σχόλια
Σύντομα διαθέσιμα: Καθ' όλη τη διάρκεια του 2024 θα καταργήσουμε σταδιακά τα ζητήματα GitHub ως μηχανισμό ανάδρασης για το περιεχόμενο και θα το αντικαταστήσουμε με ένα νέο σύστημα ανάδρασης. Για περισσότερες πληροφορίες, ανατρέξτε στο θέμα: https://aka.ms/ContentUserFeedback.
Υποβολή και προβολή σχολίων για